
Researchers from ETH Zurich have uncovered severe cryptographic vulnerabilities in several end-to-end encrypted (E2EE) cloud storage services, challenging their claims of security.
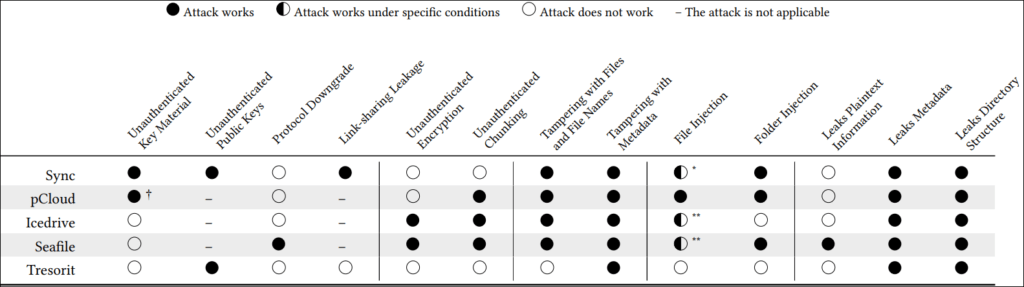
Jonas Hofmann’s and Kien Tuong Truong's analysis revealed critical issues in four major services — Sync, pCloud, Icedrive, and Seafile — exposing how easily a malicious server could compromise user data through file injection, tampering, and direct access to plaintext. The only provider that escaped major vulnerabilities was Tresorit, which employs a more robust cryptographic structure.
“Broken clouds” (and security promises)
The analysis focused on five prominent E2EE providers — Sync, pCloud, Icedrive, Seafile, and Tresorit — which collectively serve over 22 million users, including high-profile institutions such as the University of Toronto and the Canadian government. These services, which promise robust encryption protocols to prevent even the service providers from accessing user data, were found lacking in multiple areas. The researchers exposed ten attack vectors across these platforms, four of which directly impact file confidentiality, while others target file integrity and metadata.
Key vulnerabilities include:
- Key Replacement Attacks: In Sync and pCloud, an attacker could substitute encryption keys with their own, allowing them to decrypt all future user data.
- Protocol Downgrade in Seafile: Seafile's encryption protocols could be downgraded, enabling brute-force attacks on user passwords.
- File and Metadata Tampering: Attackers could modify file names and metadata and even swap files between directories without detection in Sync, pCloud, and Icedrive.
- Injection of Malicious Files: Sync and pCloud were particularly susceptible to file injection attacks, where an adversary could upload rogue files that would appear to the user as if they uploaded them.
Sync, a Canadian company with over two million users, and pCloud, a Swiss provider with more than 19 million users, were among the most impacted. Both services use RSA encryption but fail to authenticate keys, leaving room for attackers to swap encryption keys or inject files into users' storage. Sync's vulnerabilities extended to link-sharing mechanisms, where decryption keys were embedded in shared URLs, thus exposing sensitive files to the server.
ETH Zurich
Sync, pCloud, Icedrive, and Seafile were informed of these vulnerabilities in April 2024, with a standard 90-day disclosure period proposed. While Icedrive acknowledged the findings but chose not to address the issues, Seafile committed to patching a protocol downgrade flaw. As of October 2024, Sync and pCloud had yet to respond to multiple contact attempts.
Broader implications
The findings highlight widespread issues in E2EE cloud storage and reveal that many providers fail to deliver on their promises of zero-knowledge encryption. Despite positioning themselves as privacy-focused alternatives to mainstream services like Google Drive or Dropbox, these providers struggle to meet the security standards expected of true E2EE solutions. The researchers emphasize the need for a unified, standardized protocol for E2EE cloud storage, similar to the Signal protocol used in secure messaging.
Security recommendations
Hofmann and Truong propose two primary courses of action to rectify the discovered issues: first, conducting more rigorous analyses of E2EE storage systems to understand the existing cryptographic weaknesses better; and second, developing a standardized and robust E2EE protocol. Providers should also adopt authenticated encryption methods, secure key management, and stronger integrity checks to ensure that user data is truly protected from malicious servers.
For users concerned about the security of their cloud-stored data, the researchers advise selecting providers with proven security track records and staying informed about the cryptographic guarantees of their chosen service.







Leave a Reply