
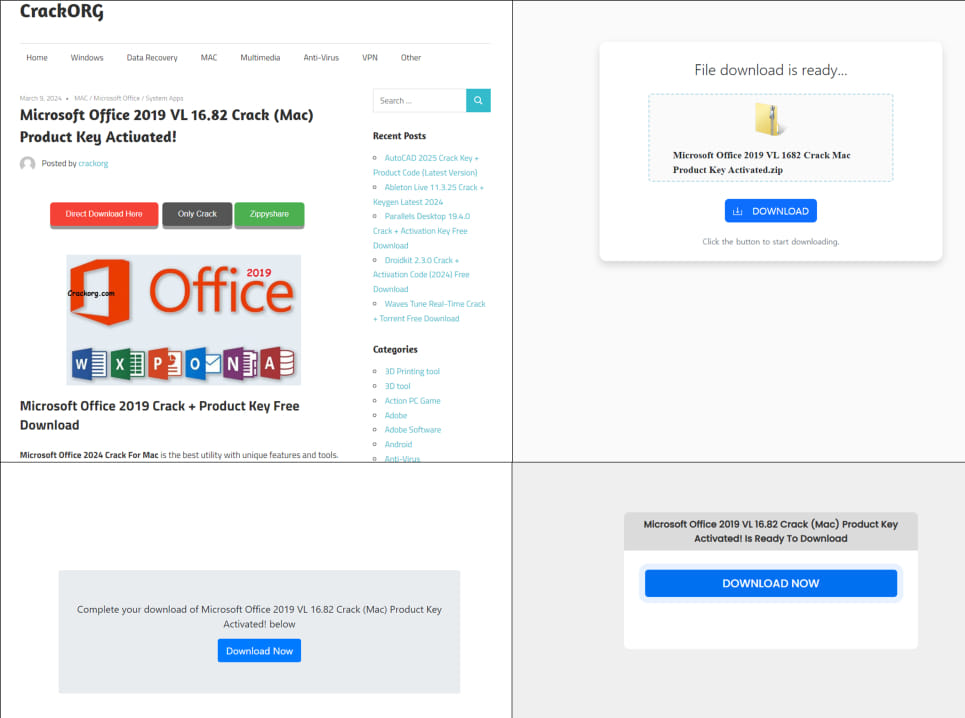
AhnLab Security Intelligence Center (ASEC) has uncovered a new malware strain dubbed “InnoLoader,” which disguises itself as software cracks and commercial tools.
ASEC's research indicates that the malware is generated dynamically upon each download request, creating a unique file with the same malicious functions but different hash values every time. This method allows the malware to evade detection by traditional security measures that rely on hash-based identification.
ASEC
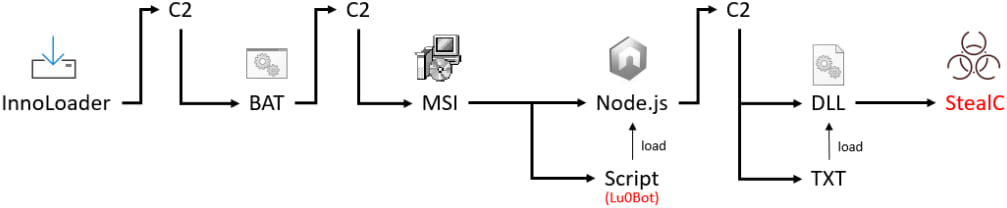
The malware communicates with a command-and-control (C2) server, downloading and executing files based on the server's responses. Analysis revealed the installation of various malicious components, including:
- Infostealer StealC: Gathers sensitive user information such as passwords, cryptocurrency wallet credentials, and FTP login data.
- Socks5Systemz: Converts the infected system into a proxy server for commercial purposes.
- Clicker: A browser plugin that inflates web page views.
Additionally, legitimate software like the Opera browser and 360 Security products were occasionally installed to obfuscate the malware's true nature and hinder tracking and analysis efforts.
Technical details
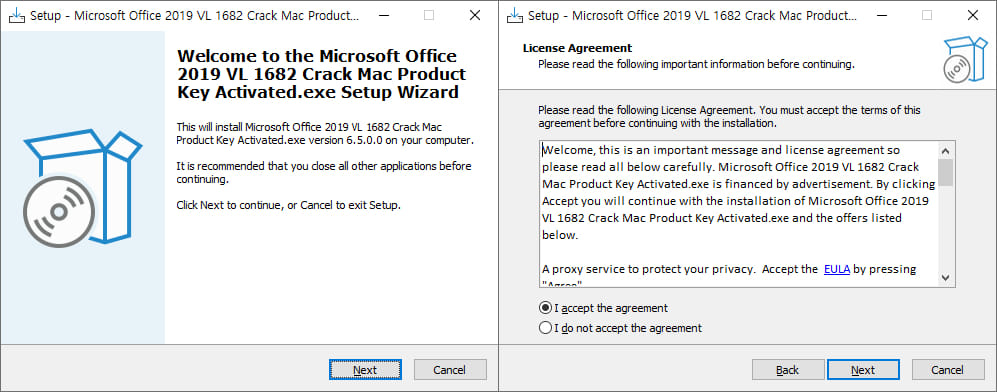
The InnoLoader malware is crafted using the InnoSetup installer framework. When executed, it presents a standard installation interface, and malicious activities are triggered by normally interacting with the installer buttons, clicking ‘Next' twice. The use of the InnoDownloadPlugin enables the malware to connect to an external network to fetch additional malicious payloads.
ASEC
Upon the first connection to the C2 server, if the response is “ok,” the malware proceeds to download and execute files from a specified URL. This process repeats across multiple C2 URLs, leading to the execution of both benign and malicious files.
The malware employs several techniques to evade detection and analysis. For instance, in environments where a download has previously occurred, a legitimate WinRAR installation file is served instead of the malware. This tactic disrupts tracking and forensic efforts.
InnoLoader also uses the Lu0Bot malware, which communicates via UDP and can execute commands, collect system information, and maintain persistence by copying itself to the ProgramData directory and creating shortcuts in the Startup folder. Lu0Bot was observed downloading and executing StealC, further complicating the infection chain.
ASEC
Defense recommendations
Given the evasive nature of the InnoLoader malware, users are advised to:
- Avoid downloading and executing files from untrusted sources.
- Maintain updated security software to detect and block known threats.
- Regularly update all software to mitigate vulnerabilities that could be exploited by malware.







Leave a Reply