
Microsoft Threat Intelligence has linked recent password spray attacks to “Storm-0940,” a Chinese nation-state threat actor leveraging compromised routers in a covert network known as “Quad7.”
Active since 2021, Storm-0940 has intensified its attacks on organizations in North America and Europe, utilizing credential theft tactics to target think tanks, governmental organizations, law firms, and other critical sectors. Microsoft has published an in-depth report detailing the covert network and offering guidance on mitigating these attacks.
A network of compromised routers
Since August 2023, Microsoft has observed attacks originating from Quad7, an infrastructure of compromised small office and home office (SOHO) routers, primarily from TP-Link. Operated by unknown actors within China, Quad7 enables threat actors to mask their true locations, distributing password spray attacks across thousands of compromised IP addresses. Microsoft's research identifies this network as part of a larger botnet with significant resilience against conventional defenses.
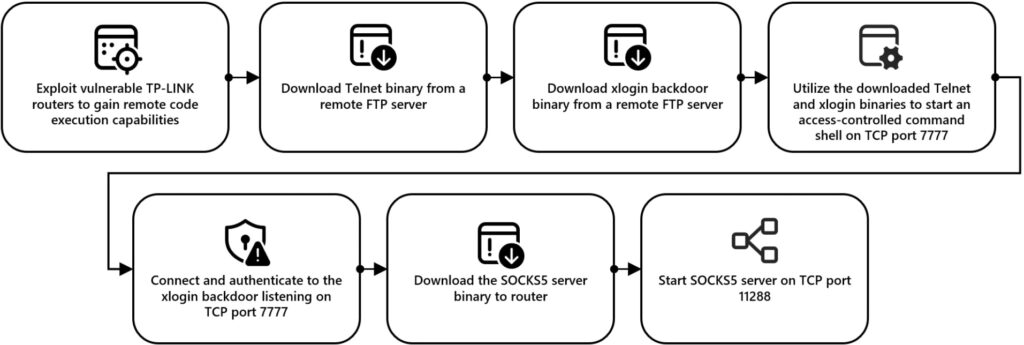
These compromised routers are remotely accessed and configured to support password spraying, exploiting vulnerabilities to load malicious binaries. Key components installed on the routers include:
Telnet and xlogin backdoor binaries for command shell access on TCP port 7777
SOCKS5 proxy servers on TCP port 11288 to anonymize and route password spray attempts
Password spraying on Microsoft accounts
Microsoft's analysis indicates that Quad7's password spray operations use a strategy designed to evade detection: it typically submits only one sign-in attempt per target account per day. This low-frequency approach prevents alerts that would normally flag repeated failed login attempts from a single IP address. Microsoft reports an average of 8,000 compromised devices within Quad7, with about 20 percent actively conducting password sprays at any given time.
Microsoft
Credential handover from Quad7 to Storm-0940 occurs almost immediately after a successful password spray attack, allowing for swift exploitation of compromised accounts. Storm-0940 has been observed using these credentials to:
- Conduct lateral movement across networks, deploying tools to further access sensitive systems
- Install proxy tools and remote access trojans (RATs) on network devices to maintain persistence
- Exfiltrate data from compromised environments, indicating its primary objective is espionage
The close coordination between Quad7's particular sub-cluster and Storm-0940 underscores a likely strong connection between these operations, which Microsoft suspects to be supported by several Chinese threat actors sharing Quad7 credentials.
Quad7 operational variance
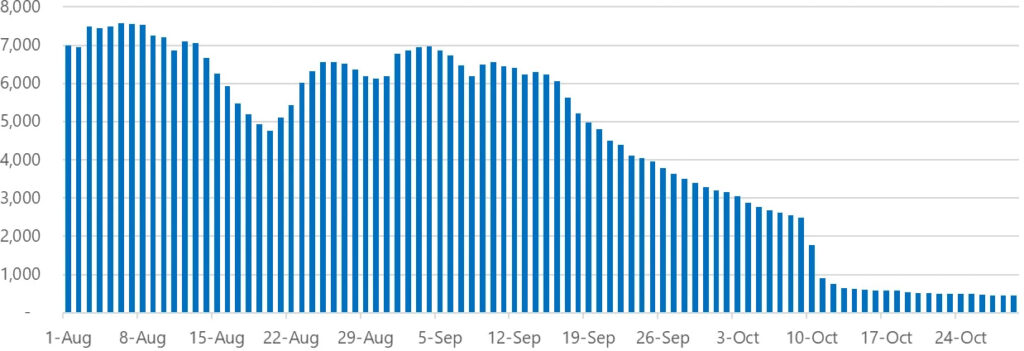
Microsoft's report includes data from security firm Sekoia.io and infrastructure analysis tool Censys.IO, indicating a decline in Quad7-related activity since mid-2024. This reduction follows increased public exposure of the botnet's structure, causing the operators to shift tactics. As of October 2024, Microsoft detects signs that Quad7 may be rebuilding its infrastructure with new operational signatures, hinting at a re-emergence under modified configurations.
Microsoft
Quad7's adaptive nature has previously allowed it to transition from open proxies to more stealthy backdoors, including new “UPDTAE” and “FsyNet” implants, which signal its operators' ongoing intent to avoid detection.
Defense recommendations
Microsoft advises organizations to improve their defenses against password spraying attacks, emphasizing credential hygiene and multi-factor authentication (MFA). Key recommendations include:
- Enforcing MFA on all accounts without exception
- Implementing passwordless authentication methods, such as Windows Hello for Business or FIDO keys, to reduce password dependency
- Blocking legacy authentication protocols that do not support MFA, limiting avenues for attackers
- Enforcing conditional access policies in Azure AD to regulate network access based on user and location criteria
- Monitoring network activity for compromised IPs, especially those used by Quad7.







Leave a Reply