
CYFIRMA has exposed a new SpyNote malware variant that impersonates Avast Mobile Security for Android, leveraging its trusted branding to lure unsuspecting users.
Distributed via phishing sites designed to resemble Avast's official website, SpyNote disguises itself as “Avastavv.apk,” complete with a fake Avast icon and branding. Once installed, this malware not only deceives users into granting extensive permissions but also gains deep control over their devices to conduct data theft, surveillance, and more. This latest iteration of SpyNote reflects a notable shift in the malware's tactics, as it now exploits a well-known antivirus brand to maximize its reach and credibility among potential victims.
Avast impersonation strategy
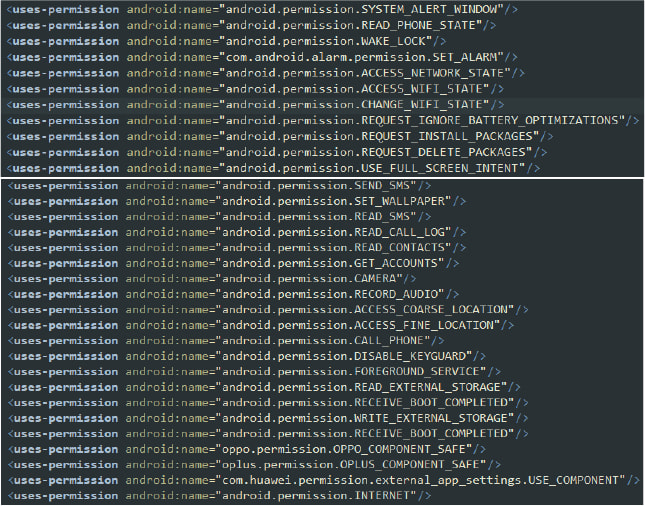
In this campaign, the malicious app “Avastavv.apk” is hosted on phishing domains resembling the legitimate Avast website. Users who download it are tricked into believing they are installing a genuine antivirus, even as the app prompts them for Accessibility Service permissions to operate effectively. This disguise is convincing enough to bypass users' initial security concerns and leads them to unknowingly grant the malware elevated privileges. As a result:
- SpyNote can silently grant itself further permissions, including camera and microphone access, by simulating user gestures in the background.
- It shows notifications suggesting a “system update,” which, when tapped, redirects users to settings related to the malware rather than genuine updates.
- The malware actively prevents users from removing it by intercepting interactions with app settings and redirecting users to the home screen.
CYFIRMA
This campaign departs from previous SpyNote tactics that used more generic app disguises. By posing as a trusted antivirus, SpyNote is likely to capture a wider audience, as users generally trust established security brands and may not suspect malicious intent from a branded app.

CYFIRMA
The phishing sites are carefully designed to mirror legitimate antivirus download portals, with options to download “Avast” for multiple platforms. Clicking on the Android download link installs SpyNote, while the desktop version of the website downloads AnyDesk, a legitimate remote desktop tool, suggesting the campaign might extend to remote access on other devices as well. CYFIRMA has identified at least 14 domains associated with this campaign:
- avastop[.]com
- avastxo[.]com
- avastbk[.]com
- avastpx[.]com
- avastcsw[.]com
- avastsf[.]com
- avastsp[.]com
- avastpy[.]com
- avastwp[.]com
- avastkb[.]com
- avastxv[.]com
- avastga[.]com
- avastsgp[.]com
- avastpst[.]com
CYFIRMA
Advanced capabilities and evolution
SpyNote includes extensive data-collection tools and defense mechanisms, allowing it to remain undetected and persist on devices. This version of SpyNote is capable of:
- Checking for an active internet connection and continuously attemptıng to connect to its command-and-control (C2) server at 45.94.31[.]96 to send exfiltrated data.
- Capturing images, recording audio, and intercepting messages across apps like WhatsApp, Instagram, and Facebook, making it effective for both personal data theft and financial fraud.
- Targeting popular crypto wallets, including Trust Wallet and Binance, to capture sensitive information like wallet balances and transaction details.
Compared to earlier versions documented by ThreatFabric in 2022, SpyNote has evolved significantly in its techniques and target profile. While previous iterations relied on more generic app disguises and targeted financial data broadly, this version takes advantage of Avast's brand to increase its perceived legitimacy. It also includes more advanced obfuscation techniques, tailored device compatibility across major Android brands like Samsung, Huawei, and Oppo, and heightened focus on cryptocurrency data — a shift likely driven by the rising value of digital assets.
To protect against this deceptive campaign, users should be vigilant about downloading apps exclusively from Google Play and avoid APK files from external sites. Moreover, it's advised to check installed apps and granted permissions periodically to identify suspicious entries.







Leave a Reply