
Europol has coordinated an international operation to dismantle infrastructure related to the illicit use of Cobalt Strike, a legitimate cybersecurity tool often exploited by cybercriminals.
In a significant move against cybercrime, Europol has coordinated a global operation to counter the misuse of the Cobalt Strike cybersecurity tool by criminal entities. The operation, conducted between June 24 and June 28, involved law enforcement agencies from multiple countries and aimed to disable unlicensed versions of Cobalt Strike used by cybercriminals to infiltrate IT systems.
Cobalt Strike abuse
Cobalt Strike, developed by Fortra, is a commercial tool used by legitimate cybersecurity experts to simulate cyberattacks and identify vulnerabilities in security systems. However, older, unlicensed versions of the tool have been stolen and cracked by cybercriminals, providing them with a powerful means to deploy malware and gain unauthorized access to systems. These unlicensed copies have been linked to major malware and ransomware operations, including those involving RYUK, Trickbot, and Conti.
Fortra has actively collaborated with law enforcement agencies to combat this misuse, but the persistent theft and cracking of its software highlight ongoing challenges. The takedown of criminal infrastructure utilizing Cobalt Strike disrupts the operations of threat actors and increases their operational risks.
Operation MORPHEUS
Operation MORPHEUS was spearheaded by the UK National Crime Agency (NCA) and included contributions from law enforcement bodies in Australia, Canada, Germany, the Netherlands, Poland, and the United States.
During the operation, known IP addresses and domains associated with criminal activity were flagged to online service providers. A total of 690 IP addresses in 27 countries were identified, leading to the takedown of 593 by the end of the action week. This effort marks the culmination of a complex investigation aimed at disrupting the infrastructure that supports cybercriminals' activities.
The success of this operation relied heavily on cooperation with the private sector. Companies such as BAE Systems Digital Intelligence, Trellix, Spamhaus, abuse.ch, and The Shadowserver Foundation provided essential support through enhanced scanning, telemetry, and analytical capabilities. This public-private partnership enabled the identification and disruption of malicious activities more effectively.
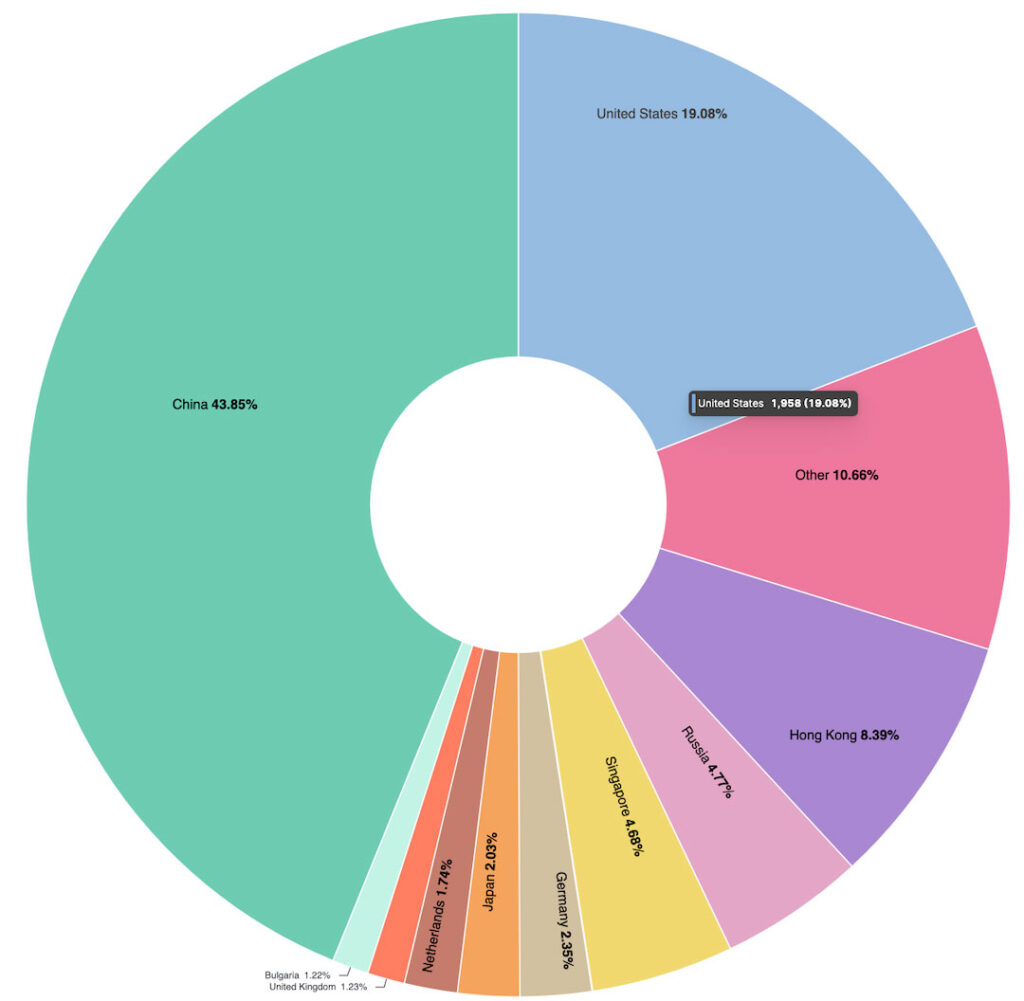
Trellix
Trellix, in particular, played a pivotal role by providing extensive threat intelligence and analysis. Over the course of the two-year investigation, Trellix identified over 12,000 unique Cobalt Strike server instances and contributed valuable data that helped law enforcement pinpoint criminal infrastructure.
Despite the significant progress made during Operation MORPHEUS, the battle against the misuse of Cobalt Strike is far from over. Law enforcement agencies will continue to monitor and disrupt criminal activities involving the tool.







Leave a Reply