
A team of Greek researchers has published a study highlighting sensitive data leak risks in password managers due to the lack of encryption in all steps of data storage and processing.
The study, published by Efstratios Chatzoglou, Vyron Kampourakis, Zisis Tsiatsikas, Georgios Karopoulos, and Georgios Kambourakis, on Arxiv, provides a comprehensive analysis of the security posture of two dozen password managers, encompassing both desktop applications and browser plugins. This research scrutinizes the capacity of these password managers to safeguard secret credentials during their residency in the system's RAM across six representative scenarios.
Specifically, the study investigates scenarios including after logging into the password manager, while the manager is running, after locking the manager, during system hibernation, upon resuming from hibernation, and after logging out or closing the manager.
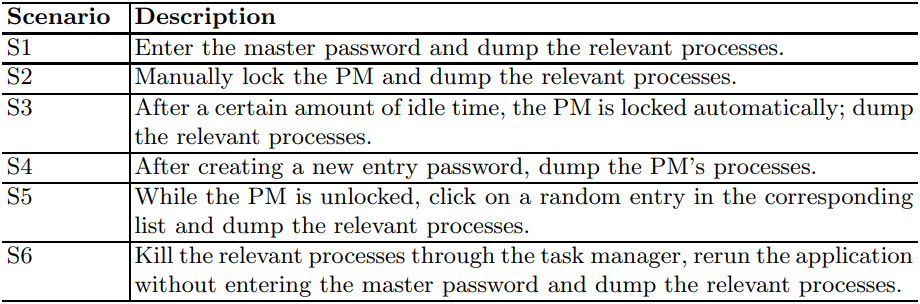
The findings reveal a concerning status: only three desktop password manager applications and two browser plugins were found not to store plaintext passwords in system memory. This vulnerability presents a significant risk, as the exposure of plaintext passwords in memory could lead to potential data breaches, putting users' sensitive information at risk.
Note: In the tables below, the white column represents the password manager's “master password” and the greyed column represents an entry password. A check represents a leak, and an X represents no leak.
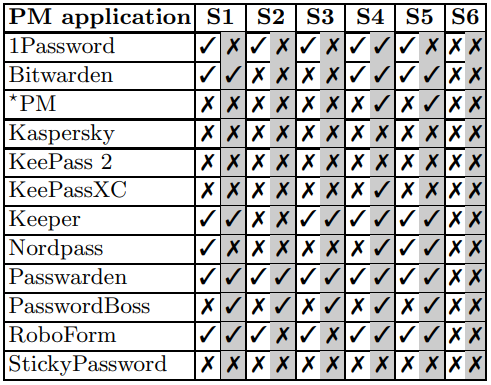

Surprisingly, only two vendors acknowledged this issue at the time of publication and reserved the identifier CVE-2023-23349. The rest have either disregarded the flaw or underestimated its implications.
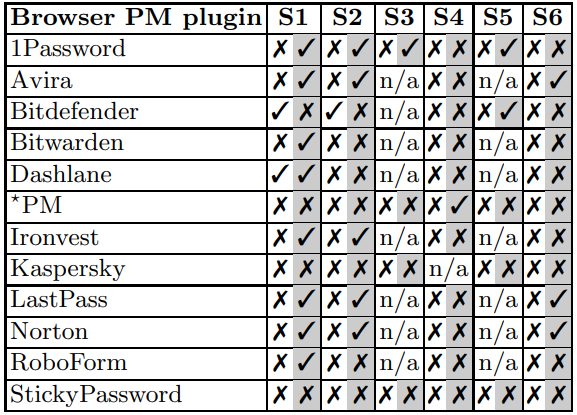
However, it's crucial to note that for attackers to leverage this vulnerability, they would first need to compromise the target machine with malware, which is a significant barrier. This requirement adds a layer of complexity to the attack, indicating that while the vulnerability is serious, exploiting it is not straightforward and requires prior access to the target's system.
Still, while some vendors may argue that such vulnerabilities only represent a threat in already compromised systems, the principle of defense in depth dictates that software, especially those handling sensitive data like password managers, should be designed to limit the damage of such compromises, not exacerbate them.
This study is a critical reminder of the ongoing challenges in securing password management software. Despite advances in technology and cybersecurity, the research highlights a pivotal oversight in the protection mechanisms of some of the most trusted tools in cybersecurity.
The fact that many of these products are not adequately securing data in all stages isn't a new realization, but the analysts, in this case, have highlighted the extent of the problem via a comprehensive evaluation of a large set of products, proving that the issue remains prevalent in the field.
As password managers continue to play a vital role in managing our digital identities, this investigation calls for re-evaluating their security features, urging developers and vendors to address these vulnerabilities promptly to ensure the confidentiality and integrity of users' data.







Thank you for the clarification on the test results, definitely interesting. I am interested in seeing who the “*” vendor is. Looking at the list of PM’s tested I can’t think of any well known PM remaining.
Hi Bryan, yes it will be interesting to see who it is. I don’t see Proton Pass on the list, but it’s relatively.
https://proton.me/pass
Hi Alex, right I didn’t see proton. I believe they are new to the PM market.
I second Bryan’s comment. What does the table mean?
Does a check mean that the manager passed the test or that the resercher successfully completed the exploit?
Why are there 2 checks/x’s for each test? What do the shaded/unshaded columns signify?
Good points, we should have added more to explain. I have now added an explanatory note to the article, and also added a screenshot of the table description. To answer your questions:
In the both tables, the white column represents the password manager’s “master password” and the greyed column represents an entry password. A check represents a leak, and an X represents no leak.
Hello. Would you help me understand the table. There are two columns for each test scenario. What do the two columns indicate?