
An infostealer campaign has been discovered by FortiGuard Labs, leveraging the CVE-2024-21412 vulnerability in Microsoft Windows SmartScreen. This vulnerability allows remote attackers to bypass security warnings and deliver malicious files, posing a high-severity risk to users.
The stealer campaign was uncovered and analyzed by FortiGuard Labs, led by researcher Cara Lin. The operation has been active over the past year, with threat actors including Water Hydra, Lumma Stealer, and Meduza Stealer exploiting the vulnerability.
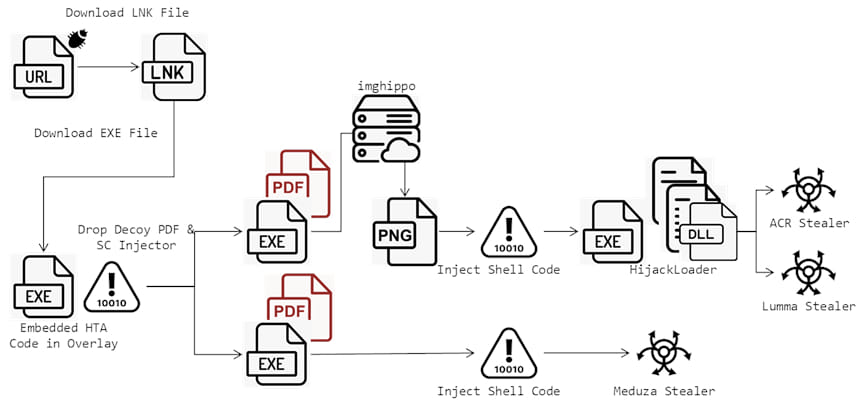
Attack chain
The attack begins with a crafted URL designed to download a malicious LNK file. When the victim clicks the link, the LNK file downloads an executable containing an HTA script. This script decodes and decrypts PowerShell code, retrieving final URLs, decoy PDF files, and a shell code injector. These files are designed to inject stealers into legitimate processes, sending stolen data to a command-and-control (C2) server.

Fortinet
The campaign targets users across various regions, including North America, Spain, and Thailand. The attackers employ different injectors and PDF files to evade detection. The LNK files invoke PowerShell via the “forfiles” command and execute “mshta” to fetch executable files from a remote server (e.g., hxxps://21centuryart.com).
Fortinet
Technical breakdown
Attackers use a malicious link to download a URL file, which in turn downloads an LNK file. The LNK file employs PowerShell and “mshta” to execute further malicious code.
Two variants of injectors are used. One variant downloads a PNG file from imghippo.com and decodes shell code using the Windows API. The other variant decrypts code and uses several Windows API functions for shell code injection.
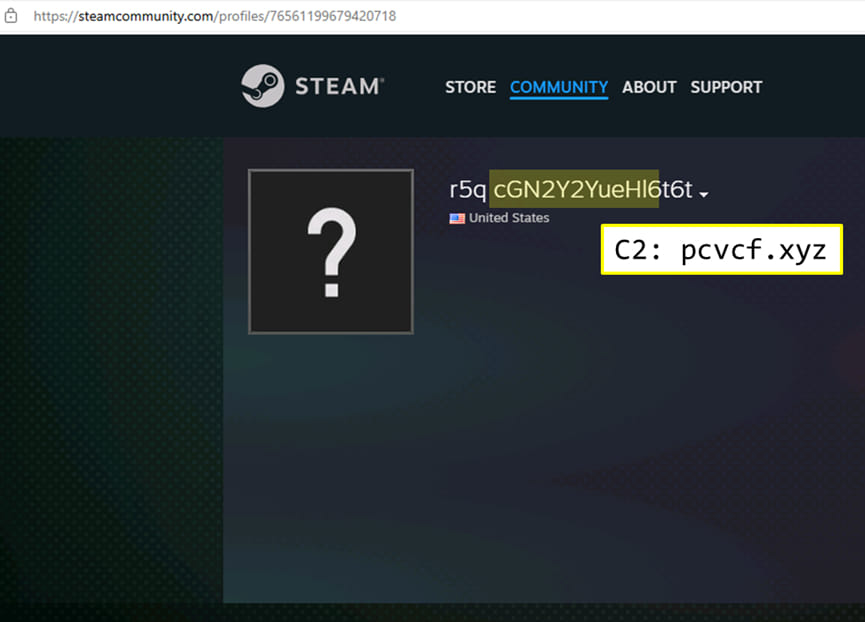
The campaign utilizes Meduza Stealer version 2.9 and the ACR stealer. Meduza Stealer's panel is found at hxxp://5[.]42[.]107[.]78/auth/login, while the ACR stealer uses dead drop resolvers on the Steam community website for C2 communication.
Fortinet
Defense recommendations
This stealer campaign exploits CVE-2024-21412 on Windows SmartScreen to propagate LNK files that download and execute malicious HTA scripts. The flaw was fixed in February 2024, so applying the latest Windows security update is enough to shut the door to the attackers.
If that is impossible, users should avoid clicking links and downloading files from untrusted sources. Additionally, it is recommended to implement stringent security measures, keep your antivirus up-to-date, and use network traffic monitoring tools that can catch suspicious activity.







Leave a Reply