
The Everest ransomware group has claimed responsibility for a cyberattack on Mediclinic, a global hospital operator with $5.4 billion in revenue, threatening to leak stolen internal data and employee records unless its ransom demands are met.
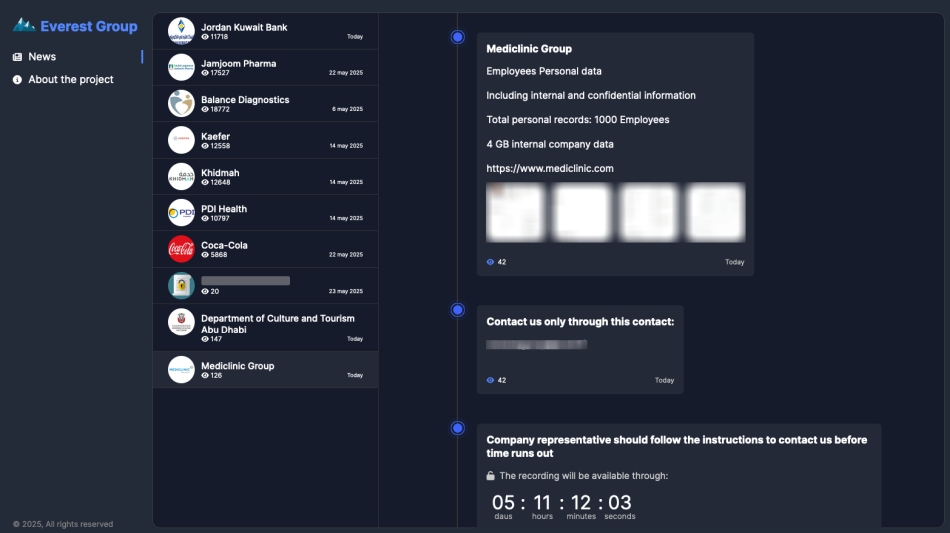
Mediclinic, which operates healthcare facilities across Switzerland, South Africa, the UAE, and Namibia, was recently listed as a victim on the Everest ransomware gang’s dark web leak site. The group claims to have exfiltrated 4GB of internal documents and the personal data of 1,000 employees, giving the company five days to negotiate before publicly releasing the stolen files.
The cyberattack has reportedly disrupted operations across multiple facilities, including temporary downtime in patient-facing platforms and internal communications systems. While clinical services remain operational, the full extent of the breach is still under investigation.
Stolen employee data and confidential files
Cybernews
Everest’s data dump allegedly includes internal company files and sensitive employee information. Though it's not yet clear whether patient data was accessed, cybersecurity experts warn the breach could have serious consequences for data privacy and trust. Such data could be used for identity theft, phishing, or even to launch secondary attacks against Mediclinic's infrastructure.
Everest’s tactic follows a common “double extortion” model, where attackers exfiltrate data before encrypting files, then threaten to release it publicly to increase pressure on victims. According to Cybernews, the gang has listed 248 victims since 2023.
Mediclinic investigating, attackers escalate
According to the Moxso blog, Mediclinic has launched a formal investigation with the help of cybersecurity professionals and legal advisors. The company is reviewing compromised systems, checking for unauthorized access, and notifying relevant regulatory bodies.
Meanwhile, Everest has published what appear to be internal documents on its leak site to support its claims. The group has previously targeted major organizations such as Coca-Cola and AT&T, and is known for exploiting remote desktop vulnerabilities and stolen credentials to gain access to networks.
The ransomware group operates under a ransomware-as-a-service (RaaS) model, allowing affiliates to use Everest's malware toolkit in exchange for a cut of ransom payments.
Healthcare remains a prime target
This incident underscores the increasing pressure faced by healthcare providers, who remain attractive targets due to the value of their data and the critical nature of their operations. In recent years, ransomware attacks have hit several major healthcare providers, including Change Healthcare and HCA Healthcare.
“Ransomware groups understand that any delay in restoring access can affect patient care, increasing the pressure on victims to pay,” noted cybersecurity analysts.
Hospitals and clinics often rely on legacy systems and complex networks, making them particularly vulnerable. Once inside, attackers can move laterally across systems to access backups, patient records, and internal documents.
Consequences and compliance risks
Beyond operational disruption, the breach could have severe legal and financial consequences for Mediclinic. If patient data was exposed, the company may face regulatory scrutiny and fines under data protection laws such as South Africa’s POPIA or the UAE's Data Protection Law.
Affected individuals — including employees and potentially patients — may also require notification, credit monitoring services, and other remediation support.
Mediclinic has not indicated whether it intends to negotiate with the attackers or pay the ransom.
Strengthening defences
It is imperative for healthcare organizations to improve cybersecurity defenses, including implementing strong authentication, network segmentation, regular backups, and staff training. A robust and tested incident response plan is critical to containing damage during attacks.
The Mediclinic breach is a reminder that cybersecurity is not just an IT concern, but a fundamental part of patient safety, data privacy, and public trust.







Leave a Reply