
A new report from iVerify has revealed a far-reaching global surveillance threat enabled by China’s state-owned telecom interconnect providers.
By exploiting outdated mobile signaling protocols, entities such as China Mobile International (CMI) and China Telecom Global have gained alarming access to sensitive mobile communications worldwide, with implications ranging from mass user profiling to covert malware delivery.
Routing sensitive data through sanctioned entities
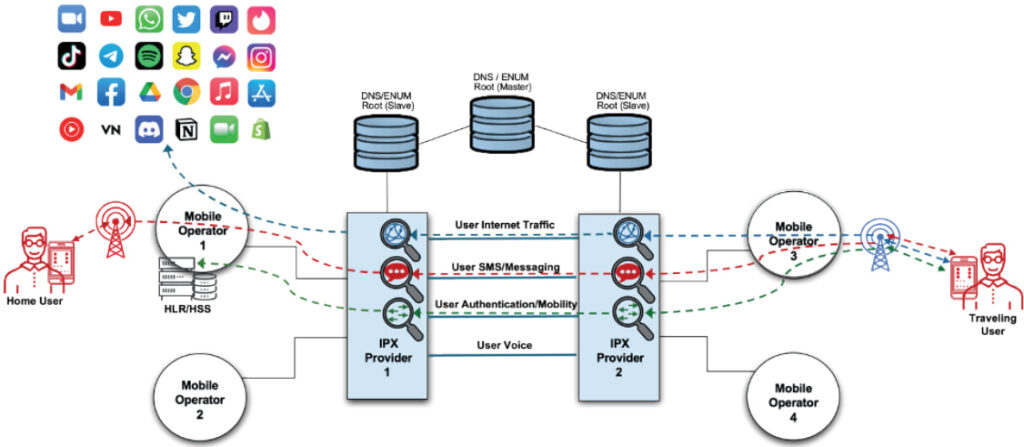
The investigation, led by researchers Gary Miller of the Citizen Lab and Daniel Kelley of the iVerify Threat Research Team, examined operational documents and GSMA data submissions to uncover the scale of this threat. Their findings show that at least 60 mobile operators across 35 countries — including key U.S. allies and intelligence partners — rely on Chinese interconnect networks for critical mobile functions. These include call setup, SMS delivery, device authentication, and data routing.
iVerify
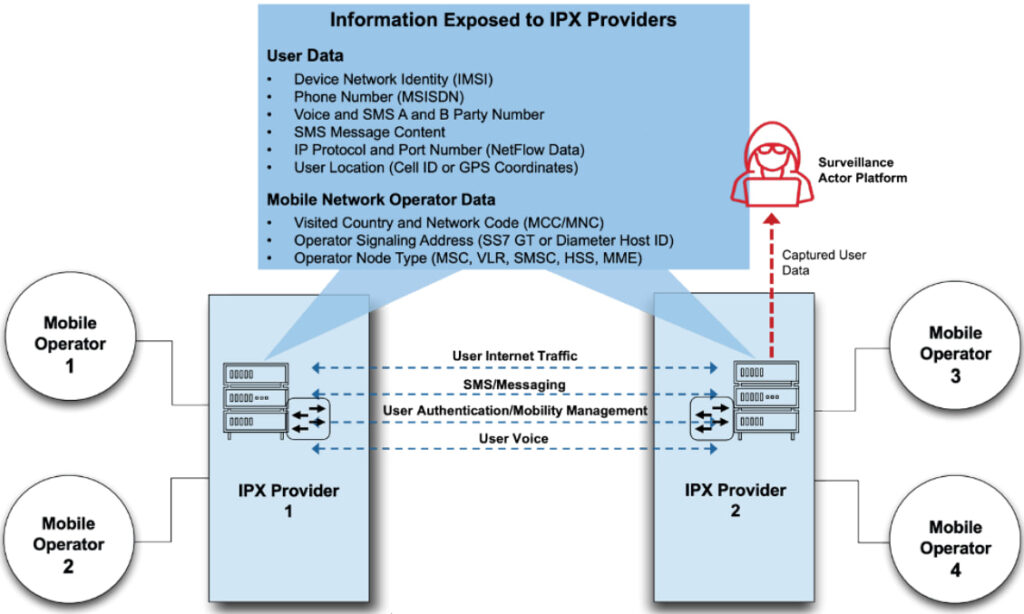
The detailed report sheds light on how these interconnect providers, embedded in the international IPX and SS7 backbone networks, act as “data-in-the-middle” surveillance points. They facilitate both passive data harvesting and active signaling manipulation, granting state-aligned threat actors in China real-time access to a wealth of mobile user data. This includes location tracking, app usage patterns, and behavioral profiling, often without user awareness or operator detection.
