The LoveSac Company has disclosed a data breach following unauthorized access to its internal systems, linked to a ransomware attack claimed by the RansomHub group in early March 2025.
While the firm reports no confirmed misuse of stolen data, sensitive personal information may have been exposed, prompting a notification campaign and an offer of identity protection services to affected individuals.
The breach was first detected on February 28, 2025, when LoveSac identified suspicious activity within its network. A subsequent investigation revealed that an unauthorized actor accessed and exfiltrated data from specific systems between February 12 and March 3, 2025. The company completed its review of the compromised files in recent weeks, enabling it to identify which individuals were affected and the types of personal data involved.
Though the company has not disclosed the exact categories of exposed data for each individual, its notices suggest that names and other unspecified sensitive personal identifiers were included in the stolen files. LoveSac maintains that it has not observed any fraudulent activity directly linked to the incident but is providing two years of complimentary identity monitoring and credit protection through Experian as a precaution.
Founded in 1995 and based in Stamford, Connecticut, The LoveSac Company is a publicly traded US furniture retailer best known for its modular sectional sofas (“Sactionals”) and large beanbag-style seating (“Sacs”). LoveSac operates both online and through a network of retail showrooms across the United States, serving a growing base of direct-to-consumer customers.
On March 6, 2025, the RansomHub ransomware group took responsibility for the breach, claiming to have stolen a trove of sensitive corporate and personal data. At the time of the claim, RansomHub threatened to publish the stolen information unless a ransom was paid. It remains unclear whether LoveSac engaged in negotiations or made a payment, and no public ransomware payment has been confirmed as of the time of writing.
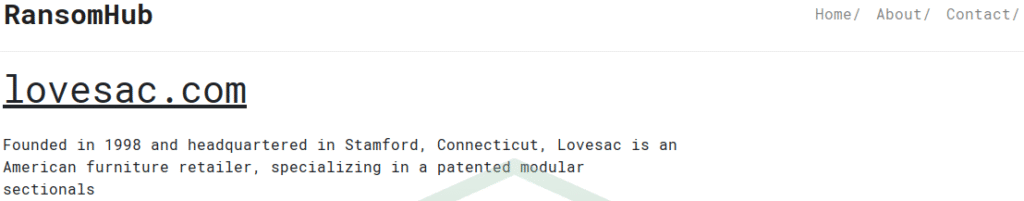
The attack vector in LoveSac’s case has not been publicly confirmed. However, RansomHub actors are known to exploit unpatched systems, weak credentials, and remote desktop protocol (RDP) services to gain initial access, followed by data exfiltration and encryption.
In response to this breach, LoveSac reports that it has now reinforced its security posture by reviewing internal policies, enhancing controls over personal data access, and notifying the appropriate regulatory bodies. The company is urging affected individuals to remain vigilant by monitoring their financial accounts, reviewing credit reports, and placing fraud alerts or credit freezes if necessary.







Leave a Reply