
France’s national cybersecurity agency, ANSSI, has published a detailed report confirming that the Russian military intelligence unit GRU — operating through its cyber-espionage arm APT28 — has conducted a sustained campaign of cyber intrusions targeting French government institutions and critical sectors since at least 2021.
This revelation adds weight to France's recent accusation at the UN, escalating diplomatic tensions with Moscow, which has rejected the claims as “unfounded.”
The report by ANSSI documents how APT28, also known as Fancy Bear, Sednit, or UAC-0028, has exploited French and European entities using a range of evolving attack techniques. These include zero-day exploits like CVE-2023-23397 in Microsoft Outlook, brute-force attacks on webmail systems, and phishing campaigns leveraging compromised edge devices such as routers and VPN gateways.
APT28, active since at least 2004 and attributed to the GRU, has historically focused on military, defense, media, and energy sectors in NATO countries. Since Russia's 2022 invasion of Ukraine, the group has increased its espionage activities, extending its scope to include government ministries, think tanks, research institutes, and aerospace and defense contractors across Europe. In France, the attackers have specifically targeted ministerial departments, local administrations, and the nation’s Defense Technological and Industrial Base (DTIB).
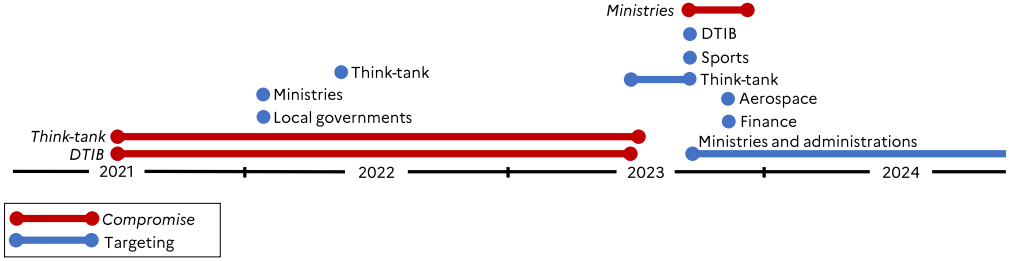
ANSSI
Technical analysis by ANSSI revealed a variety of infection chains. Some campaigns used phishing emails that redirected users to malicious ZIP files hosted on free web services like InfinityFree, deploying malware such as the HeadLace backdoor. In other operations, attackers leveraged services like Mocky.IO for command and control, used IMAP protocol exploits via the OceanMap stealer, or redirected users of UKR.NET and Yahoo to fake login pages designed to harvest credentials.
A particularly notable campaign involved persistent targeting of Roundcube email servers, aiming to exfiltrate sensitive communications and expand reconnaissance. In several incidents, no attempt was made to maintain long-term access, suggesting a focus on quickly extracting specific intelligence rather than establishing persistent footholds.
France’s recent accusations at the UN Security Council were made by Digital Minister Jean-Noël Barrot, who highlighted APT28’s links to attacks not only on Macron’s 2017 election campaign but also on Olympic organizations tied to the upcoming Paris 2024 games. The statement aligns with broader European concern, as Poland, Germany, and the Czech Republic have all issued alerts in early May 2024 regarding similar attacks on their government infrastructure.
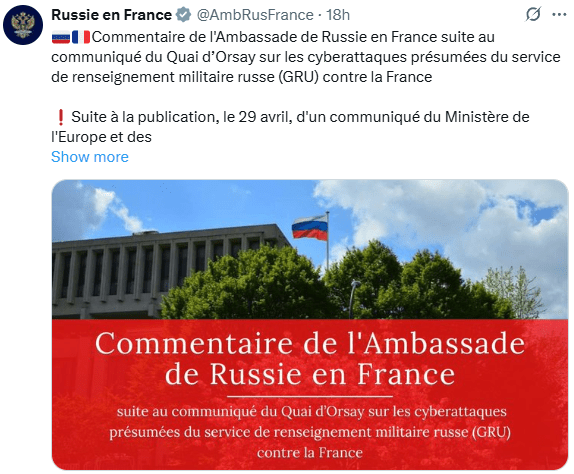
Russia has dismissed these claims as politically motivated, asserting via its embassy in France that the allegations are baseless. Nonetheless, the consistency of forensic data across multiple nations, corroborated by both public and private sector cybersecurity experts, paints the picture of a coordinated GRU cyber-espionage strategy.







Leave a Reply