
A new threat for iPhone users has emerged involving fake keyboards that look exactly like Apple’s default iOS keyboard and log everything typed on the device across all applications.
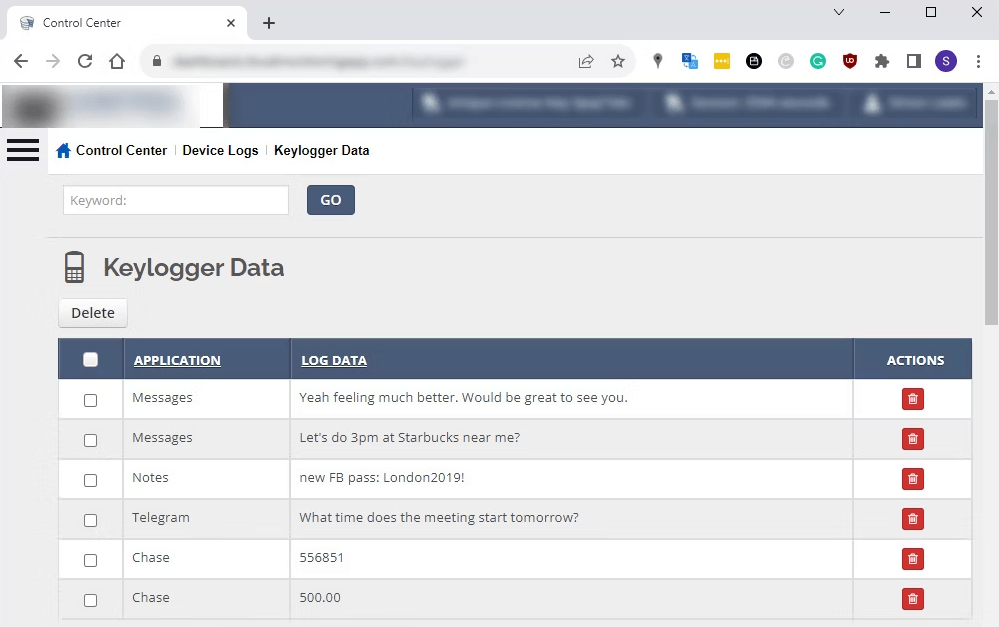
The logged data, which could include account passwords, two-factor authentication codes, private communications, internet searches, etc., is exfiltrated to a remote server accessible by the stalker/attacker via an online dashboard, allowing real-time monitoring of the victim’s activities.
According to a report by mobile security company Certo, these keyloggers are a trending threat in the iOS space right now, with cybercriminals selling them to stalkers for as little as $30.
Keyboard attack details
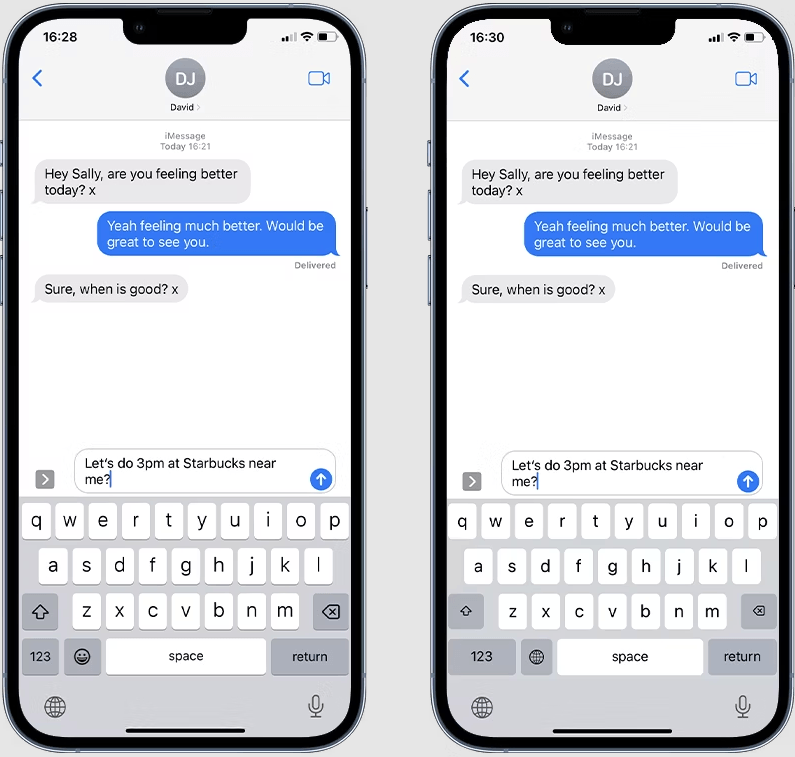
The attack begins with the installation of a custom keyboard on the target device, either by a stalker who has physical access or malware running on the device. Custom keyboards that aid with grammar, specialize in translations, or offer users rich collections of emojis, are common in the iOS app universe, but these malicious keyboard apps are designed to look exactly like Apple’s default keyboard, offering no additional functionality. This makes the threat extremely hard to spot, ensuring that the target continues to use their device normally.
