
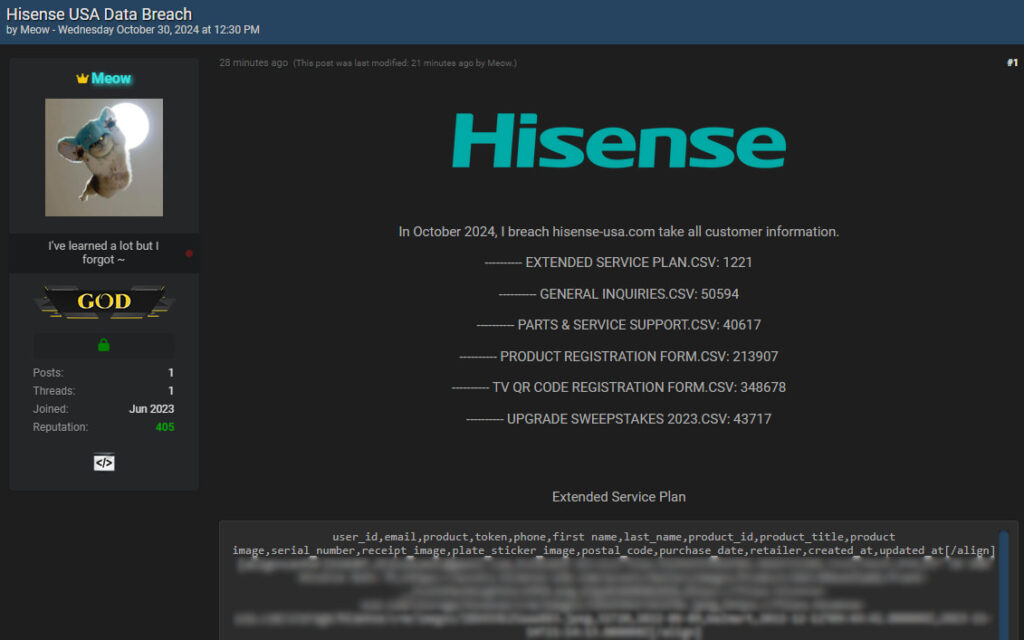
A threat actor claiming to have infiltrated Hisense USA’s database has posted samples of what they assert to be a large-scale data breach.
The post, published on the hacker forum BreachForums under the alias “Meow,” outlines a range of compromised files, reportedly containing personal and product-related information from customers who have registered products, participated in warranty and service plans, or submitted customer service inquiries.
The claimed breach affects a variety of sensitive data categories:
- Extended Service Plans: Over 1,200 records allegedly detailing customer names, emails, phone numbers, product types, serial numbers, purchase dates, and retailers.
- General Inquiries: Roughly 50,000 entries related to customer support and service requests, including customer names, contact information, and inquiry specifics.
- Parts and Service Support: Approximately 40,600 records reportedly listing personal and technical details tied to product support requests.
- Product Registration: Over 213,000 records containing customer data and product information submitted through registration forms.
- TV QR Code Registrations: More than 348,000 records of television registration data collected through QR code scans.
- Sweepstakes Entries: Close to 44,000 records from customers participating in product upgrade sweepstakes.
Hisense, a Chinese multinational corporation headquartered in Qingdao, is one of the world’s leading manufacturers of home appliances and electronics, with a strong presence in the U.S. market for smart TVs, home appliances, and various electronic products. Known for offering mid-range to high-end smart TVs, the brand competes with companies like Samsung, LG, and Sony, primarily in North America, Europe, and Asia. A breach of this nature poses significant reputational risk to the company, potentially eroding consumer trust and compliance reputation, especially in regions with strict data protection regulations.
Hisense has not yet issued a statement responding to the allegations, and our attempts to get a comment from the company were not immediately returned. Hence, the authenticity of the threat actor’s claims remains unconfirmed.
It’s worth noting, though, that the sample data includes specific, detailed fields, such as customer names, product serial numbers, retailer details, and even images tied to product registration. While the legitimacy of the breach is still doubtful, such highly structured and specific data can be a strong indicator of a genuine compromise.
For Hisense customers, exposure of this data could lead to targeted scams and unauthorized access attempts, as the data could potentially be used to impersonate Hisense support or exploit customers’ information for financial fraud. Customers are advised to:
- Check bank accounts for unusual or unauthorized transactions.
- Be wary of phishing emails or calls that may reference customer support issues, warranties, or products.
- Enable Two-Factor Authentication (2FA) on any Hisense-related or associated online accounts for added security.






Leave a Reply