
Mandiant, a Google company, has revealed details about a critical zero-day vulnerability in Fortinet’s FortiManager, tracked as CVE-2024-47575, which has been actively exploited by a new threat group known as UNC5820.
The vulnerability allows attackers to take control of compromised FortiManager devices, enabling them to stage and exfiltrate sensitive configuration data from FortiGate firewalls managed by these devices.
CyberInsider reported about the active exploitation of the same flaw yesterday, before Fortinet had publicly disclosed it, but more details have emerged now.
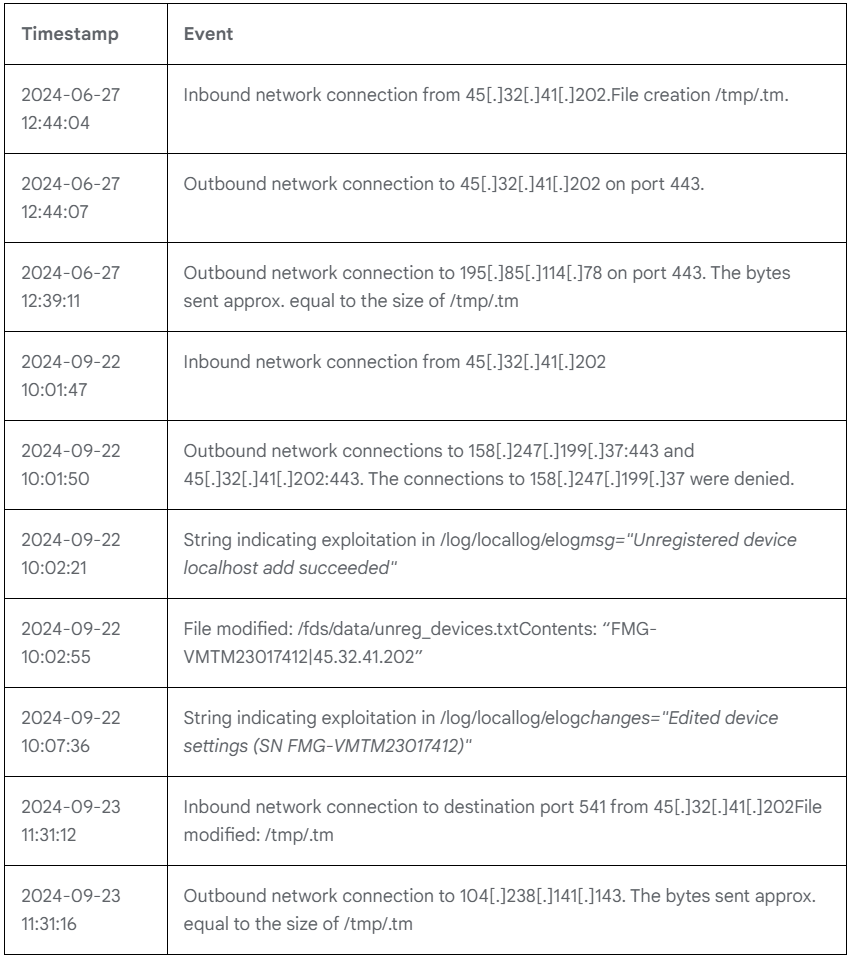
Mandiant, in collaboration with Fortinet, identified over 50 compromised FortiManager appliances across various industries, with the first signs of exploitation dating back to June 2024.
The flaw, linked to FortiManager’s management of FortiGate devices, enables attackers to execute arbitrary code by registering unauthorized devices with FortiManager. Once the devices are connected, the attackers can access critical configuration files, including hashed user passwords and network policies, which can facilitate further lateral movement within enterprise environments. However, Mandiant has not found evidence that UNC5820 has used the exfiltrated data for broader compromise, at least at this stage of the investigation.
The exploitation began with inbound network connections to FortiManager devices, notably from IP addresses such as 45[.]32[.]41[.]202 and 195[.]85[.]114[.]78, which were used to stage configuration files into a compressed archive. These files contained detailed network information, including FortiGate serial numbers, IP addresses, and firewall policies. A second wave of attacks followed in September 2024, involving similar tactics and indicators.
Mandiant (Google)
Fortinet is a major player in the network security space, and its FortiManager platform is widely used by enterprises and managed service providers (MSPs) to control large deployments of FortiGate firewalls. Given its central role in network management, vulnerabilities in FortiManager have significant implications, as compromising a single instance can lead to the potential exposure of all associated devices, making attacks like this particularly damaging for large networks.
Despite the severity of the situation, Mandiant has not yet been able to determine the precise methods UNC5820 used to exploit the vulnerability, nor have they attributed the group to a specific nation-state or criminal organization. However, the compromise of FortiManager devices and the lack of clear actor motivation underscore the importance of securing vulnerable systems immediately.
Mitigation steps:
- Limit access to the FortiManager admin portal to approved internal IP addresses only.
- Enable a configuration that denies unknown FortiGate devices from being associated with FortiManager.
- Immediately update FortiManager to the fixed versions: 7.2.5, 7.0.12, 7.4.3, or later.







Leave a Reply