
New insights into the Gravy Analytics data breach reveal the vast extent of the company’s location-tracking operations and the potential for user de-anonymization. The leaked data, part of a 10 TB dataset, exposes the granular details of individuals’ movements and raises fresh concerns about the security and ethics of location data collection.
Looking into the leaked data
An analysis of the Gravy Analytics data breach reveals disturbing insights into the scale and sensitivity of the information compromised. According to Alon Gal, co-founder of Hudson Rock, the leaked sample includes 10 million detailed location records collected from over 15,000 mobile applications. These records contain precise GPS coordinates, app data sources, unique phone identifiers, user agents, and other metadata, offering a comprehensive view of individuals’ movements over time. Popular apps such as Tinder, Grindr, Candy Crush, and 9GAG are implicated, with their integration of third-party SDKs enabling the collection and sharing of user location data.
Alon Gal
A separate file in the breach exposed Gravy Analytics’ extensive client list, which includes major corporations like Google, Uber, Spotify, and Babel Street—a government contractor known for providing data analytics services to law enforcement and intelligence agencies. This highlights how user location data, often shared unknowingly through app partnerships or aggregated by data brokers, can end up in the hands of commercial and governmental entities alike, with minimal oversight or user consent.
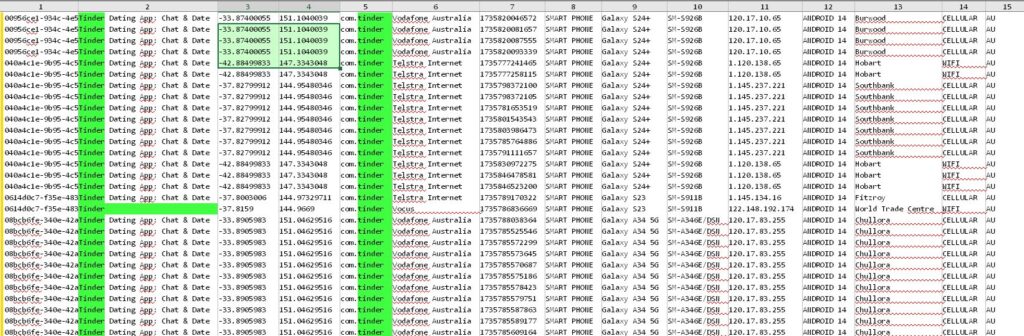
The leak’s potential for deanonymization has raised significant alarm. Security researcher Baptiste Robert demonstrated how the stolen data could be used to trace highly specific details of individuals’ lives. One example tracked a person from Columbus Circle in New York City to their home in Tennessee, where they were identified as the owner of a locksmith business.
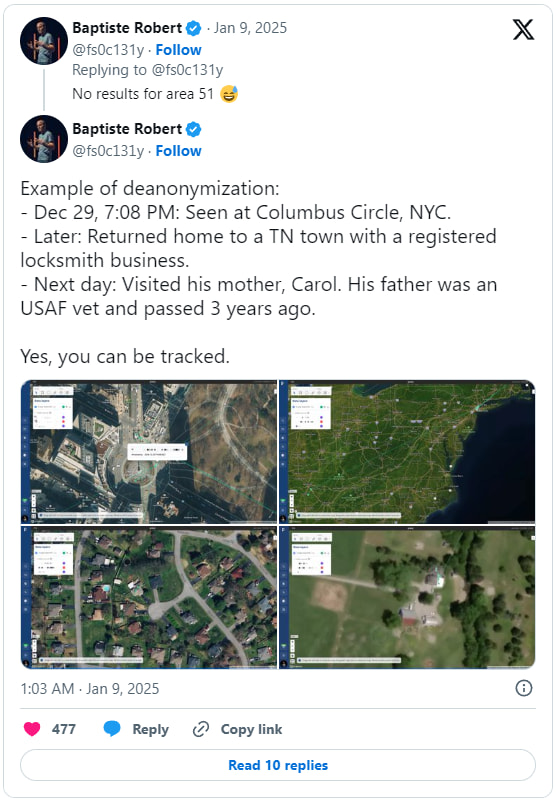
Another example followed an individual to Space Launch Complex 36, then mapped their work commute, stops at retail stores like Home Depot, and family visits near Kansas City. Such granular tracking poses profound privacy risks, revealing visits to sensitive locations like medical facilities, places of worship, or even private homes.
These revelations emphasize how seemingly benign apps can serve as conduits for invasive tracking, with Gravy Analytics aggregating and monetizing this data on a massive scale.
Gravy Analytics practices
Headquartered in Virginia, Gravy Analytics is a prominent player in the location data industry, processing an estimated 7 billion location data points daily. The company’s subsidiary, Venntel, has been involved in selling location data to U.S. government agencies, including the FBI and Department of Homeland Security. The breach reveals systemic vulnerabilities in Gravy’s infrastructure, with hackers gaining root access to servers and control over Amazon S3 buckets storing sensitive data.
The breach comes on the heels of an FTC settlement banning Gravy Analytics from selling sensitive location data obtained without proper user consent. This regulatory action highlighted past misuse of the company’s tools, including tracking visitors to abortion clinics.
Evade location tracking
The Gravy Analytics breach serves as a stark reminder of the privacy risks posed by location tracking. To protect personal data:
- Turn off location and Wi-Fi when not actively needed.
- Regularly review app permissions and revoke unnecessary access.
- Avoid apps with ads, as they often integrate third-party SDKs that share user data.
- Reset advertising IDs. On Android: Settings > Privacy > Ads > Delete advertising ID; on iOS: Settings > Privacy & Security > Tracking > Allow Apps to Request to Track.
This breach exposes the fragile security of the location data ecosystem and the ethical challenges of user data commodification at a massive scale. With hackers threatening to release the entire dataset, the privacy of hundreds of millions of users could be irrevocably compromised.







Leave a Reply