
A newly observed phishing campaign is impersonating urgent Zoom meetings to trick users into handing over their corporate login credentials.
The attack uses realistic visuals, pre-filled login forms, and a faked connection timeout to dupe victims into entering sensitive information.
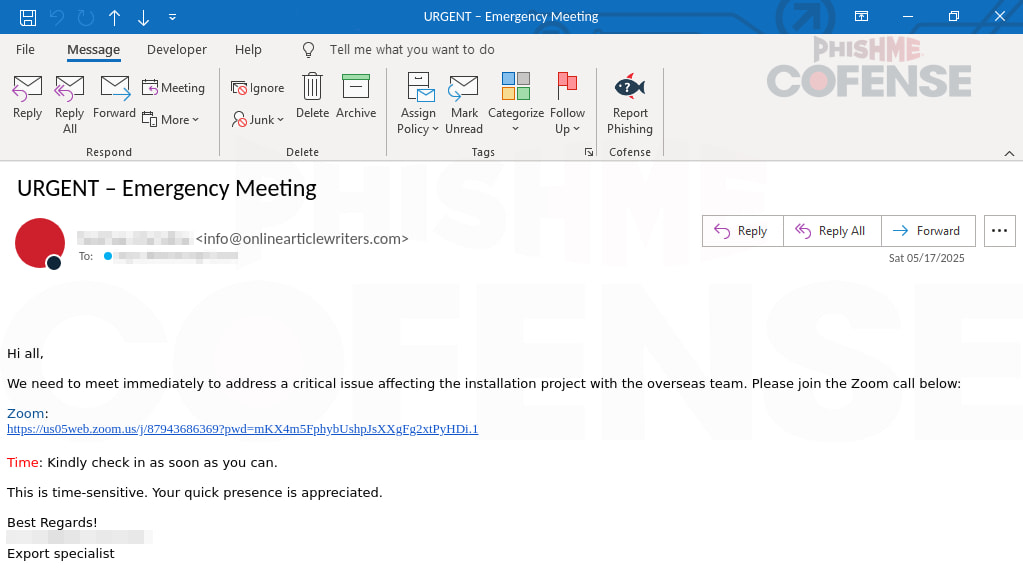
The threat was discovered and analyzed by the Cofense Phishing Defense Center (PDC). According to them, the campaign leverages users’ familiarity with Zoom and their potential anxiety over missing important meetings to bypass skepticism and lure them into credential theft. The emails are titled with urgent subject lines such as “URGENT – Emergency Meeting” and repeatedly use panic-inducing language to prompt quick user action.
The phishing chain begins with a deceptively benign link embedded in the email. The visible text appears to point to a legitimate Zoom meeting, but clicking it first routes users through a Cirrus Insight CRM tracking URL.
Cofense
This tracking URL redirects to a series of masked URLs, ultimately landing the user on a page hosted at: “pub-51656ae3d0ef4f2ba59cdfc6830c8098[.]r2[.]dev/meeting[.]htm”
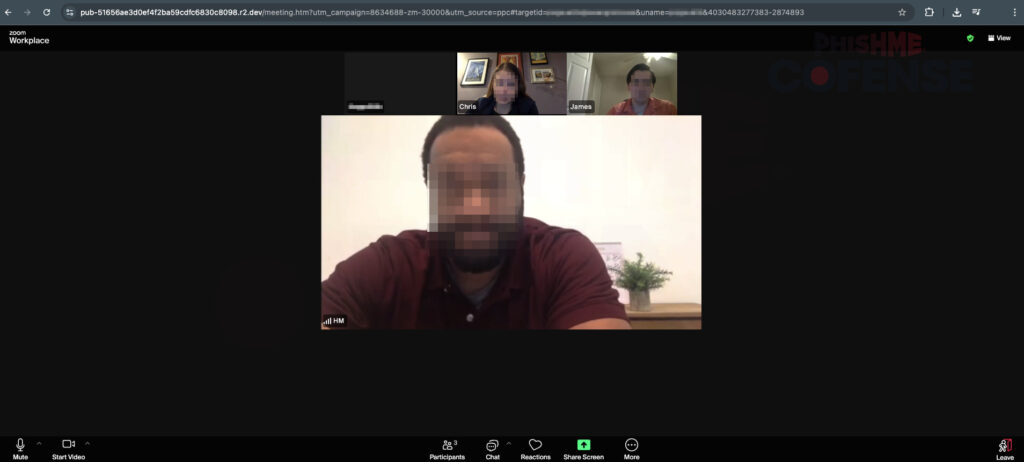
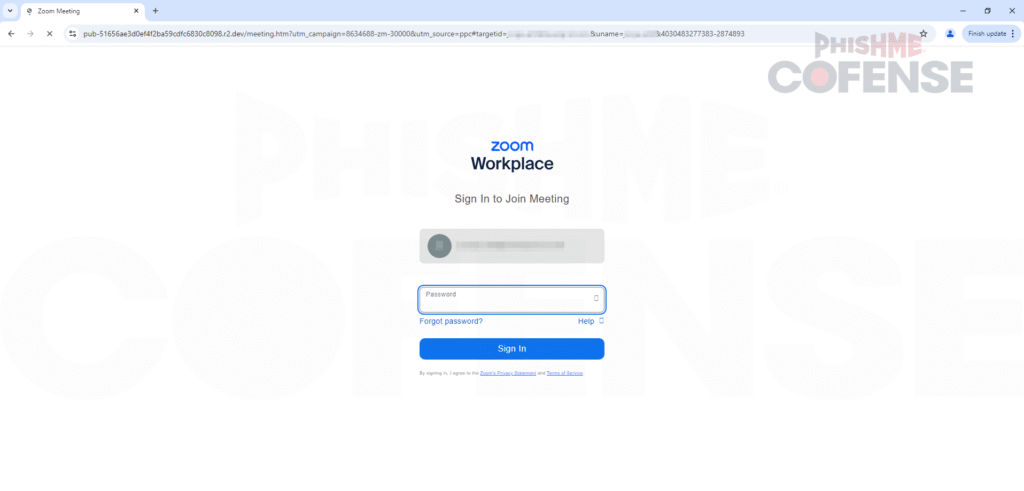
On this fake landing page, users are presented with a simulated Zoom interface that includes avatars and subtle animations, such as a participant waving or reacting to simulate a live environment. The page displays a “joining meeting” message followed by a connection timeout dialog. This message prompts users to re-enter their login credentials into what appears to be a legitimate Zoom Workplace login form.
Cofense
Zoom Workplace is a collaboration platform widely used by enterprises for meetings, messaging, and document sharing. Many organizations tie these credentials into single sign-on (SSO) systems or federated identity platforms, meaning stolen Zoom credentials can serve as entry points into broader enterprise environments.
To further increase believability, the phishing form pre-fills the victim’s email address, extracted from the original phishing URL via parameters like #targetid=john@doe.com. Once the password is entered, the credentials, along with the victim’s IP address, country, and region, are exfiltrated using Telegram’s bot API.
Cofense
Telegram, while popular for its encrypted messaging capabilities, is frequently misused by cybercriminals for command-and-control operations or data exfiltration due to its anonymity and ease of use.
The infrastructure supporting this campaign includes multiple IPs and domains associated with legitimate platforms like Cirrus Insight, Cloudflare R2, and Hubs.ly, which the attackers use for traffic redirection and content hosting. This approach makes detection and filtering more challenging for security solutions relying on simple domain reputation checks.
To defend against these attacks, hover over meeting links before clicking to confirm they’re actual Zoom.us links, inspect landing pages for discrepancies, and use multi-factor authentication on your Zoom account.







Leave a Reply