A recent study from researchers at top U.S. universities as well as Google, reveals vulnerabilities in the conditional branch predictors of modern CPUs that could let attackers read and manipulate the path history register (PHR) and prediction history tables (PHTs). This exploit, dubbed “Pathfinder”, leads to two new classes of attacks that could severely compromise data security.
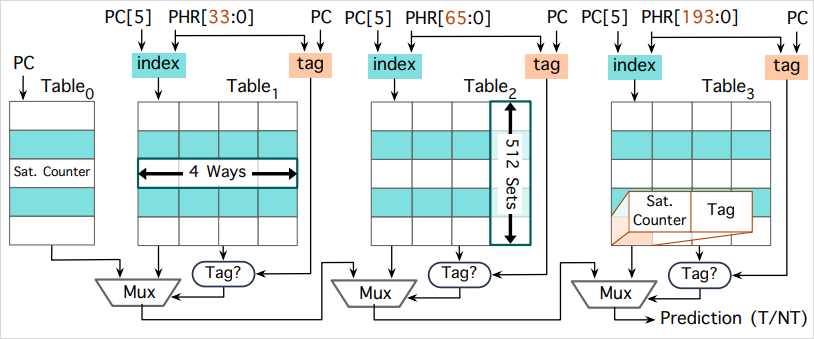
The Pathfinder class of attacks was enabled by deeper understanding of CPU branch predictors, specifically the conditional branch predictor (CBP). The research builds upon the known Spectre v1 vulnerabilities but exploits the CBP in more sophisticated ways. Previously unknown internal structures and behaviors of the CBP were fully mapped, revealing how specific manipulations of the PHR and PHTs can lead to significant security breaches.
pathfinder.cpusec.org
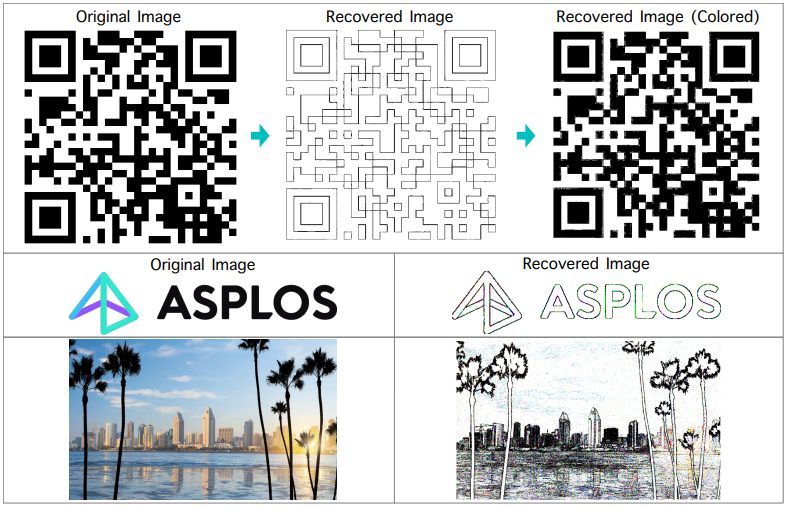
The attack can capture detailed branch execution paths of any program, revealing how the program operates on a step-by-step basis. This capability was demonstrated by successfully recovering the complete control flow of the libjpeg routines, revealing sensitive image data through the precise branch flow history.
By manipulating the PHR and PHTs, attackers can induce erroneous executions that could, for instance, allow them to extract encryption keys from secure cryptographic algorithms like AES. This is done by forcing the algorithm to mispredict branches, thereby leaking intermediate computation states.
The researchers successfully demonstrated a practical secret-image recovery attack using Pathfinder. They exploited the read primitives of the attack to capture the entire control flow of image processing routines in the libjpeg library, a widely used library for handling JPEG images. By capturing the control flow, they could deduce which parts of an image were processed in certain ways, effectively allowing them to reconstruct the image or significant parts of it.
Another demonstration involved a key recovery attack against the AES (Advanced Encryption Standard) cryptographic algorithm. The researchers showed that by using write primitives to manipulate the path history register, they could induce specific mispredictions in the execution of AES. This allowed them to observe intermediate values of the encryption process, leading to the recovery of the encryption key.
Industry response
Intel has acknowledged the findings but stated that the issues highlighted in “Pathfinder” do not introduce new practical security concerns beyond those already addressed by existing mitigations for Spectre Variant 1. They recommend reviewing their existing guidelines on bounds check bypass and timing side channels.
AMD notes that while the paper focuses on Intel CPUs, no exploit against AMD products has been demonstrated. However, they recommend following previously published guidance regarding Spectre-like attacks.
Though Pathfinder can have significant implications for user privacy and security, it's a very sophisticated attack that requires significant technical expertise to carry out.
While users themselves may not be able to prevent such sophisticated attacks directly, they can adopt several practices and advocate for system-level changes to reduce their risk, including keeping their systems updated, only using software from trusted sources, and enabling hardware-based security extensions like Intel SGX.







Leave a Reply