
The Russian-aligned APT group Curly COMrades are deploying hidden Alpine Linux virtual machines (VMs) on compromised Windows hosts via Microsoft Hyper-V.
The technique allows attackers to isolate their malware from host-based detection tools and maintain long-term covert access.
The operation was discovered in mid-2025 during a joint investigation by Bitdefender and the Georgian CERT, when suspicious activity was traced back to a compromised Georgian website that was also serving as an attacker-controlled proxy. The deeper forensic analysis revealed a previously undocumented strategy of using native Windows virtualization to run stealthy Linux-based malware, avoiding the reach of traditional endpoint defenses.
Hyper-V as a launchpad for Linux malware
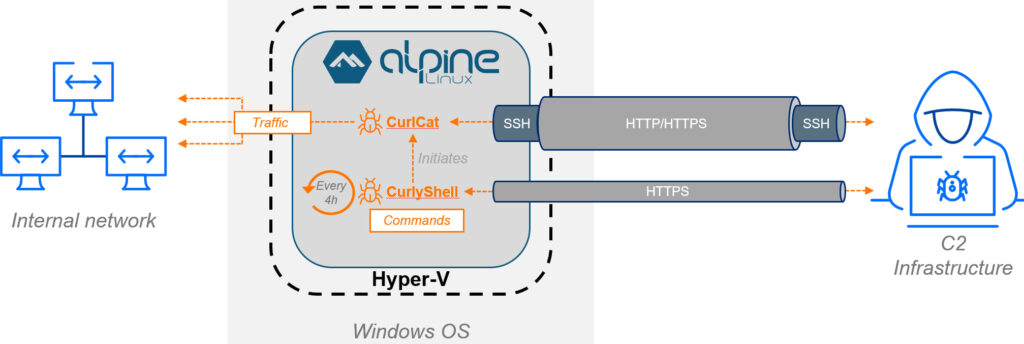
On compromised Windows machines, attackers remotely enabled the Hyper-V role and disabled its management interface to reduce visibility. They then downloaded a compressed virtual machine image, masquerading as a video file, and extracted it using WinRAR, ultimately importing it into Hyper-V via PowerShell. The VM was deceptively named “WSL” (a nod to the Windows Subsystem for Linux) but was, in reality, a standalone Linux environment.
Running Alpine Linux, the virtual machine was both small (120MB disk footprint) and low-memory (256MB RAM), making it unlikely to trigger host-based alerts. It used Hyper-V's Default Switch networking, allowing all outbound traffic from the VM to appear as if originating from the Windows host's IP address, a technique that further obscures malicious activity.
Within this concealed Linux environment, two custom malware implants were deployed:
- CurlyShell: A persistent reverse shell written in C++, responsible for command execution. It maintains persistence via a root-level cron job and uses HTTPS for C2 communication. The malware obfuscates its traffic using a non-standard Base64 encoding scheme.
- CurlCat: A stealth reverse proxy tool that wraps SSH traffic inside HTTP requests. It's launched on-demand via CurlyShell and facilitates tunneled communication over SOCKS proxies, authenticating to remote servers using hardcoded RSA keys.
Both implants are compiled as ELF binaries and share a common codebase built around the libcurl library. Their minimalist design enables long-term operation with a minimal forensic footprint.
Bitdefender
Outside the VM, attackers used a flexible arsenal to sustain access and pivot through victim networks.
On the Windows hosts, the attackers used a PowerShell script (kb_upd.ps1) to inject encrypted Kerberos tickets into LSASS, enabling remote command execution and lateral movement via SMB. Persistence was maintained through another GPO-distributed script that created or reset local accounts with hardcoded credentials. To ensure reliable communication, they also deployed tunneling tools like Ligolo-ng, Resocks, Stunnel, and CCProxy, alongside CurlCat, reflecting a flexible, layered approach to remote access.
Artifacts were frequently stored under C:\Windows\ps1\ or C:\ProgramData\, blending into legitimate Windows system directories.
Security teams should audit Hyper-V usage across endpoints and disable the role where unnecessary. It is also advisable to monitor for hidden VMs and unexpected imports using PowerShell and WMI activity, and enable host-based network inspection, especially on systems with virtualization enabled.







Leave a Reply