
UpGuard has discovered an unprotected Elasticsearch database containing over 22 million web request records, nearly all of which were tied to Leakzone.net, a prominent forum for sharing hacking tools, stolen credentials, and other illicit content.
The unsecured server was discovered on July 18, 2025, during a routine internet scan conducted by the UpGuard research team. The database was unauthenticated, allowing anyone to access its contents without credentials. Each entry contained granular details of individual web requests, including:
- Destination domain
- IP address of the requester
- Request size
- Metadata such as geolocation and ISP information
Notably, 95% of the records pointed to traffic directed at Leakzone.net, with the remaining spread thinly across 280 other domains, including sites like Accountbot.io.
Leakzone has become a central hub in the evolving ecosystem of cybercrime forums. While predecessors like Raid Forums and Breach Forums were dismantled by law enforcement, Leakzone has remained resilient. The site has hosted trading of compromised account data, pirated software, and cracking utilities since gaining traction in 2020. Despite public awareness and legal pressure, it continues to operate openly on the clear web.

UpGuard
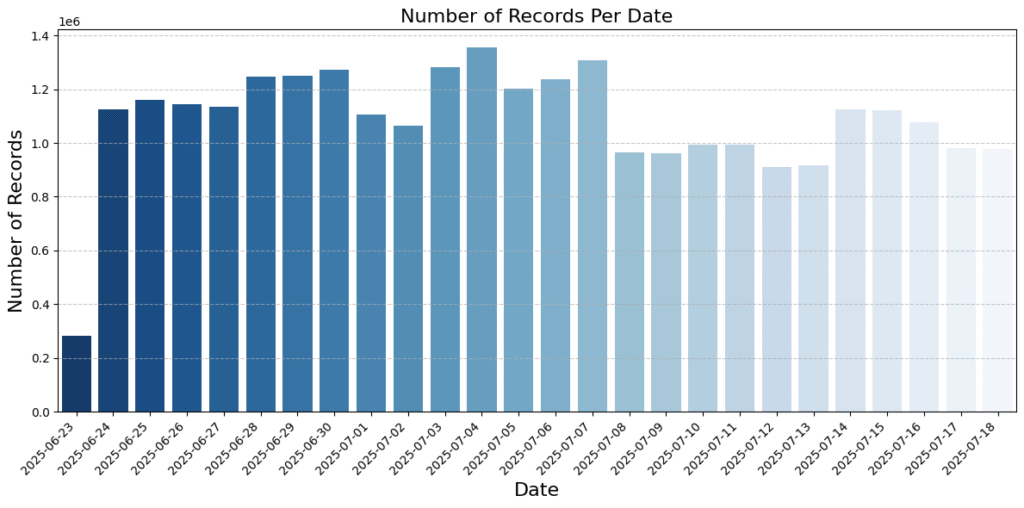
To validate the nature of the leak, UpGuard created a Leakzone account and confirmed that their own IP address appeared in the logs, proving the records were accurate reflections of site traffic. The logs covered a three-week period from June 25 to mid-July 2025, documenting about one million requests per day with a median size of 2.8 KB. The data offers an unusual window into the behavior of users engaging with a known cybercrime platform.
UpGuard
Among the dataset's 185,000 unique IP addresses, many did not correspond to individual users. UpGuard observed indicators of obfuscation techniques, around 5% of the traffic was routed through public proxies, and several IPs were associated with VPN providers such as Cogent Communications. A bell-shaped distribution in request frequency revealed a cluster of heavily used VPN exit nodes, suggesting shared infrastructure commonly used for anonymity.
Interestingly, a significant portion of traffic originated from major cloud providers, including Amazon Web Services, Google Cloud, and Microsoft Azure. This is consistent with patterns of VPN use, bot scraping activity, and cloud-hosted anonymization tools. Traffic from China was notably absent, suggesting that users in restricted regions are using overseas proxies to mask their location. In some cases, providers like Huawei Cloud appeared in the logs, but with server locations listed in places like Singapore.
Further analysis revealed that 39% of IP addresses appeared only once in the logs. These one-off visits likely represent genuine client IPs from users connecting without additional privacy measures, possibly unaware of the visibility of their activity.
Despite the illegal nature of many exchanges on Leakzone, not every visitor to the site can be presumed malicious. Cybersecurity professionals, journalists, and researchers often monitor such platforms for threat intelligence. Some of the most active IP addresses could, in fact, belong to automated tools operated by these groups. Still, the leak illustrates the inherent fragility of online anonymity, even for those relying on proxies or VPNs.







Leave a Reply