
The Chrome Security Team has announced that starting with Chrome 127, certificates issued by Entrust and AffirmTrust will no longer be trusted if their earliest Signed Certificate Timestamp (SCT) is dated after October 31, 2024.
This move aims to uphold the integrity of the Web PKI ecosystem and protect Chrome users from potential security risks associated with non-compliant Certificate Authorities (Cas).
Background and rationale
Certificate Authorities (CAs) are critical to internet security because they issue digital certificates that verify the authenticity of websites, enabling encrypted connections between browsers and web servers. This encryption ensures that data transmitted between users and websites remains private and secure.
Users should care about using trusted certificates because they provide assurance that the website they are interacting with is legitimate and has not been tampered with by malicious actors. Without trusted CAs, the risk of data breaches, phishing attacks, and other security threats increases significantly, undermining the overall trust and safety of online interactions.
In a post published on its security blog space, Google explained that the decision to implement this block stems from a series of publicly disclosed incident reports that revealed concerning behaviors by Entrust over the past several years.
These behaviors, which include compliance failures and unmet improvement commitments, have eroded confidence in Entrust's competence, reliability, and integrity as a CA. As CAs play a critical role in securing encrypted connections on the internet, their failure to meet security and compliance standards poses significant risks for users, which Google finds unacceptable.
Affected certificates
The distrust will specifically affect TLS server authentication certificates validating to the following Entrust roots:
- Entrust Root Certification Authority – EC1
- Entrust Root Certification Authority – G2
- Entrust.net Certification Authority (2048)
- Entrust Root Certification Authority (2006)
- Entrust Root Certification Authority – G4
- AffirmTrust Commercial
- AffirmTrust Networking
- AffirmTrust Premium
- AffirmTrust Premium ECC
Certificates issued by these roots before October 31, 2024, will remain trusted. However, any certificates issued after this date will be distrusted by default starting November 1, 2024, when Chrome 127 is expected to be released. This will apply across all platforms where Chrome operates, except for iOS due to Apple's policies.
Scope of impact
Starting from November 2024, Chrome will stop loading sites with certificates issued by Entrust or AffirmTrust after October 31, 2024, unless users or enterprises explicitly trust these certificates through local settings. Affected websites will display a security warning, preventing users from accessing them until the certificates are replaced, or if the user specifically chooses to proceed nonetheless.
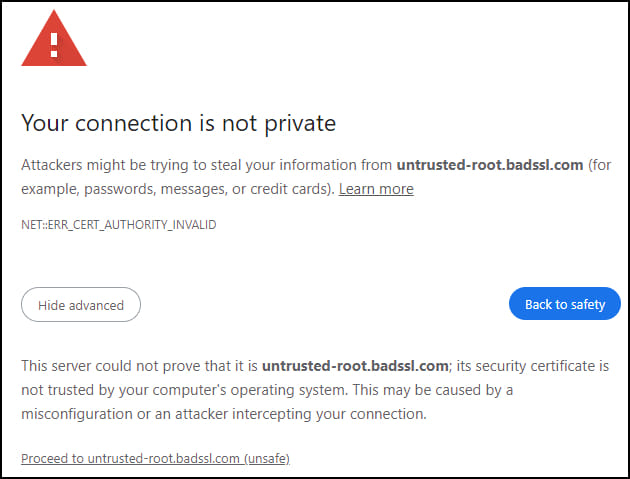
RestorePrivacy
Entrust and AffirmTrust are significant players in the digital certificate market, and it's estimated that thousands of websites currently use certificates issued by these authorities, so the impact for internet users could be significant. This concerns not only sites people directly attempt to access, but also APIs and other online services using those certificates.
Chrome's built-in Certificate Viewer tool can help users determine if a website's certificate is affected by Google's decision.
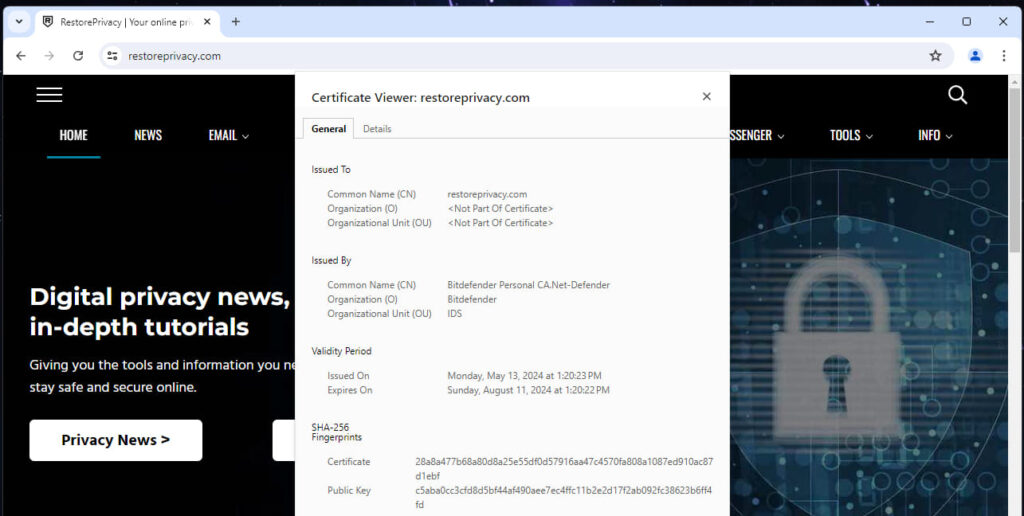
For website operators, Google suggests that they move quickly to identify if they use certificates from Entrust or AffirmTrust, obtain and install new certificates from a trusted CA included in the Chrome Root Store before October 31, 2024. Finally, it’s important to test the new configurations by using command-line flags in Chrome 128 (available in Canary/Dev) to simulate the SCTNotAfter distrust constraint and ensure the new certificates work correctly.






