
The Irish Data Protection Commission (DPC) has levied a €91 million fine against Meta Platforms Ireland Limited (MPIL) after concluding a five-year inquiry into the company’s handling of user data. The investigation, initiated in April 2019, was triggered by MPIL’s self-reporting of an incident where user passwords were inadvertently stored in plaintext on internal systems, bypassing proper encryption protocols.
Key findings and GDPR infringements
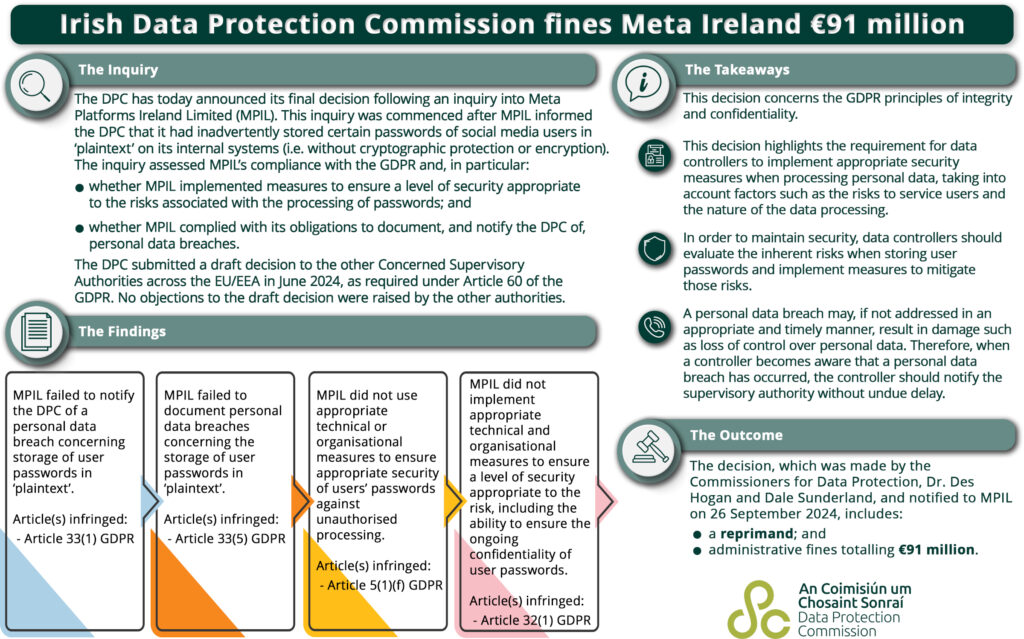
The DPC’s decision highlighted several General Data Protection Regulation (GDPR) violations. The decision was approved without objection from other European Economic Area (EEA) authorities, following the draft submitted in June 2024 under Article 60 GDPR. Commissioners Dr. Des Hogan and Dale Sunderland, overseeing the inquiry, determined that MPIL’s actions fell short of several GDPR mandates, including:
- Article 33(1) GDPR – Meta failed to notify the DPC of a personal data breach involving the storage of user passwords in plaintext.
- Article 33(5) GDPR – Meta did not properly document the breach concerning the unencrypted storage of these passwords.
- Article 5(1)(f) GDPR – Meta did not implement sufficient technical or organizational measures to ensure the security of user passwords against unauthorized processing.
- Article 32(1) GDPR – The company failed to uphold appropriate security standards to maintain the confidentiality and integrity of user passwords.
Deputy Commissioner Graham Doyle emphasized the critical nature of securing user passwords, stating: “It is widely accepted that user passwords should not be stored in plaintext, considering the risks of abuse that arise from persons accessing such data. It must be borne in mind that the passwords subject to consideration in this case are particularly sensitive, as they would enable access to users’ social media accounts.”
Meta's password security lapse
In March 2019, Meta disclosed to the DPC that certain user passwords were mistakenly stored in plaintext without encryption or cryptographic protection on its internal systems. The incident did not involve external access to these passwords. The inquiry, which began in April 2019, aimed to assess Meta’s compliance with GDPR obligations, focusing on whether the company had taken adequate measures to safeguard user passwords, appropriately documented the breach and notified the DPC as required.
The decision centers on the GDPR principles of integrity and confidentiality, which mandate that data controllers like Meta implement robust security measures tailored to the risks involved in data processing. This includes an obligation to evaluate and mitigate risks to maintain the security of personal data such as passwords.
The DPC’s decision includes two key corrective actions:
- A Reprimand under Article 58(2)(b) GDPR for the failure to uphold appropriate data protection standards.
- A €91 Million Administrative Fine under Articles 58(2)(i) and 83 GDPR.
DPC
The DPC’s findings reinforce the critical obligation of data controllers to adequately protect personal data, promptly document any breaches, and notify regulatory authorities without delay. Given the potential risks associated with unencrypted password storage — including unauthorized access and data abuse — this decision is a stern warning to organizations processing sensitive data across the EU.
The DPC promised to release the full text of the decision and additional details soon.







Leave a Reply