
A new academic study demonstrates that even subtle sounds emitted by a computer mouse can leak sensitive information.
Researchers from the University of Padua, TU Delft, and UC Irvine have shown that acoustic side-channel attacks (ASCAs) targeting mouse movements are feasible and pose real security risks.
The research team designed a series of experiments to test whether mouse movement sounds could be captured and analyzed to infer user activity. While keyboard acoustic attacks are a well-established domain, this study is the first to systematically explore the threat surface associated with mouse usage.
Tracking mouse movements
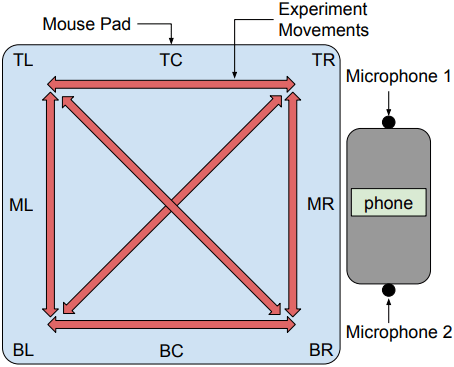
The research began with a controlled experiment where four basic mouse movements — up, down, left, and right — were recorded using a single microphone. Using machine learning techniques and Mel-Frequency Cepstral Coefficients (MFCCs) to process the audio, the team trained a convolutional neural network (CNN) to classify movements with 98% accuracy.
In a more complex setup, they recorded mouse movements in real time without pre-defined patterns and achieved 70% classification accuracy, which improved to 83% using a pipeline of normalization, PCA, and SVM. However, attempts to increase movement granularity to eight directions failed due to the limitations of a single microphone setup.
To overcome this, researchers introduced dual-microphone recordings using a smartphone’s stereo mic array. This two-dimensional audio capture enabled the successful classification of ten distinct mouse movement trajectories with 95% accuracy using a Random Forest classifier.
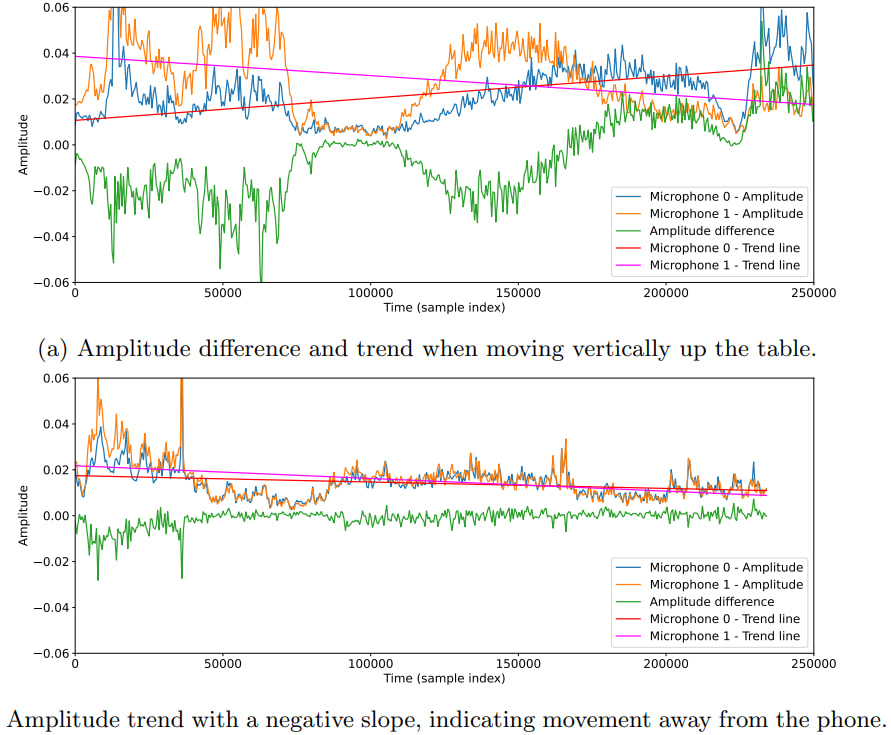
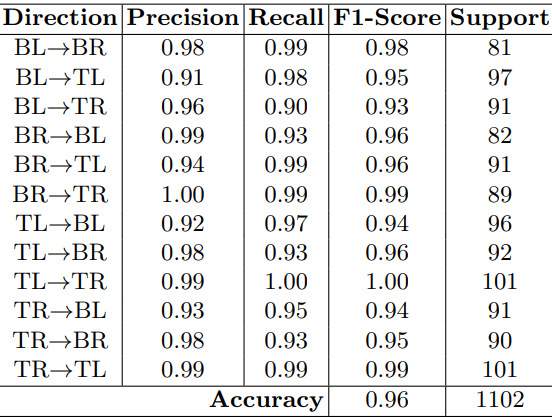
Moving beyond lab conditions, the researchers conducted real-world tests involving six participants. Each was asked to perform twelve directional mouse movements in a standard office setting. Despite differences in speed, pressure, and technique among participants, the model maintained a high accuracy rate of 96%.
arxiv.org
The team also evaluated whether such an attack could detect specific user actions — namely, closing a window by clicking the red “X” at the top-right corner of the screen. A binary classifier trained on mouse click acoustics achieved 91% accuracy in identifying this action from background noise, showing the practicality of ASCAs in monitoring user behavior with high precision.
The attack model requires nothing more than a smartphone placed unobtrusively near the victim. Modern smartphones, equipped with stereo microphones, can record acoustic signals from mouse movements without user awareness. The recorded sounds can then be analyzed offline using relatively simple ML pipelines.
arxiv.org
The potential threat is significant. If mouse movement data can be reliably interpreted, it could be combined with keyboard ASCAs to reconstruct sensitive tasks — such as filling out financial forms or submitting personal data. Though not pixel-accurate, the inferred trajectories and interaction patterns could betray the user’s intentions or actions.
Defense measures
To mitigate this emerging threat, users and organizations can consider:
- Microphone control: Limit or disable microphone access for untrusted apps and devices near sensitive workstations.
- Noise masking: Deploy white noise generators or software-based audio masking to obscure peripheral sounds.
- Hardware design: Encourage manufacturers to develop quieter mouse hardware or explore dampening materials in peripheral devices.
- Physical distancing: Maintain greater distance between untrusted devices and user input areas.
The researchers emphasize that this work is exploratory, yet it uncovers an underappreciated risk vector in everyday computing environments. Further research is needed to assess the full scope of mouse-based acoustic side channels, especially when combined with existing keyboard eavesdropping techniques.







Leave a Reply