
McAfee Labs has detailed a novel infection chain involving AsyncRAT, a sophisticated Asynchronous Remote Access Trojan, that involves leveraging non-PE (Portable Executable) files to bypass security measures.
AsyncRAT has adapted to use a variety of file types, including PowerShell, Windows Script File (WSF), VBScript (VBS), JavaScript (JS), Batch (BAT), Text (TXT), and HTML to evade antivirus detection. This shift highlights a growing trend among cybercriminals to exploit less conventional file types in their attack vectors.
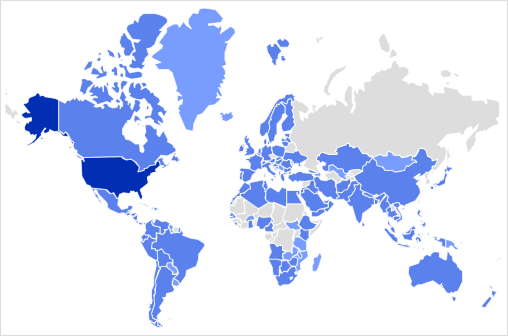
Most of the observed attacks target the United States, although McAfee observed signs of compromised worldwide, notably excluding Russia and Belarus, which indicates a potential source for the malicious activity.
McAfee
New AsyncRAT infection chain
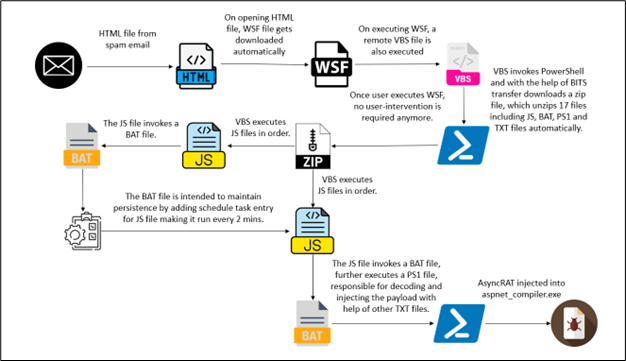
The infection begins with a seemingly innocent spam email that includes an HTML attachment. When the recipient opens the attachment, it automatically triggers the download of a WSF file disguised as an “Order ID” document, giving it a false appearance of legitimacy.
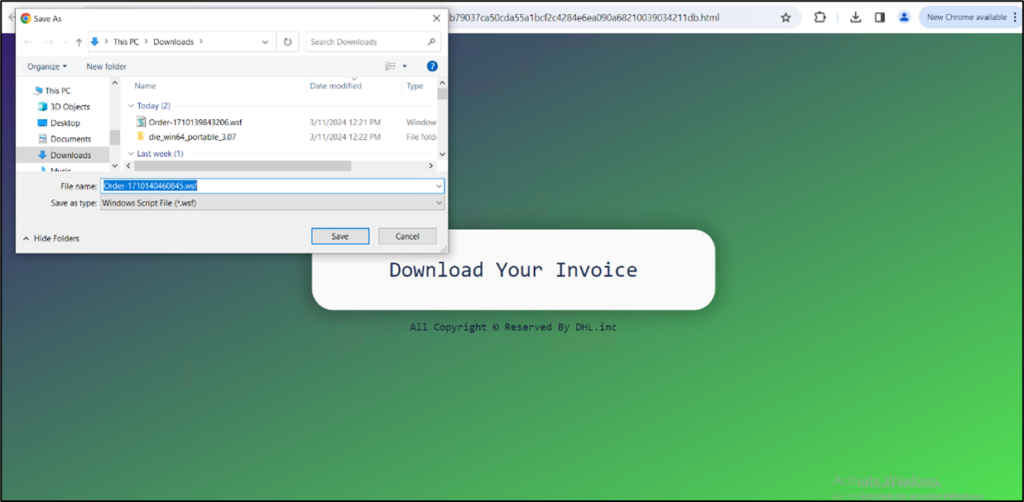
McAfee
This WSF file is a key component in the infection chain, leading to a series of automated downloads and executions without any further user interaction or remote operations by the attackers.
Following the execution of the WSF file, various scripts and batch files are executed in a predefined order:
- WSF -> Initiates the download of a TXT file named “1.txt”.
- ‘1.txt' -> Contains code that downloads a ZIP file, misleadingly labeled “r.jpg,” which actually contains the malware.
- Malware scripts -> Files extracted from the ZIP file, including “basta.js” and “node.bat,” set up a persistent backdoor on the victim's system by configuring scheduled tasks.
- Final payload -> The malware culminates with the injection of malicious code into ‘aspnet_compiler.exe', a process often overlooked by security software.
McAfee
AsyncRAT's sophistication is evident in its use of scheduled tasks to maintain persistence on the compromised system, obfuscation in its code, which is hidden within benign-looking files, and process injection targeting legitimate system processes to evade detection.
McAfee Labs advises individual users and organizations to enhance their defensive posture by attending/organizing phishing training, using secure web gateway with real-time scanning, and performing sender identity verification when met with requests to download dubious files via email.







Leave a Reply