Which is why I stopped using Chrome close to a decade ago. I didn’t like that I was using Google everything. While I use their mail, calendar, and contact services, I use third party apps to utilize them. I use open source whenever possible (support as well), and buy third party apps.
The link posted [EX:bugzilla-mozilla-org-buglist] on Entrust was opened back in 2015-11-01, with 59 bugs found since then.
What could be the real reasons after all this time, Google now finds Entrust and AffirmTrust digital certificates issued by these authorities, unacceptable?
In the ‘Criticism’ section at [https://en.m.wikipedia.org/wiki/Public_key_infrastructure]
Web browser implementation of HTTP/2 including Chrome, Firefox, Opera, and Edge supports HTTP/2 only over TLS by using the ALPN extension of the TLS protocol.
This would mean that, to get the speed benefits of HTTP/2, website owners would be forced to purchase SSL/TLS certificates controlled by corporations.
Currently the majority of web browsers are shipped with pre-installed intermediate certificates issued and signed by a certificate authority, by public keys certified by so-called root certificates. This means browsers need to carry a large number of different certificate providers, increasing the risk of a key compromise.
When a key is known to be compromised, it could be fixed by revoking the certificate, but such a compromise is not easily detectable and can be a huge security breach. Browsers have to issue a security patch to revoke intermediary certificates issued by a compromised root certificate authority.
What other checks and balances in this digital age can a simple user trust besides big tech?
Google’s control over our internet use is significant, it is essential to note that the company’s dominance is not absolute. But this move, is yet just another feather in its hat to gain full dominance over the internet.
Google’s control over any internet use is multifaceted and extensive. Here are some key points that highlight its dominance today:
– Search Engine Dominance:
Google processes over 90% of all internet searches, making it the primary gateway to the internet for many users. This gives Google immense control over what information is accessible and visible to the public.
– Android Operating System:
Google develops the Android mobile operating system, which is used by over 70% of the world’s smartphones. This allows Google to control the user experience and integrate its services seamlessly into the operating system.
– YouTube:
Google owns YouTube, the largest video-sharing platform, which accounts for over 2 billion monthly active users. This gives Google significant control over online video content and distribution.
– Google Earth:
Google Earth, launched in 2005, allows users to access high-definition satellite images from around the world, further solidifying Google’s presence on the internet.
– Internet of Things (IoT):
Google develops and manufactures smart devices, such as smartwatches, TVs, and cars, which are connected to the internet. This expands Google’s reach and control over the internet of things.
– Investment and Partnerships: Google has invested in and partnered with various companies, giving it influence over their products and services. This includes investments in companies like YouTube, Android, and other startups.
– Data Collection and Analysis: Google collects vast amounts of user data through its services, allowing it to analyze user behavior, preferences, and interests. This data can be used to influence online advertising, content creation, and product development.
– Algorithmic Control:
Google’s algorithms play a significant role in determining what content is displayed, recommended, and promoted online. This algorithmic control can influence the visibility and accessibility of certain information, shaping the online discourse and user experience.
The dominance of Googles internet control over other companies, limits and restricts our substantial presence of other venues on the internet, and Googles ongoing efforts are not helping to promote internet diversity and decentralization!
Hmm. Many government organizations/departments still use Entrust via Microsoft Edge. But that’s ok, they have ample public funds at taxpayer expense.
Flip the coin, try to understand why the American public is on the hook always…when the top 1% privilege, inordinate, socioeconomic powers get off scott-free. Yes, the tax payers voice needs spoken loudly with contempt, when people who have a duty to act on behalf of others, such as elected officials with a duty to serve their constituents’ interests or more broadly the public good.
Instead act in corrupting the law in order to serve their own interests with the receipt of bribes, and the receipt of unlawful gratuities, by these federal public officials. That sell/hire positions that serve the interests of some private parties only!
The failure of government officials to serve the public interest as a consequence of lobbying by special interests who provide benefits to the official is an example of agent misdirection. That is why lobbying is seen as one of the causes of a democratic deficit. Boiled down rendering a real conspiracy to defraud the United States tax payer.