
Aqua Nautilus researchers have uncovered a new variant of the Gafgyt botnet that extends its reach beyond typical IoT devices, now targeting more powerful servers within cloud-native environments.
This variant, leveraging weak SSH passwords, is designed to infiltrate systems, expand the botnet, and harness GPU power for cryptocurrency mining, representing a significant shift in Gafgyt's operational focus.
Brief history of Gafgyt
Originally known as Bashlite or Lizkebab, Gafgyt emerged around 2014 as malware primarily targeting Internet of Things (IoT) devices, such as routers and cameras. By exploiting weak or default credentials, Gafgyt would integrate these devices into a botnet, commonly used to launch distributed denial-of-service (DDoS) attacks.
Over the years, the malware has evolved through various iterations, with its source code being leaked, leading to numerous variants that complicate cybersecurity defenses.
Attack flow
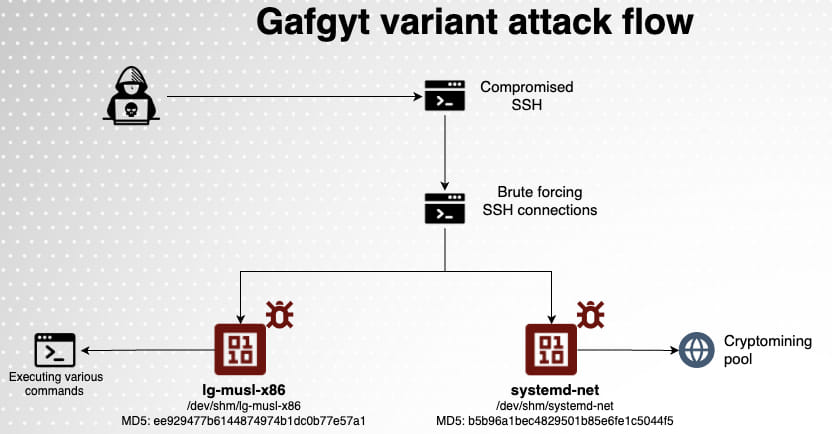
In this latest campaign, attackers gained initial access through brute-force attacks on weakly secured SSH services. Once access was secured, they executed commands to inspect the server, transferred two primary payloads, and then initiated the deployment of a cryptominer, specifically XMRIG, which mines Monero cryptocurrency using the server's GPU power.
The payloads included an SSH scanner named “ld-musl-x86” and a cryptominer disguised as “systemd-net.” These binaries were executed directly from memory to avoid detection, with “ld-musl-x86” handling the propagation of the botnet by scanning for more vulnerable systems, while “systemd-net” managed the cryptocurrency mining operations.
The malware also included functions to eliminate competing malware, modify system configurations, and erase history and log files, further obscuring its presence.
Targeting cloud-native environments
This new variant's focus on cloud-native environments marks a notable departure from traditional Gafgyt operations. The malware's binary names, “ld-musl-x86” and “systemd-net,” are cleverly disguised as legitimate Linux components, highlighting the threat actors' efforts to evade detection. Additionally, the use of the flags –cuda and –opencl in the cryptomining process indicates a deliberate intent to exploit the GPU power typically found in more robust server environments rather than low-power IoT devices.
An analysis of the brute force configuration file, containing 179 sets of usernames and passwords, revealed a broad range of potential targets, including cloud-native infrastructure like Hadoop, AWS, and Azure, alongside more traditional IoT devices and gaming servers. This diverse target list underscores the variant's capability to compromise a wide array of systems across different sectors.
Exposure and protection
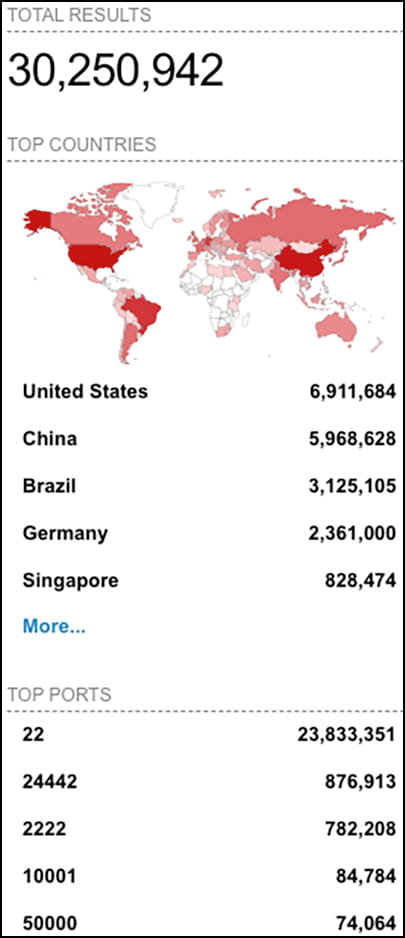
Shodan, the search engine for Internet-connected devices, identified over 30 million SSH instances exposed to the internet, underscoring the critical need for securing SSH services against brute-force attacks such as those employed by Gafgyt.
Aqua Nautilus
Aqua Nautilus‘ advanced Runtime Protection solution was instrumental in detecting and analyzing this attack in real-time. The platform identified malicious behaviors, such as fileless execution and cryptomining activities, with precise alerts that enabled timely response and mitigation.
To defend against this evolving threat, organizations should:
- Use complex passwords or, ideally, switch to RSA keys for SSH authentication.
- Implement advanced threat detection solutions capable of identifying suspicious behaviors in real-time.
- Ensure that all devices, especially those exposed to the internet, are regularly updated and patched to prevent exploitation of known vulnerabilities.
- Limit SSH access to trusted IP addresses and use two-factor authentication where possible.







Leave a Reply