
Despite mounting sanctions, legal pressure, and international outrage, commercial spyware vendors are thriving, using stealth infrastructure, corporate rebranding, and legal grey zones to continue arming governments with tools for covert surveillance.
A new report by Sekoia.io reveals that the global spyware market has not only survived years of scandals and investigations, but continues to grow in both revenue and complexity. The research traces how private surveillance companies, often branded as lawful intelligence providers, have built a resilient industry supplying tools to regimes accused of human rights abuses.
The findings show that companies behind spyware such as Predator, Pegasus, Graphite, and DevilsTongue have routinely circumvented export controls and regulatory oversight, while governments, including some in the EU and the United States, continue to procure or tolerate their use.
Failure of export controls
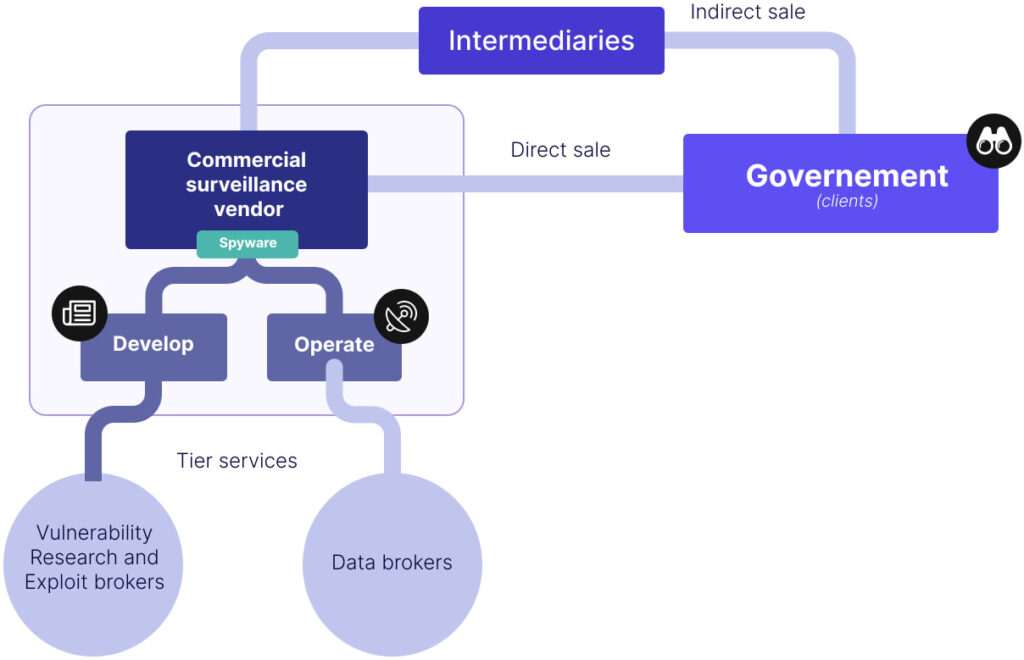
Sekoia provides evidence that, rather than diminishing under regulatory scrutiny, commercial surveillance vendors (CSVs) have adapted through opaque corporate restructuring, offshore entities, and partnerships with intermediaries.
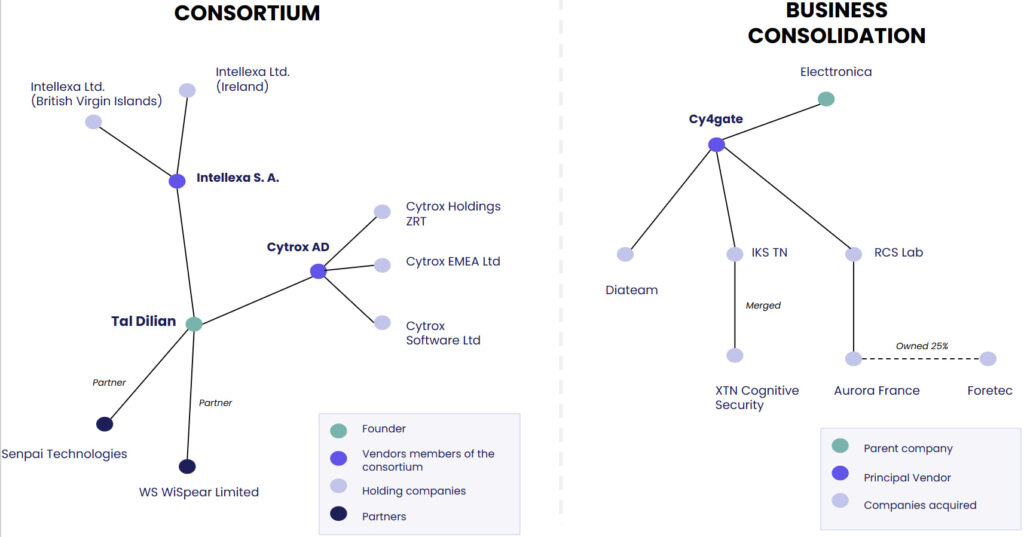
Predator, the mobile spyware developed by Cytrox and sold by the Intellexa consortium, remains operational despite being sanctioned by the US in 2023. Sekoia’s threat intelligence team identified five layers of infrastructure supporting Predator deployments in 2025, including servers owned by FoxItech s.r.o., a Czech company with links to Intellexa’s financial network. This tiered architecture is designed to obfuscate operator identity and evade attribution.
