
Cisco Talos has uncovered a destructive malware dubbed Numero, a Windows-targeting threat that disguises itself as a legitimate AI video tool installer but ultimately renders victims’ systems unusable.
Alongside Numero, Talos also discovered two ransomware families, CyberLock and Lucky_Gh0$t, spreading under the guise of AI software, all part of a rising wave of cyberattacks exploiting AI’s surging popularity.
The discovery stems from Talos’ recent investigations into malware campaigns using fake AI tool installers. These campaigns leverage SEO poisoning, Telegram channels, and social media platforms to lure victims searching for AI solutions into downloading infected software bundles. The attackers’ targets include businesses across marketing, technology, and B2B sales sectors, which are increasingly adopting AI-driven tools for automation and content generation.
Corrupting Windows from the inside
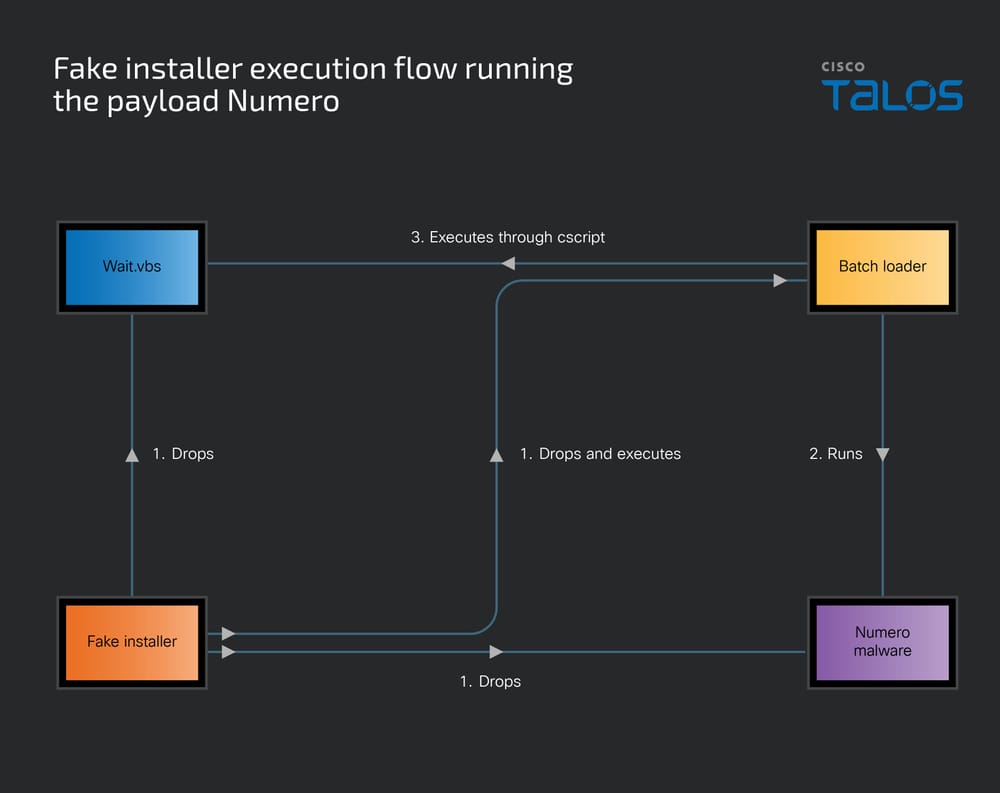
Numero poses as the installer for InVideo AI, a popular online platform used to create marketing videos, social media content, and presentations. Once the victim runs the fake installer, a dropper package unpacks several malicious components, including a malicious batch file, a VB script, and the Numero executable (wintitle.exe).
These components are dropped into the user’s application temp folder. The batch file then launches Numero in an infinite loop, executing the malware, pausing briefly, terminating it, and restarting the cycle.
