
A newly discovered malware suite for macOS, dubbed PasivRobber, appears to be a highly advanced surveillance framework with links to Chinese tech firms known for developing government surveillance tools.
First unearthed on March 13, 2025, by Kandji researchers, the toolset showcases a deep technical understanding of macOS internals and targets applications popular among Chinese users.
Targeting communication data
The initial discovery occurred when the researchers found a suspicious Mach-O binary named wsus on VirusTotal. A deeper investigation revealed a broader malware ecosystem made up of over 20 binaries and dynamic libraries. These components were designed to steal data from widely used apps such as WeChat, QQ, email clients, and web browsers. The suite uses a LaunchDaemon to establish persistence, employs naming obfuscation to evade detection, and installs additional payloads based on the system version and CPU architecture.
The main binary, goed, is deceptively named to resemble Apple's legitimate geod daemon and triggers the execution of wsus. This, in turn, manages remote communications via FTP and RPC, orchestrates plugin execution, and can uninstall itself to evade forensic review. The malware's depth — extending to the use of encrypted .ini files, Protobuf-based RPC communication, and a plugin system — suggests capabilities on par with state-sponsored spyware.
At the heart of PasivRobber lies a collection of modules for credential theft, system monitoring, screenshot capture, and app injection. Notably, a binary named center acts as a local agent, managing surveillance activities and maintaining communication with a remote server. It captures system data using shell commands and sysctl, logs user behavior, and uses injected dynamic libraries to extract instant messaging keys. Libraries like libIMKeyTool.dylib, libQQRobber.dylib, and libWXRobber.dylib specifically target WeChat, QQ, and Enterprise WeChat, using embedded Frida scripts to hook into running processes.
These components are supported by 28 plugin modules — disguised as .gz files — that collect and store user data in SQLite databases. The suite appears to dynamically tailor its behavior based on the system and apps present, with signs of compatibility checks for specific app versions and macOS builds. It even performs a System Integrity Protection (SIP) check to enable deeper system access where possible.
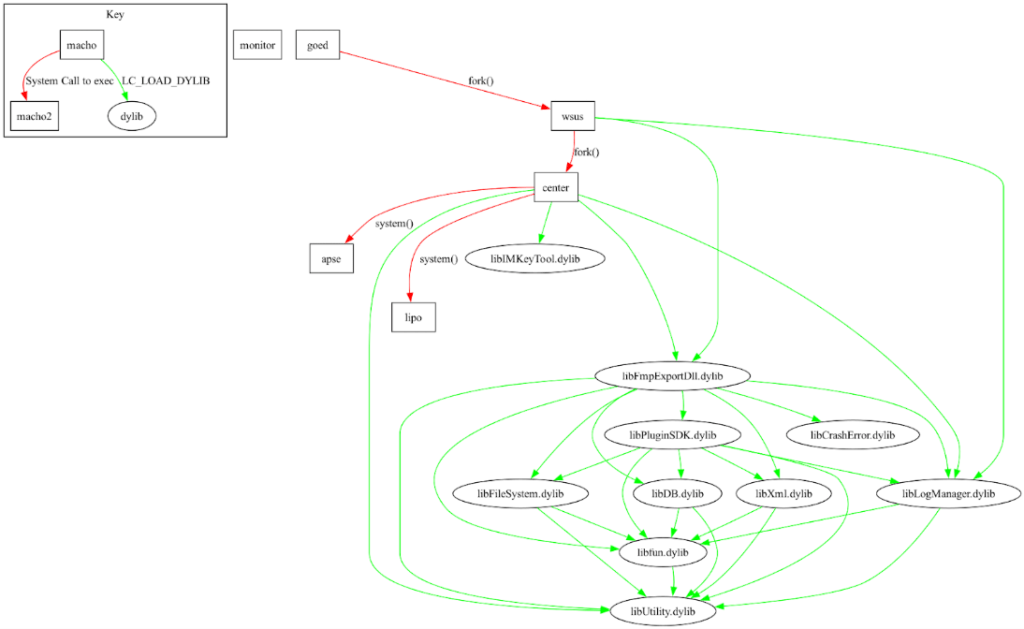
Kandji
State-sponsored surveillance
Open-source intelligence (OSINT) analysis by the researchers connects the malware to a developer identity named “weihu chen” and the directory path name “Meiya.” These identifiers link back to the Chinese firm Xiamen Huanya Zhongzhi Technology Partnership Enterprise, which holds shares in Xiamen Meiya Yian Information Technology Co, itself affiliated with Meiya Pico. According to the U.S. Treasury, Meiya Pico operates in China's surveillance technology sector and has developed software tools reportedly used in state-backed monitoring programs, including tools deployed in Xinjiang.
Meiya Pico is a significant entity in China's surveillance technology landscape, with known products for forensic analysis and mass data collection. The potential overlap in developer identifiers, functionality, and target demographics lends credence to the hypothesis that PasivRobber may be a macOS adaptation of tools previously attributed to the firm or its affiliates.
The discovered suite even includes a Windows component, though the analysis focused exclusively on the macOS variant. The researchers note the inclusion of Windows install scripts and executables that suggest this tool is part of a cross-platform surveillance effort.
Defense recommendations
Given PasivRobber's sophistication, detecting and mitigating it requires more than typical endpoint protections. Organizations and individuals using macOS — especially within high-risk sectors or regions — should consider the following:
- Inspect LaunchDaemons and suspiciously named services, such as com.apple.goed, for persistence mechanisms.
- Enable and enforce System Integrity Protection (SIP) to prevent unauthorized dylib injections.
- Monitor file system paths like /Library/protect/ and /usr/local/lib/ for unrecognized binaries and libraries.
- Use behavioral EDR tools that can detect inter-process execution chains and Frida-based memory hooks.
- Analyze outgoing network connections, particularly to unknown FTP servers, and block suspicious RPC calls.
- Harden application permissions to prevent injection into messaging and communication software.
As this toolkit targets widely used messaging apps and disguises itself effectively within the macOS ecosystem, users should remain vigilant and perform regular audits of background services and third-party installations. The research team anticipates further analysis and updates as more artifacts are uncovered.







Leave a Reply