
Microsoft Threat Intelligence revealed that the Russian-based threat actor known as ‘Forest Blizzard,' or APT28, has been actively exploiting a vulnerability in Windows Print Spooler service, identified as CVE-2022-38028, using a custom malware named ‘GooseEgg.'
This exploit has been part of a series of strategic intelligence-gathering operations targeting a broad spectrum of sectors, including government, transportation, and education across Ukraine, Western Europe, and North America.
Forest Blizzard, attributed to Unit 26165 of the Russian GRU, has been operating since at least 2010 with the primary objective of supporting Russian government foreign policy initiatives. This group stands out from other GRU-affiliated groups due to its focus on intelligence collection rather than outright destructive attacks.
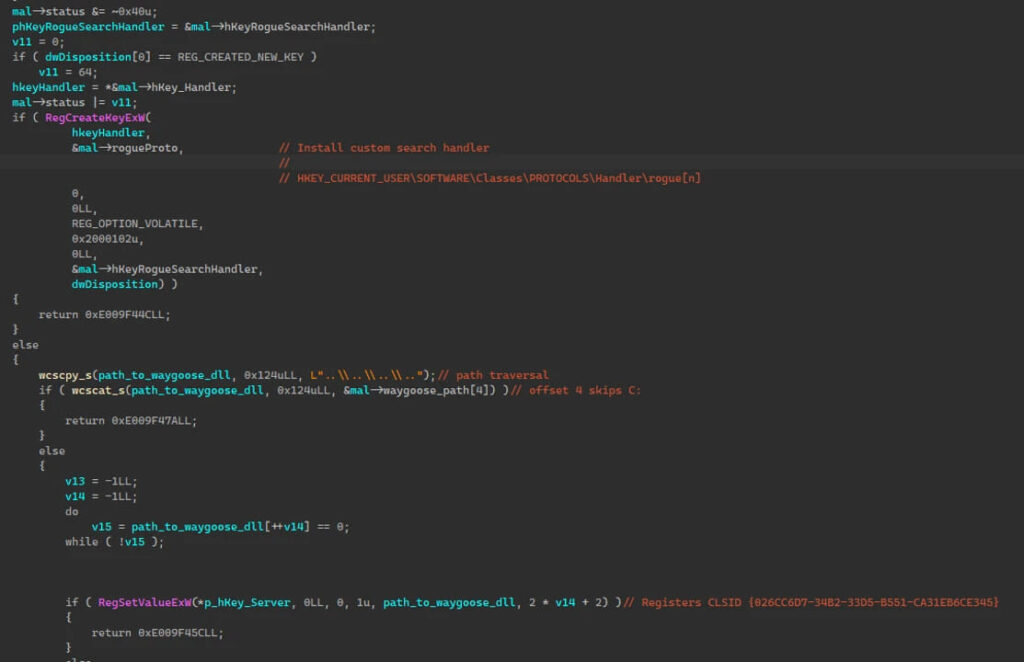
The tool at the center of this campaign, dubbed GooseEgg, allows the threat actor to execute code with SYSTEM-level permissions, thereby facilitating the elevation of privileges and theft of credentials within compromised networks. GooseEgg has been utilized to manipulate a JavaScript constraints file, leading to unauthorized command execution within the Windows Print Spooler service.
Forest Blizzard employs GooseEgg through batch scripts such as “execute.bat” and “doit.bat” to establish persistence and elevate privileges. The GooseEgg binary itself, with variants named justice.exe and DefragmentSrv.exe, among others, can launch additional malicious applications or DLLs with elevated permissions. This functionality extends the actor's capability to install backdoors, move laterally across networks, and execute remote commands.
Microsoft
The malware components are often stored in deceptively named directories within C:\ProgramData, mimicking legitimate software folders like those of Microsoft, Adobe, and NVIDIA, which helps to evade detection.
Microsoft's report includes specific indicators of compromise (IoCs), such as file names, hashes, and malicious registry keys, which organizations can use to detect potential breaches or place defensive measures. To further mitigate the threat, Microsoft advises applying the security update for CVE-2022-38028 and disabling the Print Spooler service where not necessary, especially on domain controllers.







Leave a Reply