iVerify
Notably, mobile operators in countries such as New Zealand, South Korea, Japan, and several Southeast Asian nations — including Taiwan — use China-based networks like CMI and CITIC Telecom International. Some of these operators simultaneously deploy Huawei or ZTE core network equipment, creating an end-to-end surveillance surface that combines hardware-level access with unencrypted data transport.
The report outlines how attackers exploit interconnect infrastructure in three primary ways:
- Passive Surveillance: Using deep packet inspection (DPI) tools, state actors can collect unencrypted traffic data to build detailed user profiles—identifying co-travelers, inferring socioeconomic status, and monitoring VPN usage.
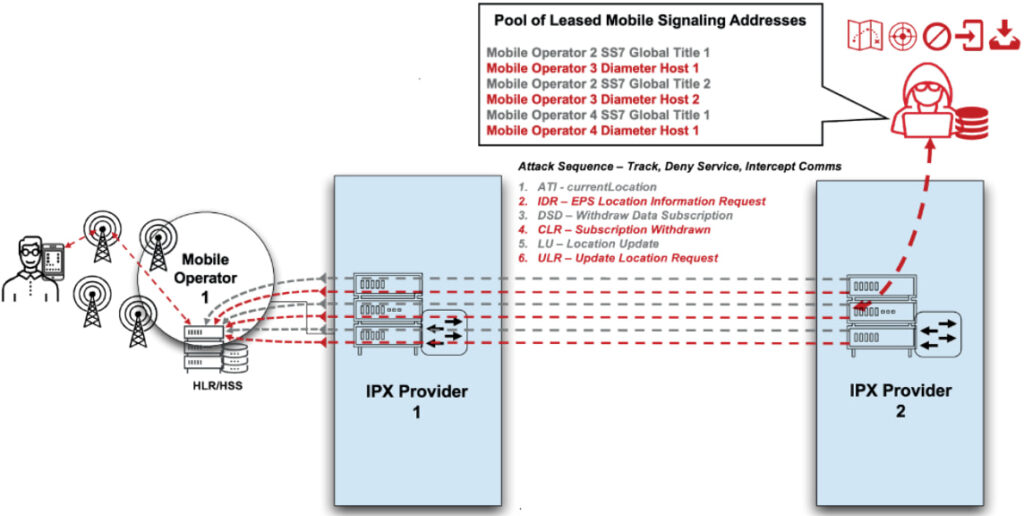
- Active Signaling Attacks: Adversaries inject commands into the mobile signaling backbone to track users, intercept communications, or deny service. Techniques include SS7 and Diameter protocol exploitation, such as anyTimeInterrogation for location tracking or deleteSubscriberData for disruption.
- Malware Distribution: Through network reconnaissance and control, attackers can deploy spyware via SMS phishing or silent over-the-air (OTA) commands, often bypassing firewall detection using leased foreign signaling addresses.
iVerify
The U.S. FCC has already designated CMI and China Telecom as threats to national security. Yet despite this designation, many foreign operators — sometimes unknowingly — continue to route sensitive user data through Chinese-controlled infrastructure due to global roaming agreements and IPX dependencies.
This situation highlights a structural flaw in the global telecom system: the assumption that interconnect networks are inherently secure. Legacy protocols such as SS7 and Diameter, designed decades ago without encryption, were never built for the modern threat landscape. Combined with opaque leasing of signaling addresses to third parties, the result is a fragile and easily exploited mobile infrastructure.







Leave a Reply