
ESET researchers have uncovered a novel Android malware named “NGate,” targeting banking clients in Czechia, marking the first known instance of malware that relays NFC traffic to facilitate unauthorized cash withdrawals.
This malicious operation, active since November 2023, initially employed Progressive Web Apps (PWAs) and WebAPKs before advancing to the deployment of NGate, which exploits NFC technology in a unique and alarming way.
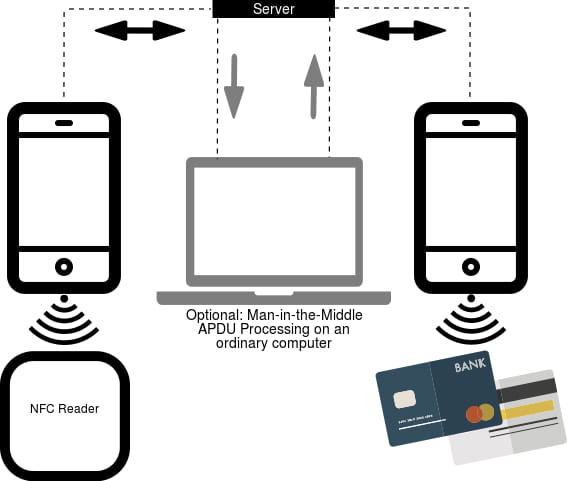
The NGate malware operates by cloning NFC data from victims' payment cards via compromised Android devices. This data is then relayed to an attacker's rooted Android phone, enabling them to emulate the victim's card and withdraw cash from ATMs. The malware's functionality is rooted in NFCGate, an open-source tool originally designed by students at the Technical University of Darmstadt, which has now been repurposed for this criminal activity.
ESET
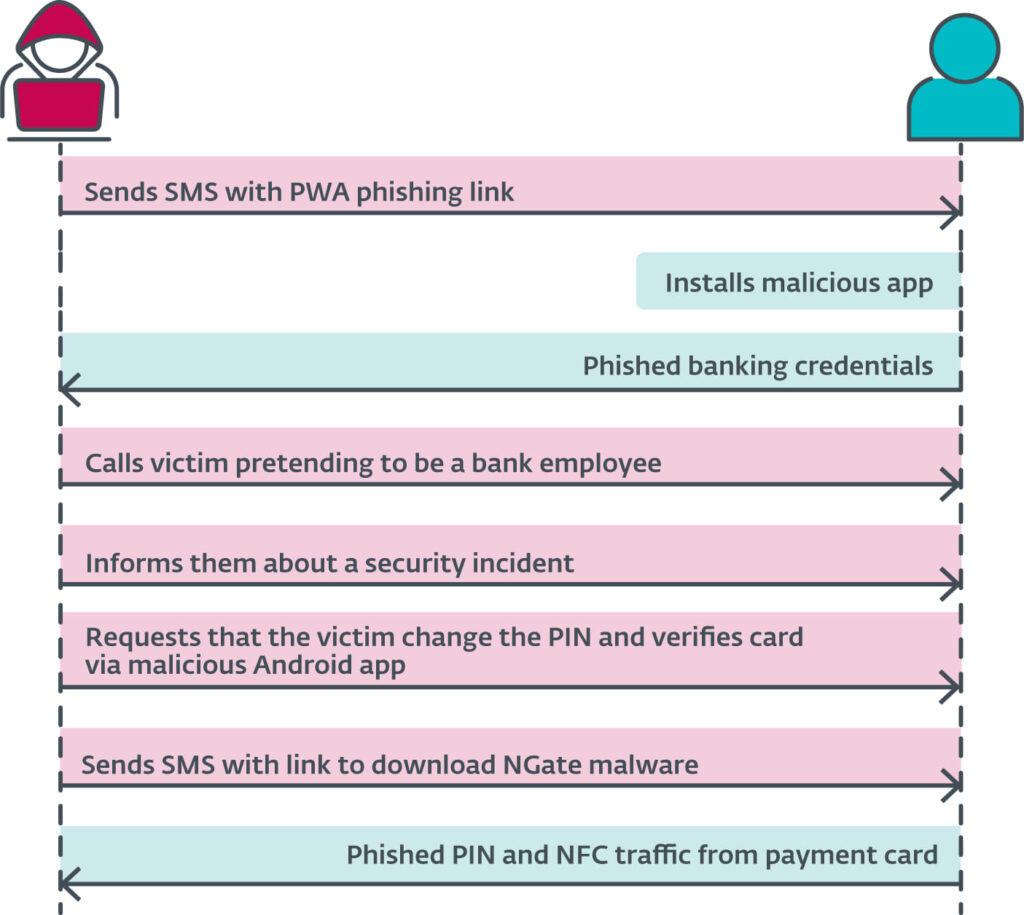
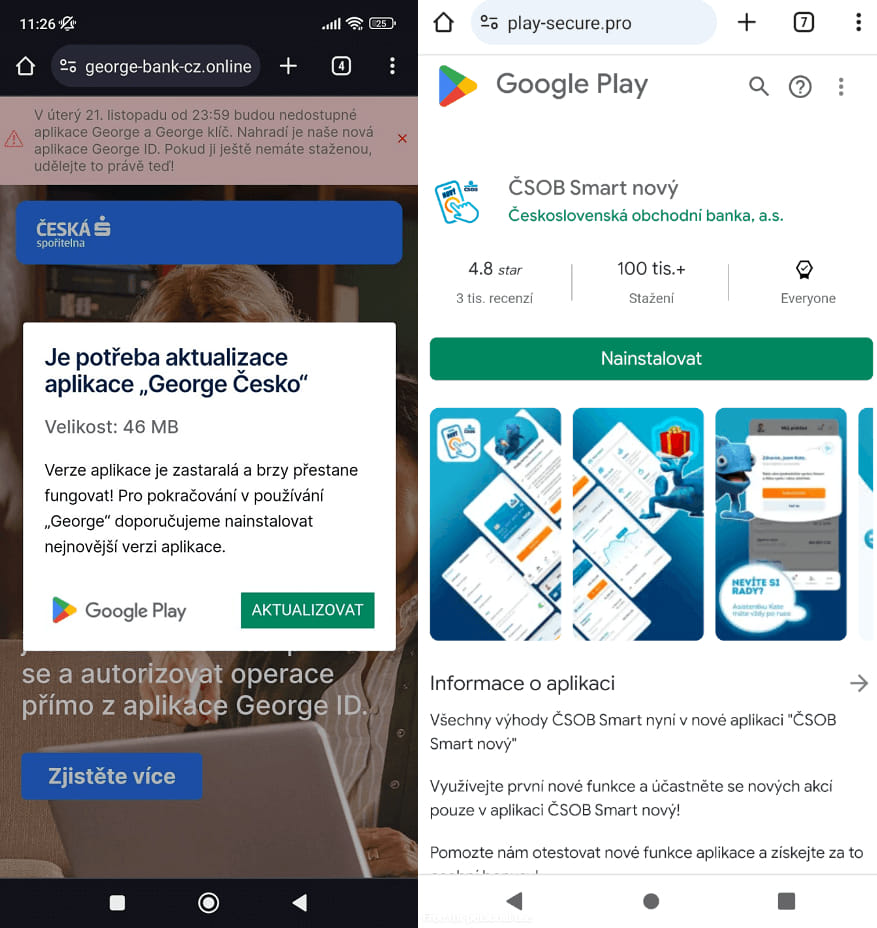
Victims were lured into installing the malware through deceptive SMS messages masquerading as communications from legitimate banks, a tactic reported by ESET in their recent research. These messages often contained links to phishing websites that mimicked official banking platforms, tricking users into downloading malicious apps under the guise of a tax refund or urgent banking alert.
ESET
This campaign, targeting clients of three major Czech banks, came under scrutiny following the arrest of a suspect in Prague in March 2024. The individual was caught with over 160,000 Czech korunas (approximately $6,500), believed to be stolen from just three victims, indicating the potentially vast scope of the operation.