Cisco Talos
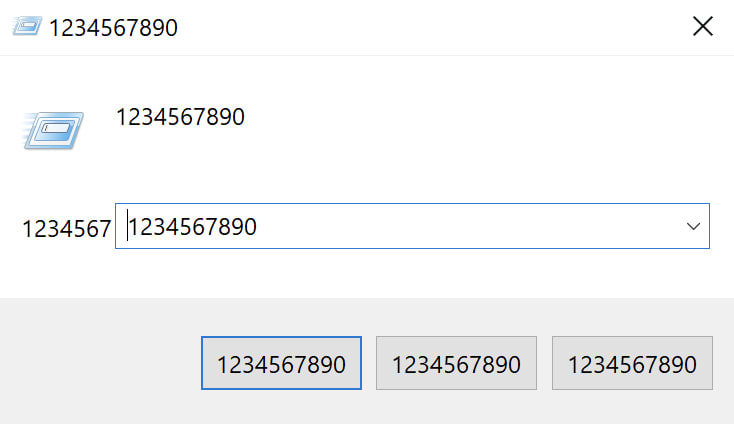
Numero is designed to evade detection by checking for common debugging tools like IDA, x64dbg, OllyDbg, and Windbg. Once active, it hijacks the Windows graphical user interface (GUI), interacting directly with the desktop window using Windows API calls (GetDesktopWindow, EnumChildWindows, SendMessageW). It hooks into child windows and overwrites window titles, buttons, and contents with repetitive numeric strings like 1234567890.
Cisco Talos
This constant manipulation leads to severe corruption of the GUI, making everyday system operations impossible. For victims, the result is a machine that cannot be used, even though files and applications may technically remain intact.
More AI-masked threats
While Numero stands out for its destructive, non-financial intent, Talos also highlighted ransomware operations using similar AI lures to spread their payloads to unsuspecting victims.
CyberLock, a PowerShell-based ransomware embedded in a fake NovaLeadsAI installer, encrypts files across several categories (documents, images, archives, executables) and appends .cyberlock extensions. It demands $50,000 in Monero (XMR) and falsely claims that ransom funds will support humanitarian aid.
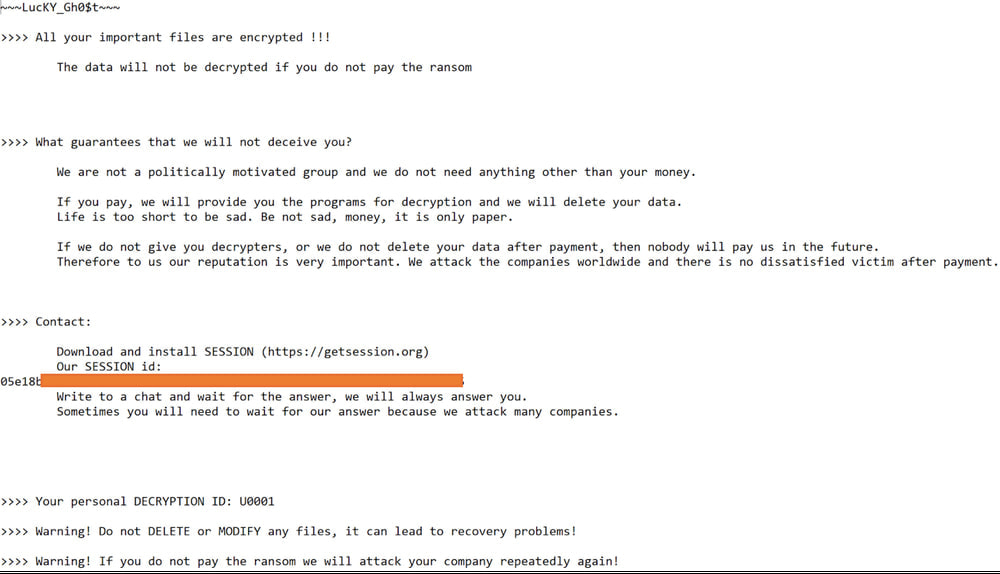
Lucky_Gh0$t, a variant of the Yashma ransomware family, hides inside a fake ChatGPT 4.0 Premium installer. It encrypts files smaller than 1.2 GB and destroys larger files by replacing their contents with single characters. Victims are instructed to contact the attacker through the Getsession secure messenger platform.
Cisco Talos
To protect against threats like Numero, it is recommended to only download software from verified, official sources, avoid clicking on promoted results, and be aware of the dangers of SEO poisoning.







Leave a Reply