
A newly disclosed security vulnerability dubbed the Opossum attack allows attackers in a man-in-the-middle (MitM) position to desynchronize secure communications over TLS in widely used protocols like HTTP, SMTP, POP3, and FTP.
Discovered by a team of researchers from the Technology Innovation Institute, Ruhr University Bochum, and Paderborn University, the Opossum attack undermines fundamental TLS guarantees of channel integrity without requiring software bugs or broken cryptography.
The attack was detailed in a research paper published by Robert Merget, Nurullah Erinola, Marcel Maehren, Lukas Knittel, Sven Hebrok, Marcus Brinkmann, Juraj Somorovsky, and Jörg Schwenk. Building on earlier findings from the ALPACA attack (2021), the team explored how servers that support both implicit TLS (starting encryption from the beginning of the connection) and opportunistic TLS (upgrading plaintext connections to TLS mid-session) can be exploited due to subtle mismatches in protocol behavior.
The core weakness lies in how TLS is integrated into application protocols. When a server supports both TLS modes simultaneously, attackers can exploit discrepancies in the initial message exchange after the TLS handshake. For example, in HTTP, implicit TLS expects the client to send the first message post-handshake, whereas opportunistic TLS expects the server to respond first. By intercepting and re-routing client connections, attackers can craft situations where clients and servers operate under mismatched assumptions leading to persistent desynchronization.
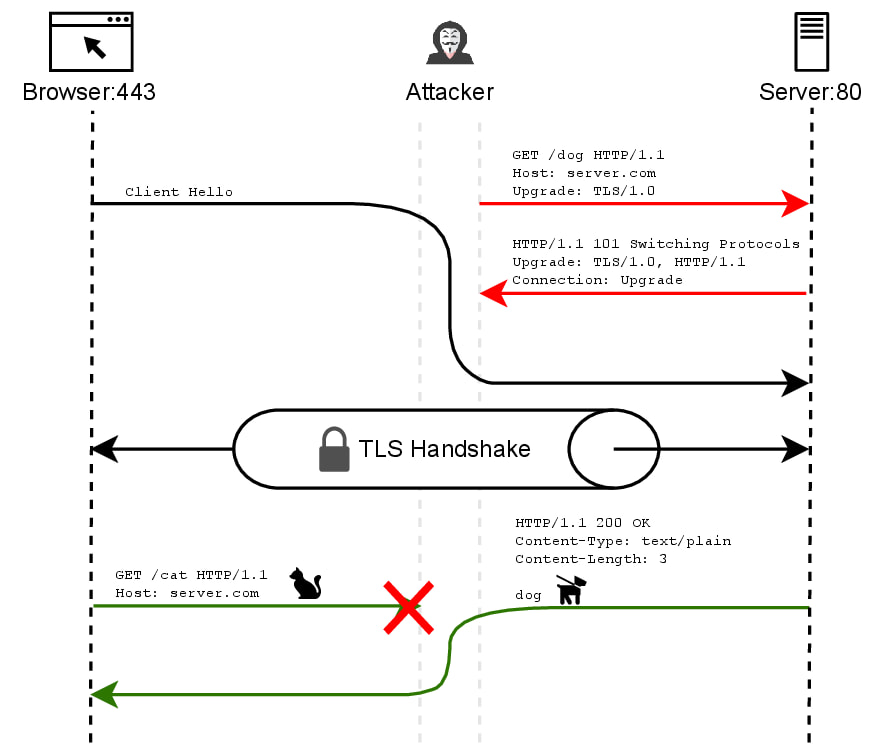
In practical terms, an attacker can inject crafted HTTP requests into the connection, resulting in a client receiving a response intended for a different request. Proof-of-concept (PoC) exploits shared by the researchers demonstrate several attack classes against HTTPS:
- Resource Confusion: Users may be served the wrong content (e.g., fetching /cat returns /dog).
- Session Fixation: Attackers can log victims into attacker-controlled sessions.
- Reflected XSS Escalation: Self-XSS flaws can be amplified into full XSS exploits.
- Request Smuggling: Desynchronized request bodies can leak cookies or trigger unauthorized actions.
A released PoC involves Apache 2.4.62 servers misinterpreting POST request bodies due to the TLS upgrade mechanism, resulting in cookie leaks and session hijacking.
The research team identified over 3 million hosts supporting both TLS variants, making them theoretically vulnerable. While HTTP servers supporting RFC 2817's TLS upgrade mechanism are rare, legacy systems like CUPS, Icecast, and Cyrus IMAP remain susceptible. Despite the limited real-world impact today, the attack presents a clear warning for future protocol designs and existing deployments.
Affected systems include not only web servers but also email and file transfer services using STARTTLS. The vulnerability is tracked as CVE-2025-49812, and mitigation steps include disabling opportunistic TLS (e.g., STARTTLS or HTTP TLS upgrades) and enforcing strict separation of implicit and opportunistic TLS ports. Also, implementing distinct ALPN identifiers for different TLS modes (currently lacking standard support) is also effective in mitigating the issue.
Following the disclosure of the team's findings, vendors have started taking action. The Apache Foundation plans to deprecate RFC 2817 support, Cyrus IMAP has changed its default to implicit TLS, and patches are underway for CUPS and Icecast.
Administrators are urged to audit their services for dual TLS support and disable opportunistic modes wherever possible. While modern web browsers do not support HTTP TLS upgrades, many server-side applications still expose this legacy functionality, making vigilance and prompt configuration updates essential to prevent desynchronization exploits, such as Opossum.







Leave a Reply