
A newly discovered phishing campaign targeting Microsoft 365 accounts has been attributed to Russian-linked threat actors, leveraging an advanced technique known as device code authentication phishing.
Reports from both Microsoft and cybersecurity firm Volexity indicate that multiple groups have been exploiting this method since mid-2024, targeting government agencies, NGOs, defense organizations, and private companies across Europe, North America, Africa, and the Middle East.
Microsoft Threat Intelligence first identified an ongoing device code phishing operation by a group it tracks as Storm-2372. The campaign, active since at least August 2024, involves attackers masquerading as users of messaging applications like WhatsApp, Signal, and Microsoft Teams. Victims receive fake meeting invitations or messages from seemingly legitimate contacts, leading them to an official Microsoft login page where they unknowingly authenticate an attacker-controlled session.
Volexity
Microsoft assesses Storm-2372 as a nation-state actor aligned with Russian geopolitical interests, based on the group’s tactics, targeting scope, and victimology. Meanwhile, Volexity’s independent research found that at least three separate Russian threat groups — identified as CozyLarch (APT29), UTA0304, and UTA0307 — have been deploying similar attacks since January 2025, further confirming the widespread nature of this technique.
Volexity
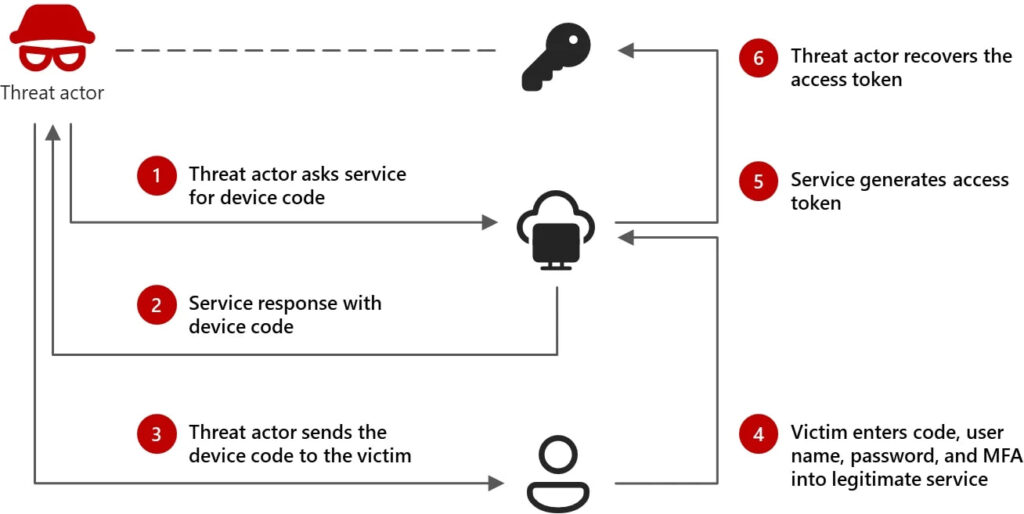
Device code phishing workflow
Device code authentication is a legitimate feature used for logging into Microsoft services from devices that lack interactive web browsers, such as smart TVs and IoT devices. The attack exploits this process as follows:
- Attackers generate a device code: The adversary creates a valid authentication request on Microsoft’s device login portal.
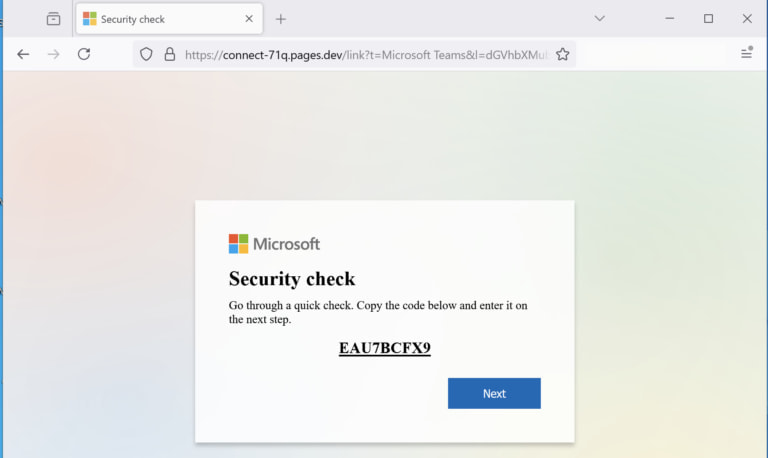
- Targeted social engineering: Victims receive phishing emails or messages impersonating government officials, journalists, or research institutions, prompting them to enter the provided code into the legitimate Microsoft sign-in page.
- Session hijacking: Once the victim authenticates, the attacker captures the access token, gaining control over the user’s Microsoft 365 account without needing credentials.
- Lateral movement and data theft: The attackers then exploit access to search for sensitive data, send additional phishing emails within the organization, and exfiltrate emails or cloud-stored documents.
Unlike traditional phishing, this method bypasses standard multi-factor authentication (MFA) and leaves minimal traces in security logs, making it highly effective and difficult to detect.
Microsoft
Tactics and victimology
Volexity’s research provides additional insight into how Russian actors have been executing these attacks. The campaigns often involve masquerading as government and diplomatic entities, impersonating officials from the U.S. Department of State, Ukrainian Ministry of Defense, European Parliament, and other prominent institutions.
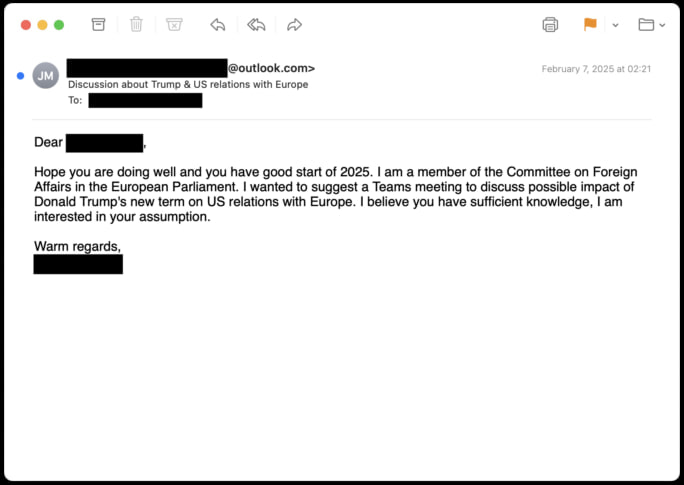
Victims have been approached with invitations to discussions on geopolitical topics, including U.S.-EU relations, China’s foreign policy, and NATO affairs.
Execution differs per threat actor. According to Volexity, the following tactics are followed from each threat group:
- UTA0304 created a fake secure chat platform, directing victims to an attacker-controlled Element messaging server.
- CozyLarch (APT29) sent fake invitations to join a U.S. State Department Microsoft Teams meeting.
- UTA0307 built a fake Microsoft login page that generated real-time device authentication codes to trick users into providing access.
These highly targeted spear-phishing efforts have led to successful compromises of Microsoft 365 accounts, with attackers using automation tools like Python-based scripts to rapidly exfiltrate data.
Both Microsoft and Volexity have taken steps to alert affected organizations and mitigate the ongoing threat. Microsoft has issued notifications to targeted users and is actively monitoring for suspicious authentication attempts. Additionally, Volexity has linked several domains and email addresses to these campaigns, providing threat intelligence to security teams.







Leave a Reply