
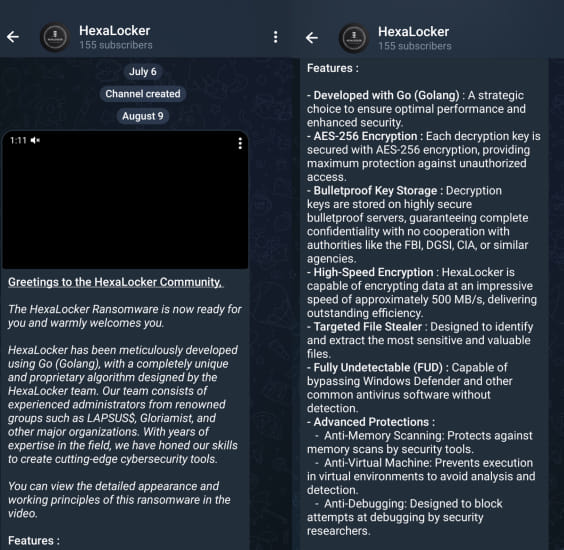
A former administrator of the notorious LAPSUS$ group has re-emerged with a new ransomware operation named HexaLocker.
The revelation comes just two months after LAPSUS$ announced its shutdown in June 2024. Synactiv, a cybersecurity firm, uncovered this new threat, with evidence pointing to a LAPSUS$ admin known as “ZZART3XX” as the key figure behind HexaLocker.
LAPSUS$, infamous for its high-profile cyberattacks against companies like Microsoft, Nvidia, and Uber, was primarily known for spear phishing, data theft, and extortion rather than ransomware deployment. However, HexaLocker marks a departure from their previous tactics, introducing a ransomware strain that encrypts victims' files and demands a ransom for decryption. The ransomware operation was first advertised on a Telegram channel associated with the group on August 9, 2024.
Synacktiv
HexaLocker is a sophisticated ransomware, written in Golang, that targets Windows systems. It uses a proprietary encryption algorithm and includes several advanced features designed to thwart analysis and detection. According to Synacktiv's analysis, HexaLocker employs anti-virtualization and anti-debugging techniques, utilizing modules such as GoDefender and Chacal, making it difficult for security researchers to dissect its behavior in controlled environments.
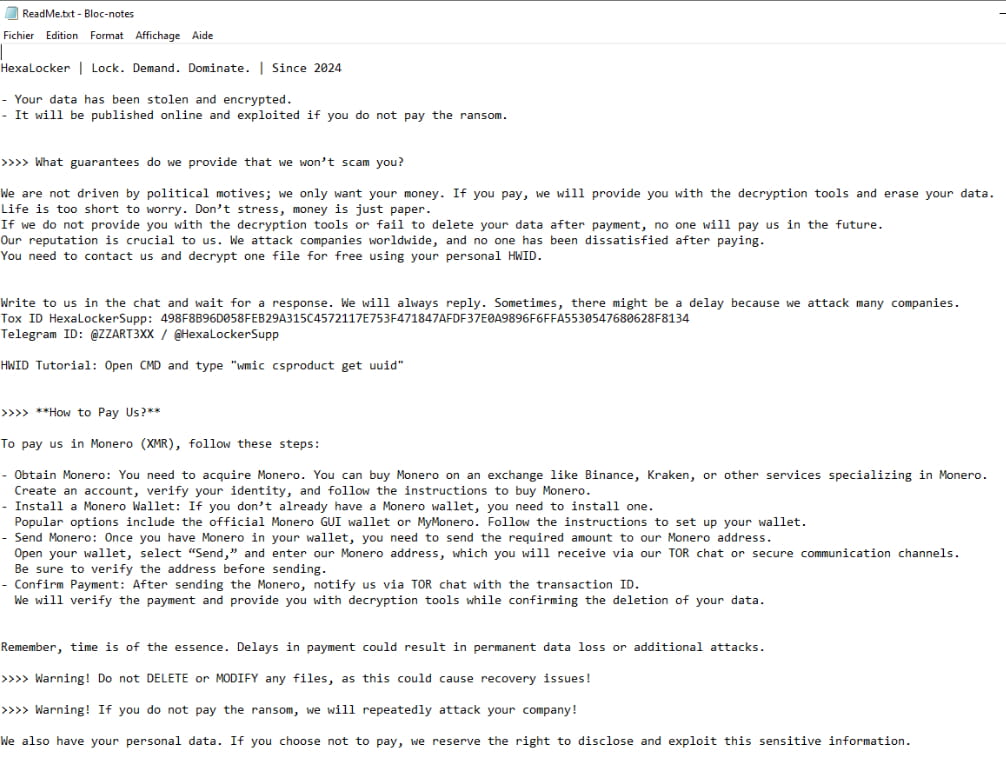
The ransomware works by recursively encrypting files in the victim's user directory using AES-256-GCM, a strong encryption standard. Notably, the decryption keys are sent to a remote server, which lacks the usual protections of asymmetric cryptography, raising concerns about the security and reliability of the ransom process. Additionally, HexaLocker steals files before encrypting them, compressing the stolen data into a zip file, and transmitting it to a remote server. Known as ‘double extortion,' this tactic is now very common in the ransomware space.
Synacktiv
The emergence of HexaLocker signifies an evolution in tactics by former members of LAPSUS$. While LAPSUS$ was once thought to be defunct, the appearance of HexaLocker under the administration of one of its former leaders suggests that the group's influence and operations may continue under new guises. The affiliation between HexaLocker and other ransomware groups, such as a newly formed gang called DoubleFace, indicates a potential for increased collaborative attacks, potentially targeting large-scale organizations.
Organizations are advised to stay vigilant and employ robust cybersecurity measures to mitigate the threat posed by HexaLocker. Monitoring network traffic for suspicious activity, particularly for outbound connections to known malicious servers, is crucial. Finally, maintaining isolated or offline backups of your most important data and verifying the copies regularly is a solid strategy against any ransomware.







Leave a Reply