
ETH Zurich spin-off Soverli has introduced a groundbreaking smartphone architecture that uses isolated “domains” to grant users unprecedented control over their data and device resources, fundamentally reshaping mobile security.
The new architecture, dubbed TEEtime, stems from years of research at ETH Zurich, transforming the academic work into a commercial platform that promises secure, domain-based separation on smartphones, breaking from the traditional, monolithic operating system model.
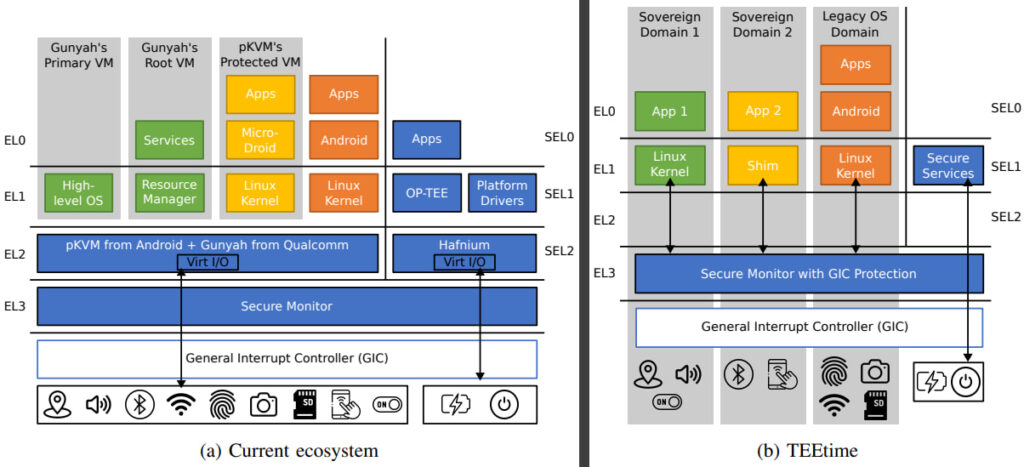
At the core of TEEtime is the ability to create sealed-off areas, or domains, on a smartphone that run independently of each other and of the main OS. Each domain has its own isolated memory, hardware access, and sensor controls. Crucially, switching between these domains occurs through a custom controller developed at ETH, which operates independently of the operating system, thereby minimizing the attack surface and maximizing trust.
This architectural shift addresses a long-standing flaw in smartphone security, which is the centralized, bloated nature of modern OS environments. With millions of lines of code, traditional mobile OSs represent large and vulnerable targets. TEEtime counters this by keeping the controller's source code minimal and auditable, limiting trust requirements to the firmware layer and eliminating the need to rely on manufacturers' closed-source hypervisors or trusted execution environments (TEEs) like TrustZone.
The spin-off's offering is especially relevant for government bodies, emergency services, and corporate clients, who require high-assurance isolation for sensitive operations such as crisis communication, secure messaging, or handling classified information. For example, emergency responders could operate a domain connected to a dedicated emergency network, entirely isolated from consumer apps and services.
ETH Zurich
Soverli's approach fundamentally redefines smartphone privilege hierarchies. In contrast to conventional systems, where hardware control is layered with manufacturers at the top and users at the bottom, TEEtime places the user in complete control, allowing them to define which domains have access to which peripherals and when. This extends to sensors, displays, fingerprint readers, and even network modules.
Each domain can:
- Run its own apps or OS variant
- Access selected hardware components directly without virtualization
- Protect its code and data from all other domains, including the main OS
This is made possible through TEEtime's interrupt isolation and memory protection mechanisms, based on the Armv8-A architecture and the Arm Generic Interrupt Controller (GIC). Unlike existing solutions, TEEtime avoids hypervisors entirely. Instead, it uses a custom secure monitor that configures access dynamically at runtime, ensuring peripherals and their interrupts are only accessible to authorized domains.
The architecture is also designed to be backward-compatible. Soverli demonstrated the system running multiple domains alongside a full Linux-based legacy OS, with practical use cases including secure messaging apps that bypass OS-level surveillance, biometric authentication modules isolated from third-party apps, and VPN clients with dedicated hardware access.
Although Soverli is currently targeting enterprise and institutional partners through software licensing and pre-installed hardware, the founders haven't ruled out expanding into the consumer market. “Awareness that we shouldn't be as dependent on the big tech companies is growing by the day,” Puddu noted in the ETH announcement.
Their academic paper on TEEtime is scheduled for presentation at a major cryptographic hardware conference in October 2026, underscoring the technical significance of the innovation.







Leave a Reply