
A months-long campaign leveraged altered builds of the open-source password manager KeePass to deliver malware through deceptive advertisements.
The attackers used a custom-built loader, dubbed “KeeLoader,” based on KeePass source code, to exfiltrate password data and deploy Cobalt Strike beacons for further compromise.
The campaign came to light in February 2025 during an incident response involving the encryption of VMware ESXi infrastructure at a European IT provider. WithSecure's investigation revealed that the attackers had altered KeePass source code and recompiled it with valid digital signatures, producing malicious versions of the KeePass installer and associated binaries. These trojanized builds were distributed via malvertising chains on search engines such as Bing and DuckDuckGo, leading users to typosquatted domains designed to mimic the official KeePass site.
Malicious KeePass clone
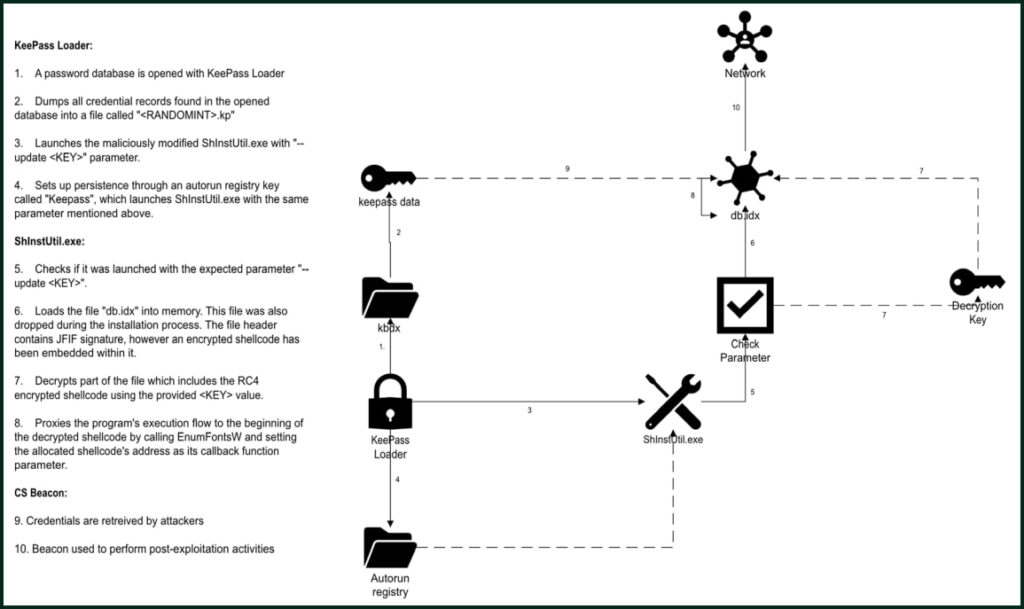
KeePass is a widely used open-source password manager, trusted for its local storage model and transparent codebase. By tampering with the source code, attackers were able to add malicious functionality directly into the KeePass binaries. Specifically, the modified installer dropped two key executables — KeePass.exe and ShInstUtil.exe — into the user's %localappdata% directory. These binaries included added logic to extract credentials from KeePass databases and create persistence by launching a Cobalt Strike payload named db.idx, which masqueraded as a JPG file.
KeeLoader's malicious capabilities extended beyond simple credential theft. When a database was opened, the malware exported login credentials, URLs, and comments to a local CSV file, which could later be exfiltrated through the Cobalt Strike beacon. This method bypassed many endpoint security tools by deferring beacon activation until after user interaction.
WithSecure
WithSecure traced the delivery vector to malvertising domains hosted on Cloudflare infrastructure and registered via Namecheap. These domains targeted users searching for software such as KeePass, WinSCP, and TreeSize Free, and redirected them through multiple intermediaries to ultimately download malware. The campaign's infrastructure overlapped with a known threat group tracked as UNC4696, which has links to Black Basta and BlackCat ransomware operations. However, the specific use of generic ransom notes and onionmail-based communication suggests that some affiliates may have broken away from these larger groups to conduct solo attacks.
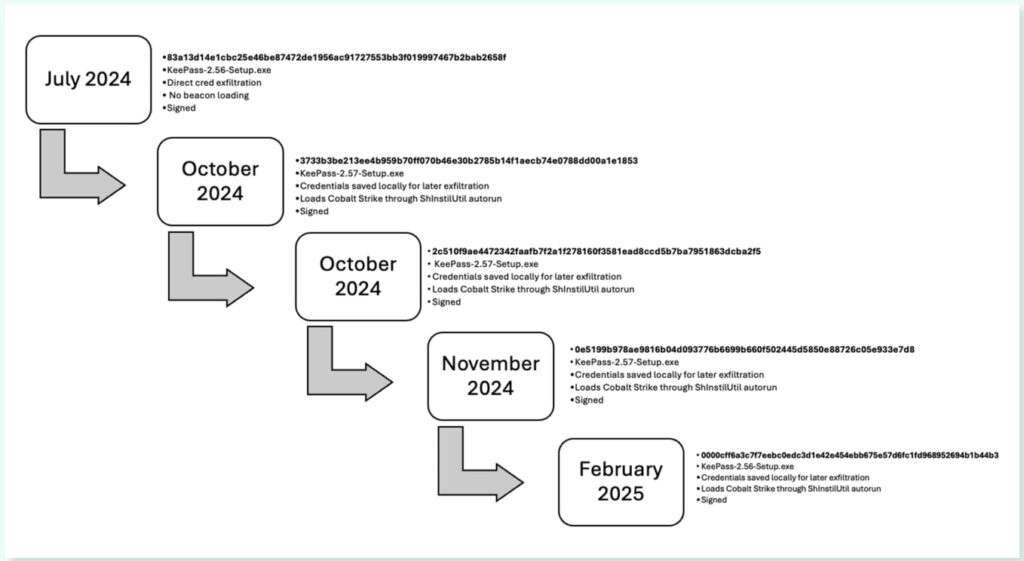
Five KeePass-based samples were discovered, dating back to mid-2024. These samples show iterative development, including the addition and later omission of direct exfiltration functions (IsUrlReady, RC4Apply) in favor of stealthier methods. All versions were signed with legitimate certificates from various companies, including MekoGuard, Shenzhen Kantianxia, AVARKOM LLC, and S.R.L. INT-MCOM — some of which were later revoked.
WithSecure
The attack demonstrates a significant evolution in software supply chain abuse, especially against open-source projects. Unlike past campaigns that simply bundled malicious files alongside legitimate applications, this case involved the complete recompilation of KeePass from source with embedded malicious functionality.
To minimize the risk of getting infected by such malware, avoid downloading software via search engine advertisements, and instead, verify URLs and use official sources.







Leave a Reply