
An independent security researcher has uncovered a significant vulnerability affecting millions of modems used by customers of Cox Communications.
His investigation led to the discovery of potential attack vectors capable of compromising network security and user privacy on a massive scale.
Discovering a breach
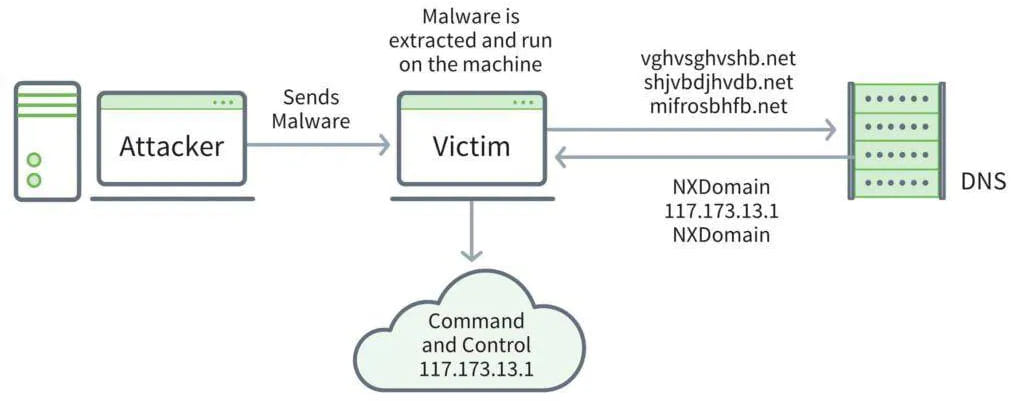
Two years ago, while exploiting a blind XXE vulnerability, the researcher spun up an AWS box and ran a Python webserver to receive traffic. However, they observed an unknown IP address replaying HTTP requests, indicating that someone was intercepting and replaying their traffic. Testing with different devices and servers confirmed the persistence of this behavior, leading the researcher to suspect that their modem had been compromised.
Tracing the suspicious IP address, the researcher found it belonged to DigitalOcean and was associated with several phishing websites targeting a South American cybersecurity company, ISG Latam. This added complexity to the investigation, suggesting that the attackers might be part of a sophisticated phishing and malware operation.
samcurry.net
Further inquiries revealed that the modem, a Cox Panoramic Wifi gateway, was likely compromised. The researcher handed over the device to the ISP, receiving a new one that stopped the suspicious behavior. However, the lack of access to the compromised modem hindered further investigation at the time.
Revisiting the case
In early 2024, during a discussion with cybersecurity colleagues, the researcher decided to revisit the case and made a startling discovery.
He found that the suspicious IP address had been used as a C&C server with domains following an algorithmic naming convention. This pointed towards a domain generation algorithm typically used by malware operators, suggesting the presence of sophisticated malware infrastructure.
samcurry.net
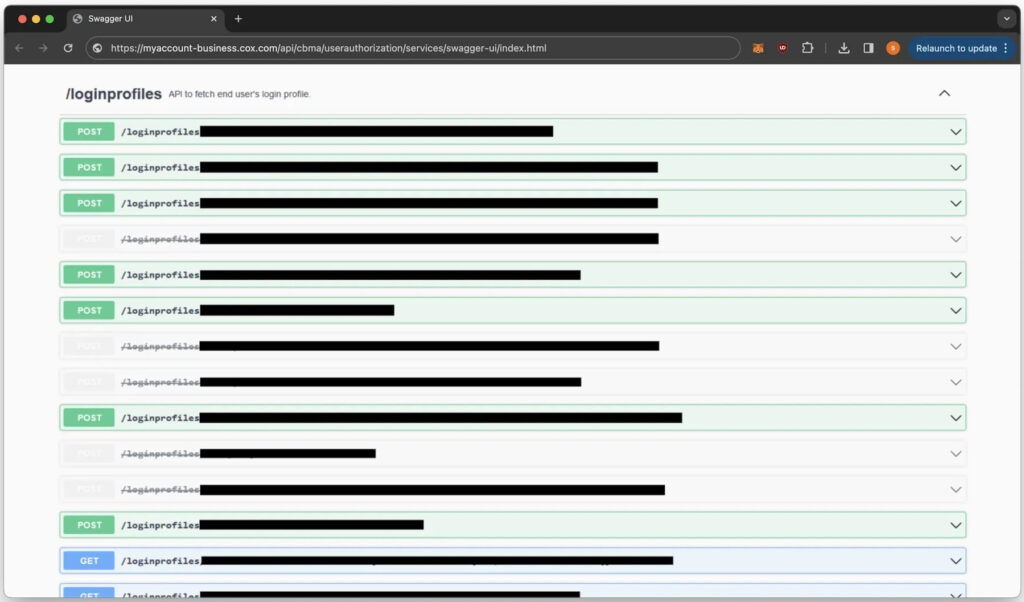
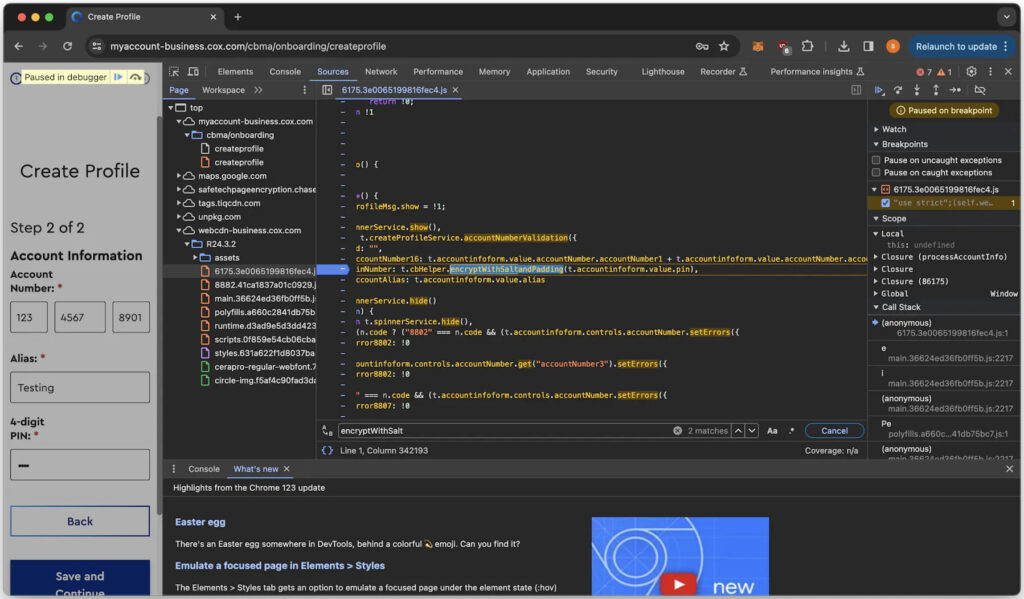
Intrigued, the researcher decided to probe the Cox Business portal, discovering a plethora of API calls that facilitated device management. By analyzing JavaScript files and endpoints, the researcher identified vulnerabilities that allowed unauthorized access to customer data and device settings. This included retrieving MAC addresses and executing arbitrary commands on modems, highlighting a critical flaw in the ISP’s backend infrastructure.
samcurry.net
Through meticulous testing, the researcher confirmed that exploiting these API vulnerabilities could grant attackers the same permissions as ISP support staff, allowing them to control any modem within the network.
The severity of these findings prompted the researcher to responsibly disclose the vulnerabilities to Cox Communications. Within hours, the ISP patched the exposed API calls and initiated a comprehensive security review.
- 03/04/2024 – Vulnerability reported to Cox via their responsible disclosure program.
