
A recent report by Insikt Group presents the innovative use of infostealer malware data to identify 3,300 consumers of child sexual abuse material (CSAM). The malware logs data provides new avenues for law enforcement investigators to combat this heinous crime.
Methodology
The Insikt Group's proof-of-concept report leverages the vast trove of data from Recorded Future Identity Intelligence, focusing on infostealer malware logs. Infostealer malware, often spread through phishing, spam campaigns, and cracked software, captures a wide range of sensitive information from infected users, including login credentials, cryptocurrency wallets, and browser data. These logs are then sold on dark web markets, providing a unique dataset for tracking illegal activities.
Through detailed analysis of these logs, the researchers identified 3,300 unique users with accounts on known CSAM sources. Approximately 4.2% of these users had credentials for multiple sources, suggesting a higher likelihood of involvement in child exploitation crimes. This methodology highlights the potential of using cybercriminals' own tools against them.
Offenders identified
The report includes three detailed case studies, where infostealer data and open-source intelligence (OSINT) helped identify two individuals and unearthed additional digital artifacts, such as cryptocurrency addresses.
One case involved a user identified as “d****,” who was linked to multiple CSAM sites and found to have a history of child exploitation offenses, including a prior conviction in Ohio. Another case uncovered an individual known as “docto,” who was registered on nine CSAM websites. Despite having no prior convictions, this user was actively seeking opportunities to work with children and had a concerning online presence. The third case involved a user named “Bertty,” whose infostealer logs included cryptocurrency addresses linked to CSAM transactions, indicating involvement in the financial aspects of these illegal activities.
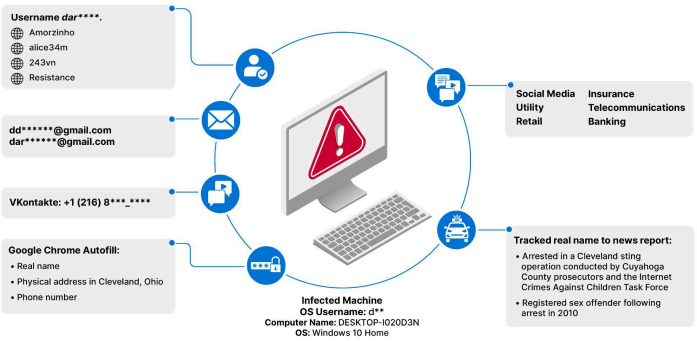
Recorded Future has escalated all relevant information to law enforcement agencies, emphasizing the actionable nature of these findings. The study also points to the growing demand for infostealer logs in the malware-as-a-service ecosystem, indicating a continuous stream of data that can be used for ongoing investigations.
Among the top sources identified were websites such as kidflix4m, alice34, and Amorzinho, each varying in content from forums to image-sharing and video-streaming platforms. Brazil, India, and the United States emerged as the top countries with users accessing these sources. This trend is likely influenced by high rates of software piracy in Brazil and the large populations of India and the U.S.
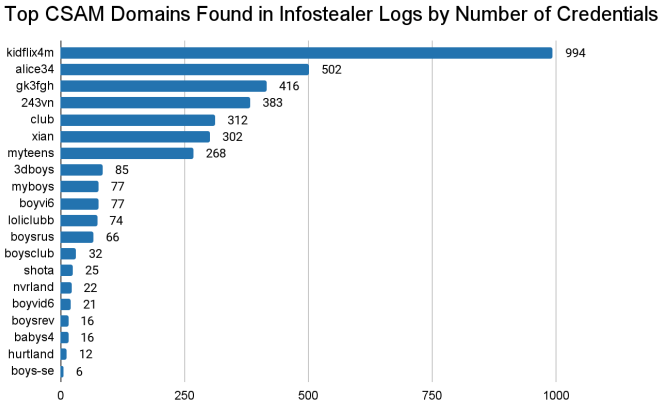
The use of infostealer logs in identifying CSAM consumers marks a significant advancement in cybersecurity and law enforcement collaboration. This approach not only uncovers the identities of those involved in child exploitation but also provides critical insights into the dark web's operational mechanisms.







Leave a Reply