
Chinese state-aligned threat actors are actively exploiting critical vulnerabilities in Microsoft's on-premises SharePoint Server, targeting organizations worldwide with sophisticated attacks that enable credential-less remote code execution and persistent access.
Microsoft has released patches and urges immediate action.
The exploitation campaign tracked by Microsoft involves two primary vulnerabilities: CVE-2025-49706, a spoofing flaw, and CVE-2025-49704, which allows for remote code execution (RCE). These issues form part of an exploit chain now tracked as CVE-2025-53770 and CVE-2025-53771, collectively dubbed “ToolShell.” The vulnerabilities affect only on-premises SharePoint Server versions, namely, 2016, 2019, and Subscription Edition, with SharePoint Online in Microsoft 365 unaffected.
Exploitation by Chinese APTs
Microsoft Threat Intelligence attributes the campaign to three China-based groups:
- Linen Typhoon: A known espionage actor active since 2012, targeting government, defense, and strategic organizations.
- Violet Typhoon: Operating since 2015, this group targets NGOs, think tanks, and public sector entities, particularly in the U.S., Europe, and East Asia.
- Storm-2603: A less well-understood actor believed to be based in China, previously associated with ransomware deployment but now leveraging SharePoint flaws to extract cryptographic materials.
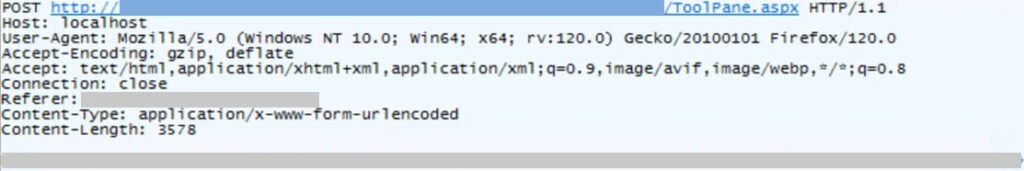
Initial access is gained through crafted POST requests to the ToolPane endpoint, bypassing authentication by spoofing the Referer header to /_layouts/SignOut.aspx, a trick first demonstrated earlier this year at Pwn2Own Berlin and weaponized in the wild by mid-July. Once inside, attackers deploy a malicious web shell file, spinstall0.aspx, and its variants, directly into the SharePoint server's layouts directory.
Microsoft
This script allows adversaries to extract ASP.NET MachineKey values, enabling the forging of valid __VIEWSTATE payloads and signing of malicious requests, effectively granting persistent access—even post-patch—unless the keys are rotated.
The ToolShell exploit chain abuses multiple vulnerabilities to allow unauthenticated attackers to:
- Upload arbitrary files to the server
- Remotely execute PowerShell scripts
- Harvest cryptographic keys used for session validation
- Deploy and operate web shells undetected
- Exfiltrate internal SharePoint data
Payload delivery occurs through PowerShell scripts dropped via w3wp.exe, the IIS worker process. Threat actors have been seen using tunnels such as c34718cbb4c6.ngrok-free[.]app/file.ps1 to fetch further payloads.
Defense recommendations
Microsoft SharePoint Server is a leading enterprise collaboration and document management platform used globally across sectors, including government, healthcare, and finance. While many organizations have moved to SharePoint Online, a significant portion still rely on on-prem deployments, often exposed to the internet for remote employee access, making them prime targets.
Given the widespread use of SharePoint and the sophistication of the exploit, mass exploitation was observed as early as July 18, with dozens of active compromises confirmed.
Microsoft issued emergency security updates for all supported versions of SharePoint Server on July 19–21, fully addressing the flaws. It also published detection logic, advanced hunting queries, and Indicators of Compromise (IoCs) via Microsoft Defender XDR and Microsoft Sentinel platforms.
The company confirmed AMSI (Antimalware Scan Interface) is essential to detect and block the unauthenticated exploit path, especially in Full Mode. Customers must also rotate MachineKey values post-update to invalidate stolen cryptographic material.
Organizations using on-premises SharePoint Server are strongly advised to:
- Apply July 2025 security updates immediately (CVE-2025-53770, CVE-2025-53771)
- Enable AMSI integration and deploy Microsoft Defender Antivirus or equivalent tools
- Rotate ASP.NET MachineKey values using PowerShell or Central Admin
- Restart IIS after patching and key rotation
- Isolate internet-exposed SharePoint servers until mitigation is complete
- Deploy Microsoft Defender for Endpoint to detect post-exploit behavior







Leave a Reply