
A critical Windows zero-day vulnerability is being actively exploited by state-sponsored hacking groups, yet Microsoft has opted not to release a security patch.
The flaw, which allows attackers to execute hidden commands using malicious shortcut (.lnk) files, has been leveraged in espionage campaigns since at least 2017.
Widespread exploitation, no patch in sight
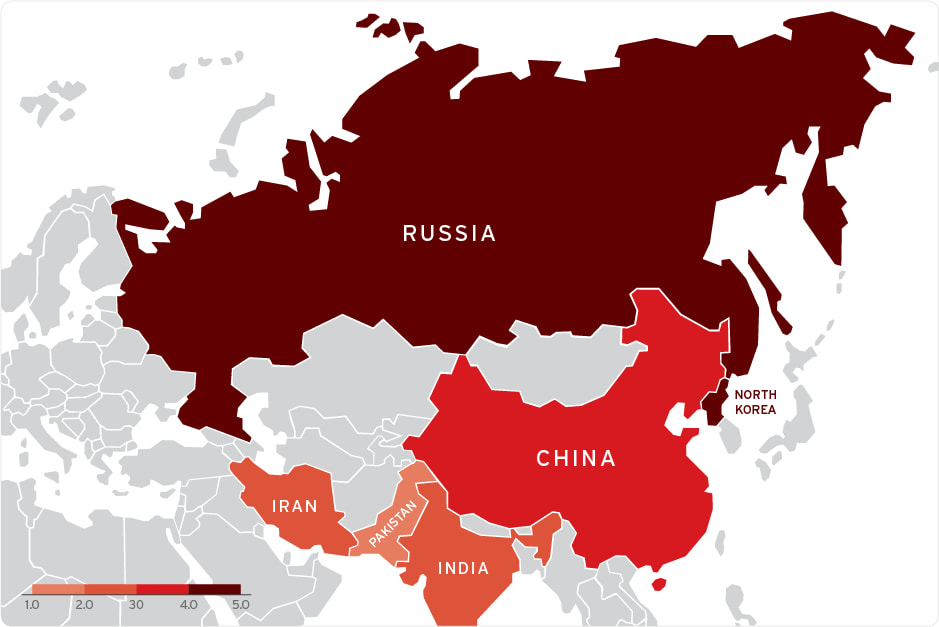
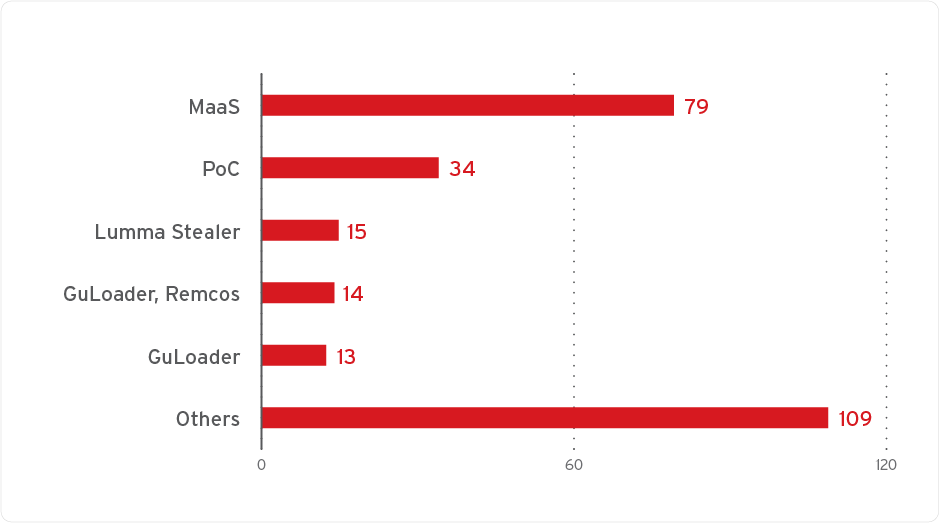
The Trend Zero Day Initiative (ZDI) discovered nearly 1,000 malicious .lnk files abusing the flaw they track internally under ZDI-CAN-25373, with attacks traced to at least 11 advanced persistent threat (APT) groups from North Korea, Iran, Russia, and China. These groups have used the vulnerability primarily for cyber espionage and data theft, targeting government agencies, financial institutions, the military, and critical infrastructure.
Trend Micro
ZDI reported the flaw to Microsoft via its bug bounty program, submitting a proof-of-concept exploit. However, Microsoft declined to address the issue, categorizing it as low severity and choosing not to release a patch. This leaves users exposed to continued exploitation, with no official fix available.
How attackers leverage the zero-day
The vulnerability resides in Windows' handling of .lnk files, allowing attackers to embed hidden command-line arguments that execute when a victim interacts with the file. These commands remain invisible in the file properties due to whitespace padding, making detection difficult.
APT groups have been seen distributing malicious .lnk files disguised as legitimate documents, using misleading icons and filenames such as report.pdf.lnk. Clicking these shortcuts silently launches cmd.exe or powershell.exe, fetching malware payloads without the user’s knowledge.
Organizations in North America, Europe, Asia, South America, and Australia have been affected, with a focus on government agencies, financial institutions (including cryptocurrency platforms), telecommunications firms, military and defense sectors, and energy and infrastructure companies.
Among the most active exploiters are North Korea’s APT37 (Earth Manticore) and Earth Imp (Konni), which have been using oversized .lnk files (up to 70MB) to evade detection.
Trend Micro
Mitigation strategies in absence of a patch
Since Microsoft has refused to release a fix, organizations must take immediate action to defend against this zero-day threat. ZDI suggests the following measures:
- Restrict .lnk file execution – Block shortcut files from untrusted locations.
- Monitor for suspicious processes – Detect cmd.exe or powershell.exe triggered by .lnk files.
- Deploy advanced endpoint security – Use Threat Detection and Response (XDR) tools to flag unusual shortcut file behavior.
- Inspect .lnk files manually – Use third-party tools to reveal hidden command arguments.







Leave a Reply