
Privacy-focused VPN provider Mullvad has released version 2 of its Defense Against AI-guided Traffic Analysis (DAITA), introducing major technical upgrades aimed at improving both user performance and resistance to machine-learning-based traffic fingerprinting.
Mullvad is a Sweden-based VPN provider known for its staunch stance on privacy, refusal to collect user data, and support for open-source initiatives. Unlike many VPN companies, it does not require an email address or personal information to sign up, and it has gained credibility through repeated security audits and transparency efforts.
DAITA represents Mullvad's response to growing concerns about advanced traffic analysis. Traditional VPN encryption protects the content of communication, but it does not shield metadata such as packet timing, size, and direction — information that can be exploited by AI models to infer user behavior. DAITA, particularly in its latest form, is among the first production-ready countermeasures designed specifically to disrupt such analysis at scale.
DAITA v2 is now available across all supported platforms, replacing the original version launched in 2023. The key enhancements include a significant reduction in bandwidth overhead and the introduction of dynamic, per-session VPN tunnel configurations. The update builds on collaborative research led by Tobias Pulls, a researcher at Karlstad University, who has worked closely with Mullvad on refining the DAITA system.
Addressing AI-powered traffic analysis
DAITA was developed to mitigate the threat of AI-powered traffic analysis, where adversaries — such as state-level actors or commercial surveillance outfits — train classifiers to identify visited websites and services based on traffic patterns, even when encrypted and tunneled through VPNs.
DAITA v1 attempted to disrupt such analysis by applying uniform packet sizes and inserting dummy traffic to obfuscate behavioral signatures. However, its reliance on static client-side configurations made it susceptible to tailored attacks by adversaries familiar with its fixed logic.
Version 2 addresses this by overhauling the defense architecture to enable dynamic negotiation of obfuscation strategies. Now, each VPN connection is assigned a unique configuration from a large set of possible “defenses,” changing how dummy traffic is inserted by both the client and the server. These configurations are randomly selected and differ across connections — even for identical user activity — making consistent fingerprinting significantly more difficult.
According to Pulls' detailed write-up, DAITA v2 utilizes a protocol akin to those used in post-quantum secure tunnels to negotiate a shared defense between the client and relay node. This replaces the static client-side logic from v1 with flexible, server-defined instructions that govern traffic padding behavior.
“The architecture now allows Mullvad to continually generate and deploy new defenses without requiring client updates, invalidating adversarial models that rely on reverse-engineering previously known behaviors,” Pulls explains.
Under the hood changes
In v1, DAITA's client used a fixed set of four state machines to insert cover traffic. These included:
- A padding packet if no data was sent in 1.5–9.5 seconds.
- A response packet for every third or fifth incoming packet.
- Randomized delay-based dummy traffic.
These machines ran in a deterministic way, meaning adversaries could potentially learn and exploit their behavior. In contrast, DAITA v2 removes these hardcoded rules. Instead, the client receives defense parameters from the server at connection time, randomly selected from a large database of probabilistic state machines designed for maximum entropy and unpredictability.
The system continues to use two main types of cover traffic: uniform packet sizing and dummy packet injection. However, the latter has been optimized — DAITA v2 now uses around half as many dummy packets as before, thanks to more precise insertion logic. This translates to a lower bandwidth overhead, improving performance, especially on mobile connections.
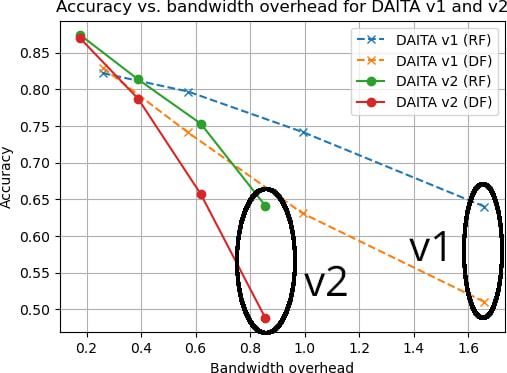
Early internal benchmarks show that DAITA v2 maintains the same level of protection as v1 against fingerprinting techniques like Deep Fingerprinting (DF) and Robust Fingerprinting (RF), while significantly reducing average bandwidth consumption.
What's next
Mullvad has confirmed that DAITA version 3 is already in development and will incorporate a new type of defense in addition to the existing padding and dynamic configurations.
For users, enabling DAITA in the Mullvad app is straightforward, and those already using it will benefit from v2 automatically, provided their client is up-to-date. Since the system now selects defenses randomly at each connection, users experiencing slower performance can simply reconnect to receive a new configuration — one that may balance overhead and speed more favorably.
While DAITA is not a silver bullet against all forms of network surveillance, its evolution represents a significant advancement in practical privacy protections for VPN users — particularly as AI-based threats become increasingly capable.







Mullvad VPN is great. I consider them the best for privacy. Their servers are fast and reliable. They even run their own servers in many countries. Sadly, as they do not offer and affiliate program, they are not in the top 3 of VPNs as they should.