
A critical vulnerability identified as CVE-2024-3273 found in certain end-of-life D-Link NAS devices is reported as actively exploited by threat actors who are openly sharing IP addresses of vulnerable devices on underground forums.
The flaw was discovered and reported by an independent researcher roughly two months back. At the time, the analyst warned that there were over 92,500 internet-exposed devices that seemed vulnerable to the particular flaw, offering cybercriminals a comfortably large attack surface.
The vulnerability was added to CISA's Known Exploited Vulnerabilities catalog on May 2, 2024, highlighting its critical nature and the urgent need to address the risk in critical environments.
Today, a report by Cyfirma confirms there is active exploitation in the wild, unfortunately involving a large number of cybercriminals.
CYFIRMA
Exploitation details
CVE-2024-3273 affects several D-Link NAS models, specifically DNS-320L, DNS-325, DNS-327L, and DNS-340L, and potentially all end-of-life NAS devices from D-Link. This issue, primarily due to hard-coded credentials and command injection flaws, can lead to unauthorized access, data theft, system modifications, and denial-of-service attacks.
Attackers have been observed exploiting this vulnerability through CGI binaries such as nas_sharing.cgi and orospucoc.cgi. These binaries allow the execution of arbitrary commands due to a pre-configured system user named “messagebus,” which has no password. By crafting HTTP GET requests with base64 encoded payloads, attackers can gain root access to the affected devices.
Successful exploitation can result in full system compromise, data exfiltration, and the integration of the device into a botnet.
Impact and mitigation
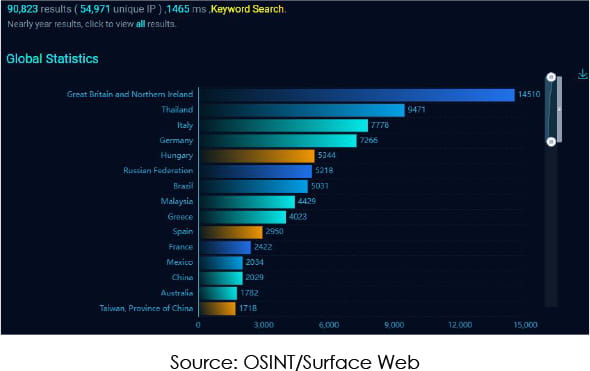
The vulnerability's impact is significant, with tens of thousands of hosts remaining exposed. Affected devices are widely used for data backup and storage, making the exploitation risks particularly high for sectors such as banking, healthcare, and software manufacturing.
CYFIRMA
Given that D-Link cannot support these end-of-life products, users must take immediate action:
- Decommission vulnerable D-Link NAS devices to prevent further exploitation.
- Isolate vulnerable devices from critical networks.
- If third-party firmware is available, consider upgrading, but note that D-Link does not support third-party firmware.
- Disable or restrict access to vulnerable CGI binaries.
The active exploitation of CVE-2024-3273 in D-Link NAS devices underscores the critical need for immediate action to secure data and infrastructure. Organizations must prioritize replacing or retiring these vulnerable devices and implementing robust security measures to mitigate the risks associated with this vulnerability.







Leave a Reply