The NGate campaign evolved from earlier methods that leveraged PWAs and WebAPKs, which allowed attackers to bypass traditional security measures on Android and iOS devices. As we reported yesterday, these tactics were first observed in phishing campaigns in Poland and later spread to Czechia, further emphasizing the growing sophistication of mobile-based cyber threats. The use of PWAs, which are typically benign web apps, and WebAPKs, which integrate these apps into the Android ecosystem, made the phishing apps appear almost identical to legitimate banking apps, complicating detection.
ESET
ESET’s findings highlight a significant shift in the tactics of cybercriminals, moving from basic phishing methods to more complex strategies involving NFC technology. The ability of NGate to relay NFC data represents a new frontier in mobile malware, with potential implications for similar attacks beyond Czechia.
To protect against such sophisticated threats, users are advised to follow several precautionary measures:
- Verify the authenticity of websites before entering any sensitive information.
- Download apps exclusively from official app stores like Google Play.
- Keep payment card PINs confidential and be cautious of unsolicited SMS messages claiming to be from banks.
- Utilize security apps that can detect and block malware, and disable NFC on mobile devices when not in use.
- Consider using protective RFID cases for payment cards to prevent unauthorized scans.







I’m not surprised by this.
I recently bought a Motorola 5G phone and was taken aback to find that NFC payments via Google Wallet were always active, with no option to manually authorize or confirm transactions. During my initial use, I had to turn off NFC and re-enable it whenever I wanted to make a purchase. In contrast, with an iPhone, I can configure the settings so that a PIN or Face ID is required before an NFC payment is processed. Additionally, Face ID only works if I’m in the Apple Wallet app at the time.
In other words, with Android, just walking by an NFC point-of-sale terminal could trigger a payment. This seems to be a vulnerability that could potentially be exploited by hackers to initiate payments when they are close to you.
I returned back the Motorola and I’m staying with Apple