- 03/05/2024 – Vulnerability hot-patched, all non-essential business endpoints return 403 and no longer function.
- 03/06/2024 – Researcher confirms inability to reproduce the vulnerability.
- 03/07/2024 – Cox begins comprehensive security review.
- 04/10/2024 – Researcher informs Cox of intent to disclose the findings 90 days from initial disclosure.
- 04/29/2024 – Researcher shares a draft of the final blog post with Cox.
Impact and recommendations
Cox Communications, a major broadband provider in the United States, serves millions of customers across the country. The exposed vulnerabilities underscored significant risks, potentially allowing attackers to execute commands, modify settings, and access sensitive information of any Cox Business customer.
The investigation into the initial modem compromise remains unresolved. Despite extensive efforts, the exact method of exploitation remains unknown. The researcher speculates that it could involve targeting the ISP’s device management tools or exploiting a private vulnerability in the modem’s firmware. The peculiar behavior of replaying HTTP requests adds to the mystery, suggesting that the attacker’s motives and methods were more complex than initially understood.
Consumers are recommended to take the following actions:
- Change the default passwords the network devices came with.
- Use network traffic monitoring tools to detect atypical patterns pointing at potential intrusions.
- Ensure that modem software and firmware are up to date with the latest security patches.
- Prefer secure, encrypted connections for sensitive online activities.
- Wherever possible, enable two-factor authentication for an added layer of security.







yeah every time I go to clock into my account it says they found a breach. change your password and it was a lot of stuff on my thing but I think I recognized all of them but I removed them all. changed my password my Wi-Fi password
I am a COX customer and a few days ago I got a notification through my COX app about a new device logged onto my WiFi network. I logged into the app and noticed 4 or 5 devices I didn’t recognize. One was registered as a VIZIO TV, another was an iPad and there was also a security camera (a Chinese brand). I quickly paused all of these devices and changed my account password and security questions and I haven’t received any similar notifications since.
Then yesterday and today I received texts from a COX number that has previously sent me verification codes. One message said “We’re sorry to see you go…” implying I had canceled my subscription, which I had not. The other text said “Your appointment has been cancelled…” when I neither made nor cancelled any appointment.
I called customer service this morning and the phone agent told me the same thing had happened to his own personal account today and they would “open an internal investigation” into my complaint. The problem is obviously much bigger than they’re letting on publicly.