
Dropbox Sign, previously known as HelloSign, reported a security breach within its production environment. Unauthorized access led to the exposure of sensitive customer data, prompting an immediate and robust response from the company to protect its users and secure its systems.
The breach was first identified by the Dropbox Sign team on April 24th. Upon discovering unauthorized access, an extensive investigation was launched involving industry-leading forensic experts.
The investigation revealed that a sophisticated threat actor had gained access through a compromised service account within Dropbox Sign's backend infrastructure. This account, typically used for running automated services, provided the attacker with extensive capabilities to manipulate the environment and access the customer database.
The data accessed includes customer emails, usernames, phone numbers, hashed passwords, and various authentication details like API keys and OAuth tokens. Importantly, there was no evidence that the contents of customers' documents or payment information were compromised.
Dropbox Sign has taken several immediate actions in response to the breach, including:
- Password Reset: All user passwords have been reset, and users have been logged out of all connected devices to prevent further unauthorized access.
- API and OAuth Token Rotation: Coordinating the rotation of all API keys and OAuth tokens to secure customer accounts from further attacks.
- Notification and Guidance: Impacted users are being contacted with step-by-step instructions on how to protect their data further.
Additionally, Dropbox has reported the incident to data protection regulators and law enforcement agencies to comply with legal obligations and aid in the broader response to the incident.
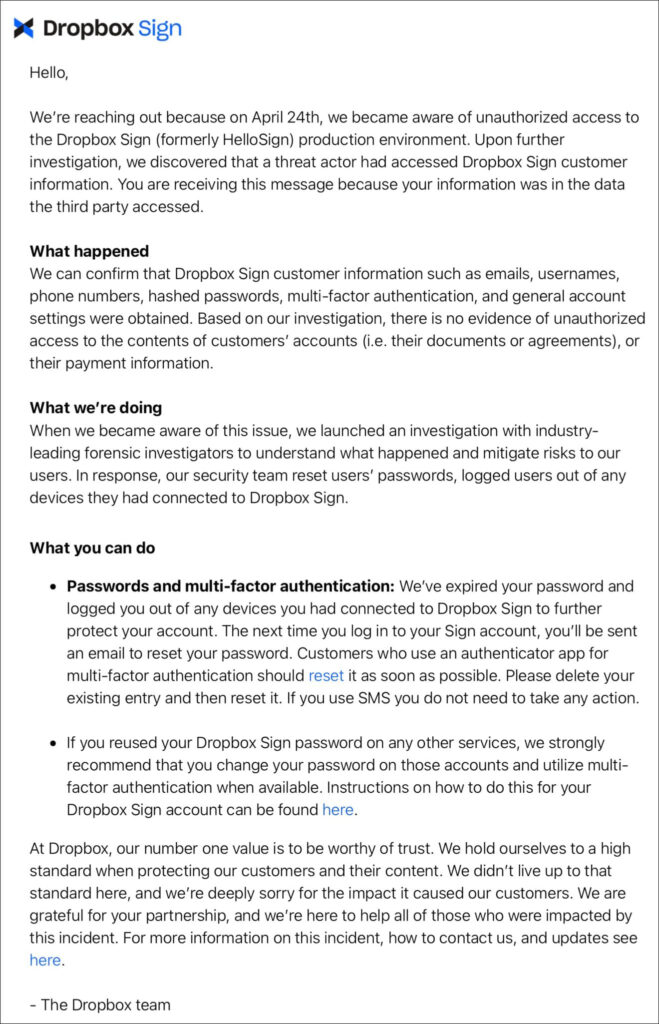
Dropbox emphasizes its commitment to trust and security, acknowledging the breach as a failure to meet their high standards. The company is conducting an extensive review to understand the breach fully and prevent future incidents. They are also updating their security practices and infrastructure based on the findings of their ongoing investigation.
For users, Dropbox Sign recommends the following:
- Reset passwords when prompted upon the next login.
- For API customers, generate new API keys and configure them with their applications.
- Users utilizing authenticator apps for multi-factor authentication should reset their configurations.







Leave a Reply