
A new Android attack dubbed Pixnapping allows malicious apps to covertly capture sensitive data rendered on users' screens, including Signal messages, one-time 2FA codes, emails, location history, and financial information, without requiring a single permission.
The attack affects nearly all modern Android phones and leverages a combination of legitimate system APIs and a GPU hardware side channel to reconstruct displayed pixels with surprising precision.
Although Pixnapping is capable of targeting a wide range of apps and web content, its ability to extract private messages from Signal, an app prized for its privacy guarantees, adds a particularly jarring dimension. The exploit works even when Signal's Screen Security feature is enabled, which typically prevents screenshots or previews of chats.
Discovered by a coalition of researchers from Berkeley, Washington, UC San Diego, and CMU, Pixnapping will be formally presented at the 32nd ACM Conference on Computer and Communications Security (CCS 2025) in Taipei.
The researchers demonstrated successful attacks on recent Google Pixel phones (6 through 9) and the Samsung Galaxy S25. Their framework enables the unauthorized extraction of pixels rendered by both web pages and native apps, using a sequence of intent-based activity calls, transparent overlays, and GPU-accelerated timing measurements.
Pixnapping can target any screen content that is visible during app use. The researchers demonstrated attacks against:
- Signal: Private conversations were exfiltrated pixel-by-pixel, even bypassing its anti-screenshot protections.
- Google Authenticator: 6-digit TOTP codes were stolen in under 30 seconds using an optimized OCR-style attack, beating the standard 30-second expiry time.
- Google Maps: Full location history (Timeline) entries were reconstructed, a feature no longer accessible via the web due to privacy restrictions.
- Gmail and Google Accounts: Emails and account details, including full names and home addresses, were retrieved.
- Venmo: Account balances and transaction history were exposed.
- Google Messages: SMS content, including potential 2FA messages, was recoverable.
Unlike prior “pixel stealing” attacks that were limited to web content and mitigated by iframe restrictions or cross-site protections, Pixnapping sidesteps these entirely. It targets Android's system for launching app activities and manipulating rendering layers to coerce graphical operations on sensitive pixels.
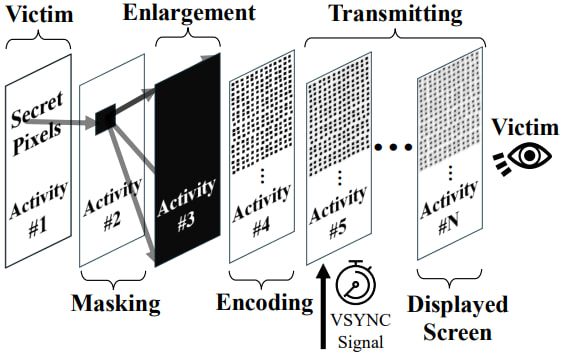
Pixnapping operates in three main stages:
- The attacker app silently launches the target activity (e.g., Signal chat window or Google Authenticator) using Android intents.
- It layers a semi-transparent blur effect to isolate and enlarge individual pixels of interest, a strategy that mimics convolution operations in image processing.
- It uses GPU rendering delays, specifically the GPU.zip side channel, to infer pixel color data, one pixel at a time.
pixnapping.com
This process effectively allows screen content to be reconstructed without ever taking a screenshot.
Crucially, the attacker app requires no declared permissions, making it indistinguishable from harmless apps in app stores or on-device security scans.
Google's response
Google initially patched the vulnerability in September 2025 and assigned it CVE-2025-48561. However, the research team soon found a working bypass. Google acknowledged the workaround as a high-severity issue and plans to roll out a second patch in the December 2025 Android security bulletin.
Samsung was notified in parallel and is also affected, though no mitigations have been confirmed for their devices.
The core enabler of Pixnapping, the GPU.zip side channel, remains unpatched by hardware vendors. This underlying issue is likely to persist until GPU manufacturers address data-dependent compression timing differences.
The researchers also discovered an app list bypass, a secondary vulnerability that allows an attacker to determine which apps are installed on a device without declaring any special permissions. Google has opted not to fix this, citing feasibility concerns.







Leave a Reply