
The Everest ransomware gang has posted over 120 GB of medical data on two file hosting platforms for anyone to download for free.
The leaked files were allegedly stolen during a ransomware attack against a third-party doing business with MultiCare Health System, a Washington-based not-for-profit healthcare organization that operates eight hospitals and medical centers in the U.S.
Last week, the organization announced that one of its third-party service providers, Kaye-Smith, who prints forms for MultiCare, has suffered a ransomware attack that impacted current and former employees of the organization.
Everest claims the leaked data set includes 37,000 distinct medical documents, with 23,195 of them being detailed medical records. Also, 4,437 documents are medical records of clients of DeVero, a medical services management suite used in hospitals.
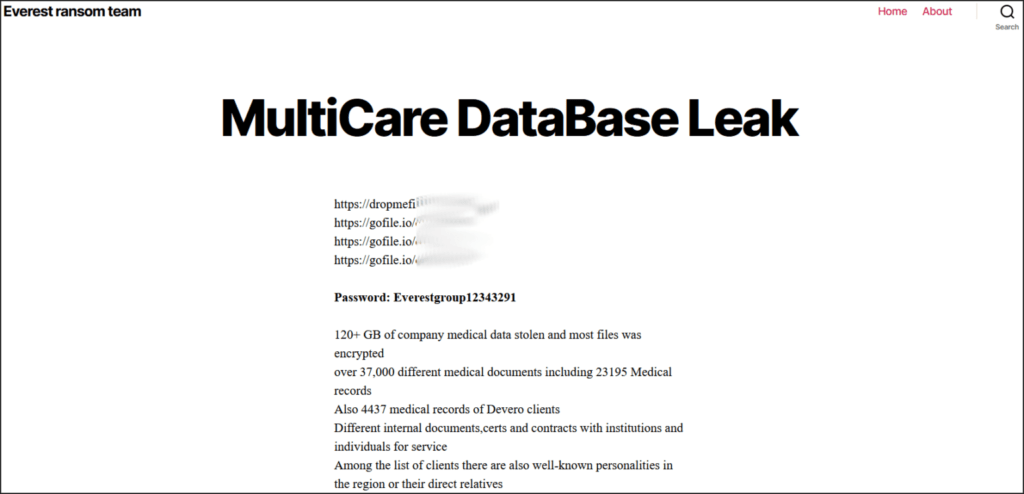
Other files in the leaked set include internal financial documents, certificates, contracts with institutions, contracts with service providers, etc.
Cyber Insider has confirmed the download links are up, so the dataset is available to anyone with the URLs at the time of writing.
MultiCare has not confirmed the authenticity of the data yet, but we have contacted the organization to clarify that point and still waiting for their response.
Previous Incident
Everest's claims about holding data of MultiCare customers don't match the recently disclosed security incident that, according to the organization, impacted only employees.
However, it matches a previous security incident that concerns a different third-party that was breached at the beginning of the year.
On August 10, 2022, and after the conclusion of the relevant investigations, MultiCare announced that one of its third-party service providers, Avamere Health Services LLC, suffered a data breach.
Reportedly, a network intruder gained unauthorized access to Avamere's IT systems, where sensitive MultiCare customer data was held.
MultiCare found that roughly 18,615 beneficiaries of its medical program might have been compromised as a result of the security incident, with potentially stolen data including full names, diagnosis and conditions, dates of service, and medical service provider details.
Everest ransomware might have gotten this data set from a different hacker group and used it to extort MultiCare and persuade them to pay a ransom.
From the result, which is to leak the data for free, it appears that the extortion has failed, and MultiCare refused to meet the blackmailers' demands.
Another possibility is that Everest uses data from the more recent breach, but they didn't recognize what kind of data it is, wrongfully deducing it belongs to customers of MultiCare.
Alternatively, Everest might be purposefully creating turbulence by claiming that the set contains customer data to raise the heat for the victimized organization.
The alleged medical records number is very close to the number of people working for MultiCare, so there's a possibility that the threat actors are simply wrong or lying about the data type.







Good for MultiCare that they didn’t cave in to the demands of these snakes!