Certo
After installing the keyboard clone, the attacker gives it ‘Full Access’ via Settings, meaning that it will be used across all apps opened on the device. This enables the keylogger app to capture user input from everywhere.
Captured information is sent to an online portal accessible via a panel from where the attacker can view logged data and the corresponding app it was recorded from.
How to protect yourself
iOS will not display a security warning about the malicious keyboard app because their authors abuse Apple’s TestFlight platform, which helps developers distribute beta apps for testing on the iOS platform.
TestFlight isn’t subject to the same security scrutiny as regular apps submitted for inclusion in the Apple App Store. However, the system still sees them as digitally signed and hence trustworthy. This is a loophole that iOS malware authors have been abusing for a while now, according to a Sophos report from August 2023. The FBI has also published a warning about this tactic earlier this year.
The only way iPhone users can protect themselves from these threats is by manually checking if they are using a custom third-party keyboard by navigating to “Settings > General > Keyboard > Keyboards.”
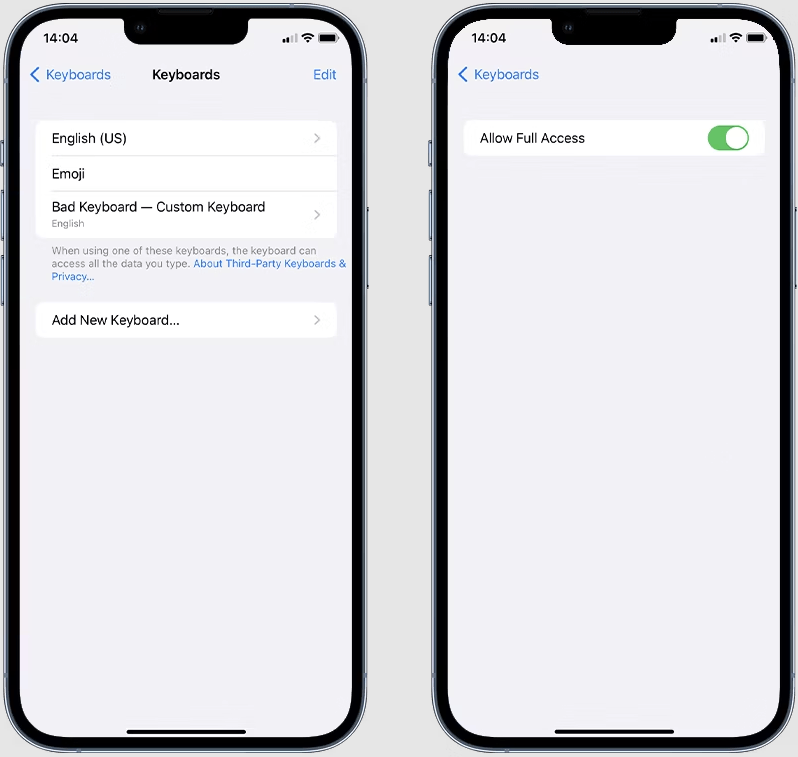
If you see any entries you don’t recognize on that screen, delete them and consider yourself compromised, meaning that your recent activities on the device might have been exposed to malicious actors.
Certos argues that Apple should introduce a security measure in the form of a notification to the user when a new keyboard with ‘Full Access’ permissions is installed on the iPhone, which could appear randomly a few hours post installation. Given that no such measure is in place right now, manual security checks are the only way to go.







Leave a Reply