
Microsoft has dealt a major blow to the cybercrime ecosystem by dismantling critical infrastructure tied to Lumma Stealer, a prominent infostealer malware-as-a-service (MaaS) that has enabled widespread credential theft and financial fraud globally.
The operation follows a legal filing by Microsoft's Digital Crimes Unit (DCU) in the U.S. District Court for the Northern District of Georgia. With court approval, Microsoft seized and disabled over 2,300 domains associated with Lumma's command-and-control (C2) infrastructure. The U.S. Department of Justice simultaneously took down Lumma's central command structure, while international partners, including Europol's EC3 and Japan's JC3, facilitated the suspension of infrastructure based in their jurisdictions.

Microsoft
Lumma Stealer, tracked by Microsoft Threat Intelligence as Storm-2477, has been active since at least 2022. The malware is sold through underground forums and marketed using a tiered subscription model that includes features like log viewing, traffic analysis, and even access to the malware's source code. Operators can build custom binaries via a web panel and manage stolen data through dedicated C2 panels. At its peak, Lumma was used by ransomware groups such as Octo Tempest (Scattered Spider) and other affiliates tracked as Storm-1607, Storm-1113, and Storm-1674.
Among the many attacks involving the malware family are League of Legends themed campaigns, cracked Black Myth: Wukong installers, fake game cheats on GitHub, and attacks exploiting a massive CrowdStrike Falcon outage last summer.
Recent Lumma activity and technical overview
Microsoft reports that between March and May 2025, over 394,000 Windows machines were infected with Lumma. The malware primarily targets browser credentials, cryptocurrency wallets, and sensitive documents, often using sophisticated delivery chains. Common infection vectors include spear-phishing emails impersonating brands like Booking.com, malvertising campaigns mimicking software downloads, and drive-by downloads via compromised websites. Notably, Lumma campaigns have also used deceptive CAPTCHA pages and clipboard-manipulating tactics known as ClickFix to trick users into executing malicious scripts.
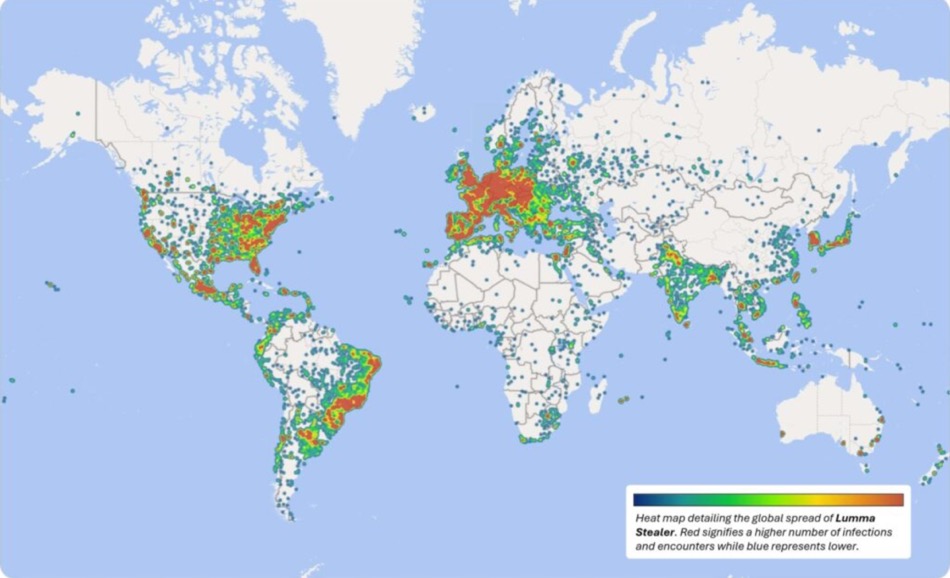
Microsoft
The malware is highly evasive. Its binaries are protected with advanced obfuscation methods like Control Flow Flattening, LLVM-based virtualization, and syscall-based API implementations. Lumma can execute payloads via process hollowing, frequently injecting code into legitimate Windows processes such as msbuild.exe or regasm.exe. It communicates with its operators through encrypted channels hidden behind Cloudflare proxies, and even includes fallback C2s embedded in Steam profiles and Telegram channels.
Microsoft's takedown campaign not only seized domains but also sinkholed over 1,300 of them, redirecting them to servers controlled by Microsoft. This allows the DCU to monitor victim connections, gather intelligence, and aid in the remediation of infected systems. Partnering organizations like ESET, BitSight, Cloudflare, Lumen, and CleanDNS played key roles in disabling Lumma's infrastructure across hosting and DNS layers.
Lumma's client base was extensive, with its creator, known by the alias Shamel, previously claiming to have “about 400 active clients.” His marketing strategy included a distinctive bird logo and the slogan, “making money with us is just as easy,” reflecting the commoditization of cybercrime.
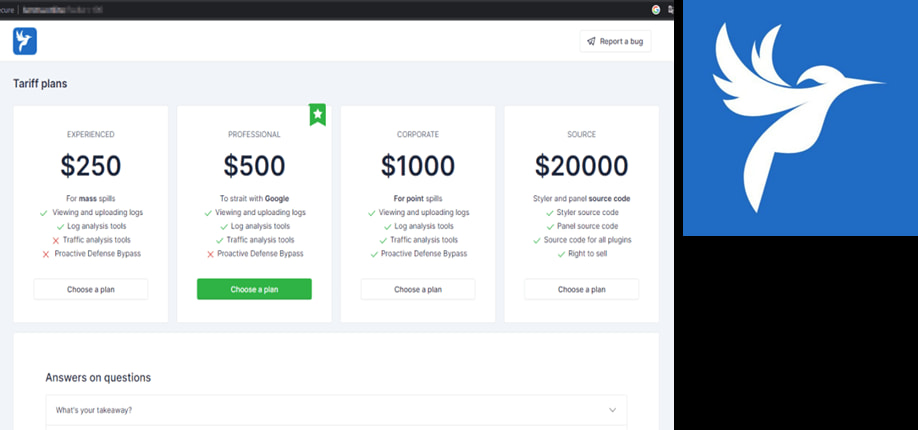
Microsoft
This disruption, while significant, is not a full neutralization. Lumma's developers and affiliates remain active, and the infrastructure could be rebuilt. However, by severing key distribution and communication channels, Microsoft and its partners have introduced meaningful friction to the operations of hundreds of cybercriminals.







Leave a Reply