
Troy Hunt, the cybersecurity expert behind the data breach notification platform Have I Been Pwned, has revealed that a phishing attack successfully compromised his Mailchimp account, exposing the email addresses of over 16,000 subscribers.
Hunt himself detailed the breach in a blog post published today. The incident unfolded in the early hours while he was jet-lagged in London. A deceptive phishing email directed him to a fake domain, mailchimp-sso.com, which mimicked Mailchimp's login portal. Hunt unknowingly submitted both his credentials and a one-time passcode (OTP) to the attacker's infrastructure, enabling immediate unauthorized access to his Mailchimp account.
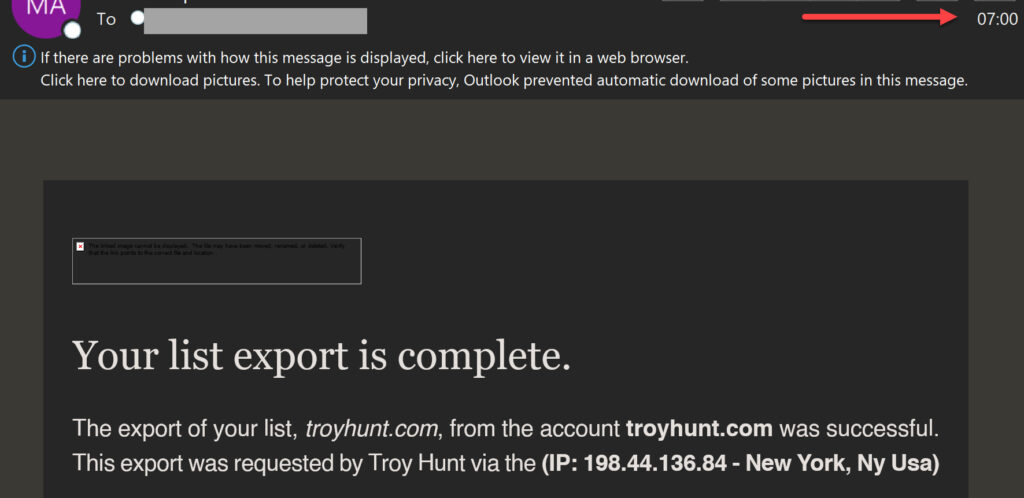
Shortly after the attacker logged in — first from Hunt's IP in London, then almost immediately from an IP address in New York — the subscriber mailing list was exported. The automated nature of the attack left little time for remediation before the data exfiltration occurred. Mailchimp later confirmed both the login and export events via notification emails.
The compromised data includes:
- Email addresses
- Subscription statuses
- Sign-up dates
- Associated IP addresses
- Approximate geolocation data
Hunt noted with concern that the export included over 7,500 unsubscribed users, raising questions about Mailchimp's data retention practices. He also identified a now-revoked API key that had been generated during the intrusion, suggesting the attacker may have attempted or intended to automate further access.
Troy Hunt
Mailchimp, a widely-used email marketing platform owned by Intuit, provides services to small businesses, creators, and large enterprises. It has been a frequent target of phishing campaigns due to its access to extensive user data and mailing infrastructure. While Mailchimp offers two-factor authentication (2FA) via OTP, Hunt pointed out that it remains vulnerable to real-time phishing relays, as demonstrated in this incident.
Hunt expressed frustration at falling for a scam despite his extensive background in cybersecurity. He attributed the lapse in part to fatigue, noting that the phishing message was subtle and believable enough to bypass his usual vigilance. The fact that his password manager, 1Password, did not auto-fill the credentials should have raised a red flag, but he dismissed it at the moment — a mistake he openly acknowledged in his write-up.
“We all have moments of weakness and if the phish times just perfectly with that, well, here we are,” Hunt reflected.
This incident underscores a critical reality in cybersecurity: even seasoned professionals can fall victim to phishing attacks. Sophisticated social engineering, well-crafted phishing pages, and real-time OTP relays can defeat traditional defenses. Hunt's experience serves as a reminder that technical knowledge alone isn't a guaranteed shield.
To minimize phishing risks, use phishing-resistant authentication such as passkeys or hardware security keys (e.g., YubiKey), which are immune to OTP relay attacks. Also, always verify domains carefully before entering credentials, especially for services that handle sensitive data. It is elementary to use password managers and treat failure to auto-fill as a warning sign. Ultimately, avoid taking action from emotionally charged emails — urgency, fear, and timing are common manipulation tactics in phishing campaigns.







Leave a Reply