Sekoia
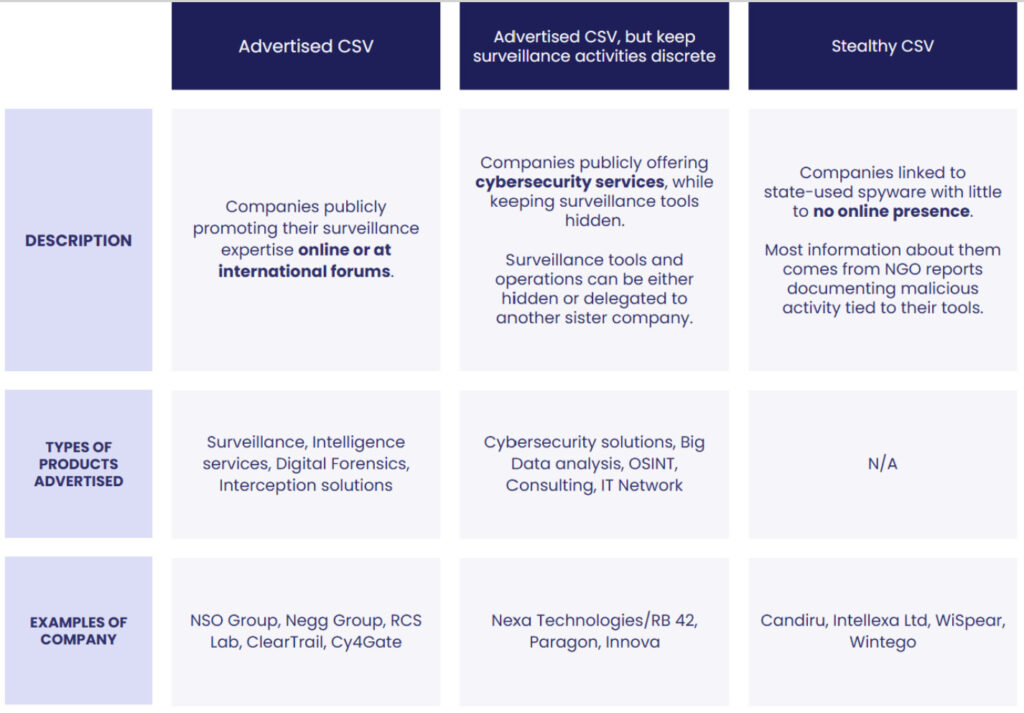
Meanwhile, firms like Nexa Technologies and Candiru have reemerged under new names after previous scandals. Some of these entities continue to do business with states previously flagged for abuse, according to Sekoia’s data.
The report also references corporate forums like ISS World, a surveillance industry trade show that explicitly bars journalists and NGOs from attending. Events like these serve as a marketplace for spyware vendors and government buyers, with past participants including NSO Group, Voyager Labs, RCS, and Paragon, many of which have been directly implicated in unlawful surveillance operations.
A billion-euro industry
While most vendors avoid public pricing, internal leaks have offered a rare glimpse into the economics of spyware:
- Predator (Intellexa): €8 million to monitor 100 devices
- Graphite (Paragon): Multi-million-dollar contracts with U.S. law enforcement
- DevilsTongue (Candiru): €6 million per deployment
- Remote Control System (Hacking Team): Nearly €1 million per activation
- FinFisher (Gamma Group): €1,100 per device (as early as 2011)
Sekoia notes that many vendors now operate through holding companies or rebranded subsidiaries, often across jurisdictions with weak export controls. For example, Cy4gate, an Italian firm, expanded its reach by acquiring RCS Lab and French cyber contractor Diateam, giving it access to both surveillance software and defense-sector contracts in France and Italy.
Sekoia
Policy gaps and legal inaction
Governments have generally responded inconsistently to the spyware threat. In the US, the Department of Commerce has blacklisted NSO Group, Candiru, and Intellexa, while courts have imposed financial penalties, including a $167 million ruling against NSO Group in May 2025 for exploiting WhatsApp.
In Europe, however, the response is fragmented. Some EU institutions have funded surveillance tech abroad without robust safeguards. Others, like Italy and Greece, are themselves accused of spyware abuse, undermining efforts to craft unified regulation.
Export controls remain porous. Many spyware firms circumvent restrictions by operating through shell companies in Cyprus, Bulgaria, or the UAE. Others rely on intermediaries to manage licensing and distribution. In 2021, for example, Swiss-based Toru Group facilitated Predator sales to Bangladesh via the Intellexa-linked firm Passitora.
Sekoia
Mobile still the prime target
Sekoia also dives into the technical mechanics of CSV malware, noting a strong focus on mobile platforms. Whether via malicious links (1-click), invisible payloads (0-click), or physical access (e.g., during border searches), modern spyware is designed to be silent, persistent, and highly evasive.
Sekoia confirms that advanced vendors now explore non-traditional attack surfaces like Wi-Fi, Bluetooth, and baseband vulnerabilities. Once inside a device, spyware often communicates with encrypted, multi-hop command-and-control infrastructures, making detection nearly impossible for non-experts.
Defensive measures
While detection remains difficult, there are several practical strategies users can follow to protect themselves from spyware attacks. These include rebooting their device frequently, enabling Lockdown Mode on iOS and Advanced Protection on Android, and avoiding clicking unsolicited links. When traveling or working on sensitive issues or in high-risk areas, consider using a burner phone.
Sekoia urges journalists, activists, and civil society members to stay informed and report suspected targeting. They can also inspect their devices using tools like Sysdiagnose (Apple), MVT (Amnesty), or SpyGuard (Sekoia).







Leave a Reply