
Dragos has unveiled “FrostyGoop,” the latest industrial control systems (ICS) malware utilizing Modbus TCP communications to disrupt operational technology (OT). Discovered in April 2024, FrostyGoop represents a significant threat to critical infrastructure, emphasizing the need for heightened cybersecurity measures.
Dragos first identified the FrostyGoop malware during a routine investigation of suspicious files. Written in Golang and designed for Windows systems, FrostyGoop interacts directly with ICS using the Modbus TCP protocol over port 502. Despite its capability to read and write data on ICS devices, antivirus vendors have not detected it as malicious.
The Lviv incident
Ukraine's Cyber Security Situation Center (CSSC) collaborated with Dragos, sharing insights into a cyberattack on a district energy company in Lviv. In January 2024, adversaries used FrostyGoop to send Modbus commands to ENCO controllers, disrupting heating services for over 600 apartment buildings amid sub-zero temperatures.
The attack lasted nearly two days, highlighting the malware's ability to cause significant operational disruptions.
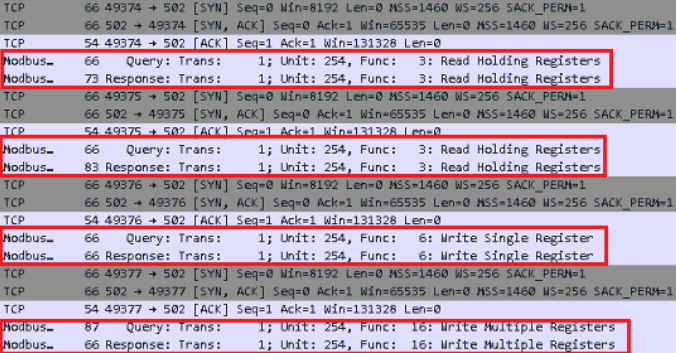
Technical details
FrostyGoop's capabilities include:
- Accepting command line execution arguments
- Utilizing JSON configuration files to specify target IP addresses and Modbus commands
- Logging output to a console or JSON file
- Sending Modbus commands to read or modify data on ICS devices
The malware's command execution flexibility, combined with its undetectable nature, underscores its potential danger. Dragos found configuration files linked to ENCO control devices, indicating the malware's broader applicability.
Dragos
Impact and broader implications
The discovery of FrostyGoop raises concerns about its potential to disrupt critical infrastructure across multiple sectors. Modbus, a widely used communication protocol in industrial environments, is embedded in both legacy and modern systems, making FrostyGoop a versatile threat. The Lviv incident exemplifies the severe consequences of such vulnerabilities, emphasizing the need for robust security measures.
To mitigate the risks posed by FrostyGoop, Dragos recommends that system administrators implement the following critical controls:
- Develop specialized response plans for OT environments, focusing on quick isolation and analysis of unauthorized Modbus commands.
- Ensure proper network segmentation and avoid exposing critical controllers to the internet.
- Employ protocol-aware monitoring tools to detect anomalies in Modbus traffic.
- Enforce multi-factor authentication, log and monitor remote connections, and use VPNs.
- Conduct regular assessments to identify and address vulnerabilities, especially those exploitable over the network.
The emergence of FrostyGoop highlights the urgent need for enhanced cybersecurity in OT environments. The malware's ability to interact with ICS devices undetected poses a significant threat, as demonstrated by the attack in Lviv.







Leave a Reply