
A new wave of malicious browser extensions, some posing as VPN extensions, has been found on the Chrome Web Store, blending functional features with covert surveillance and code execution capabilities.
These dual-purpose extensions, active since at least February 2024, were part of a broader campaign orchestrated by an unidentified threat actor who has created over 100 fake websites and Chrome extensions.
Malicious VPN extensions
The extensions mimic legitimate services, including productivity tools, crypto platforms, analytics suites, and notably, VPN clients. Behind the scenes, they establish encrypted connections to attacker-controlled servers, from which they retrieve commands, download executable scripts, and exfiltrate sensitive user data.
DomainTools
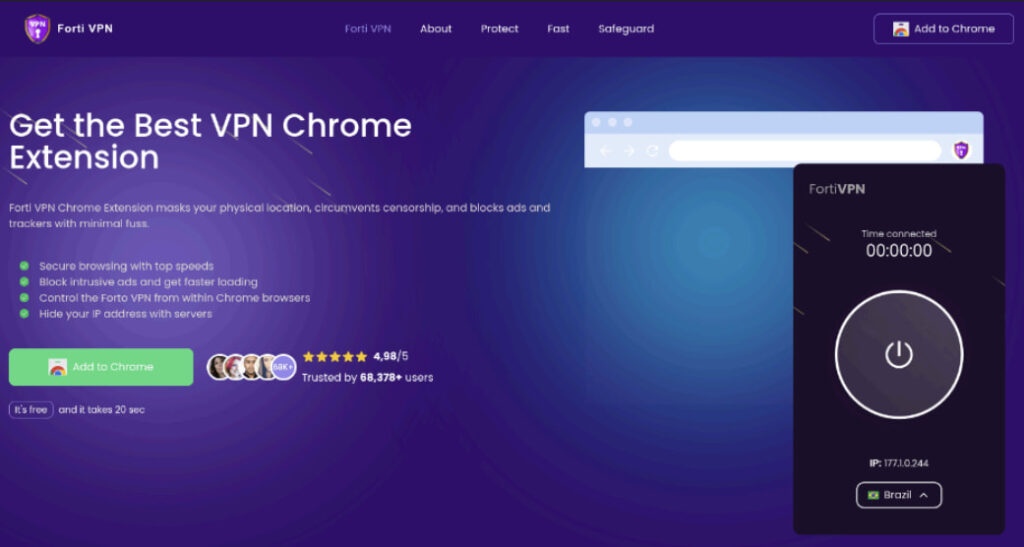
The findings were published in a detailed threat intelligence report by DomainTools, which discovered several malicious extensions, including a fake FortiVPN client. This extension is distributed via the spoofed domain forti-vpn[.]com, presents itself as a legitimate VPN service. It connects users to a seemingly functional WebSocket VPN backend using a hardcoded API key, offering partial VPN-like behavior. However, the same extension also connects to a second, malicious server (api.infograph[.]top) to receive attacker instructions, exfiltrate cookies, and proxy traffic through the user's browser.
Key malicious behaviors include:
- Retrieving all browser cookies via chrome.cookies.getAll({}), compressing and encoding them, and sending them to the attacker's server.
- Acting as a dynamic proxy, redirecting user traffic through attacker-controlled infrastructure with support for proxy authentication.
- Executing arbitrary scripts retrieved post-installation by injecting them into active tabs via chrome.tabs.sendMessage.
DomainTools
Similar behaviors were observed in other extensions, such as “Manus AI” and “SiteStats”, each linked to fake services like manusai[.]sbs and sitestats[.]world. These extensions granted themselves broad permissions, allowing for DOM manipulation, content injection, and real-time network interception. In some cases, the extensions hardcoded third-party API keys, a poor security practice that further exposes users and service providers.
The underlying technical infrastructure across these extensions was consistent. Each used background scripts — typically named background.js or background.iife.js — that handled most malicious logic. These scripts established secure communications using JWT tokens signed with HMAC SHA-256, with the extension ID often serving as the secret. This enabled persistent, authenticated interactions with the actor's backend.
The fake websites and extensions exploited current tech trends, such as AI tools and VPN demand, to lure unsuspecting users. Some leveraged Facebook ad tracker IDs for promotion, further complicating attribution. Many domains were registered through NameSilo, used Cloudflare for hosting, and employed SSL certificates issued by WE1.
While Google has removed several of these extensions following detection, the attacker's rapid deployment strategy and the time lag in response underscore a systemic challenge in browser extension security.
Users looking to install VPN extensions should only trust those from reputable publishers, and always scrutinize user reviews for potential signs of trouble. Be wary of extensions requesting excessive permissions, especially those unrelated to the tool's stated function.







Leave a Reply